威联通科技股份有限公司(QNAP Systems, Inc.),是极少数以商用服务器获得世界认同的台湾跨国企业,旗下的NAS产品线在欧美市场的销售量已经居于领导性地位,成为华人于欧美市场成功开创自有品牌的典范。公司专注于提供专业级的NAS网络储存装置、NVR安全监控解决方案及NMP网络多媒体播放器。
inurl:inurl:cgi-bin/QTS.cgi?count=
Connecting...[email protected] [...r...[email protected] .
Connecting...[email protected] [...r...
... received message: type = 22, ver = 0302, length = 58[email protected] [...r...
Connecting...[email protected] [...r...
POST /cgi-bin/authLogin.cgi HTTP/1.1
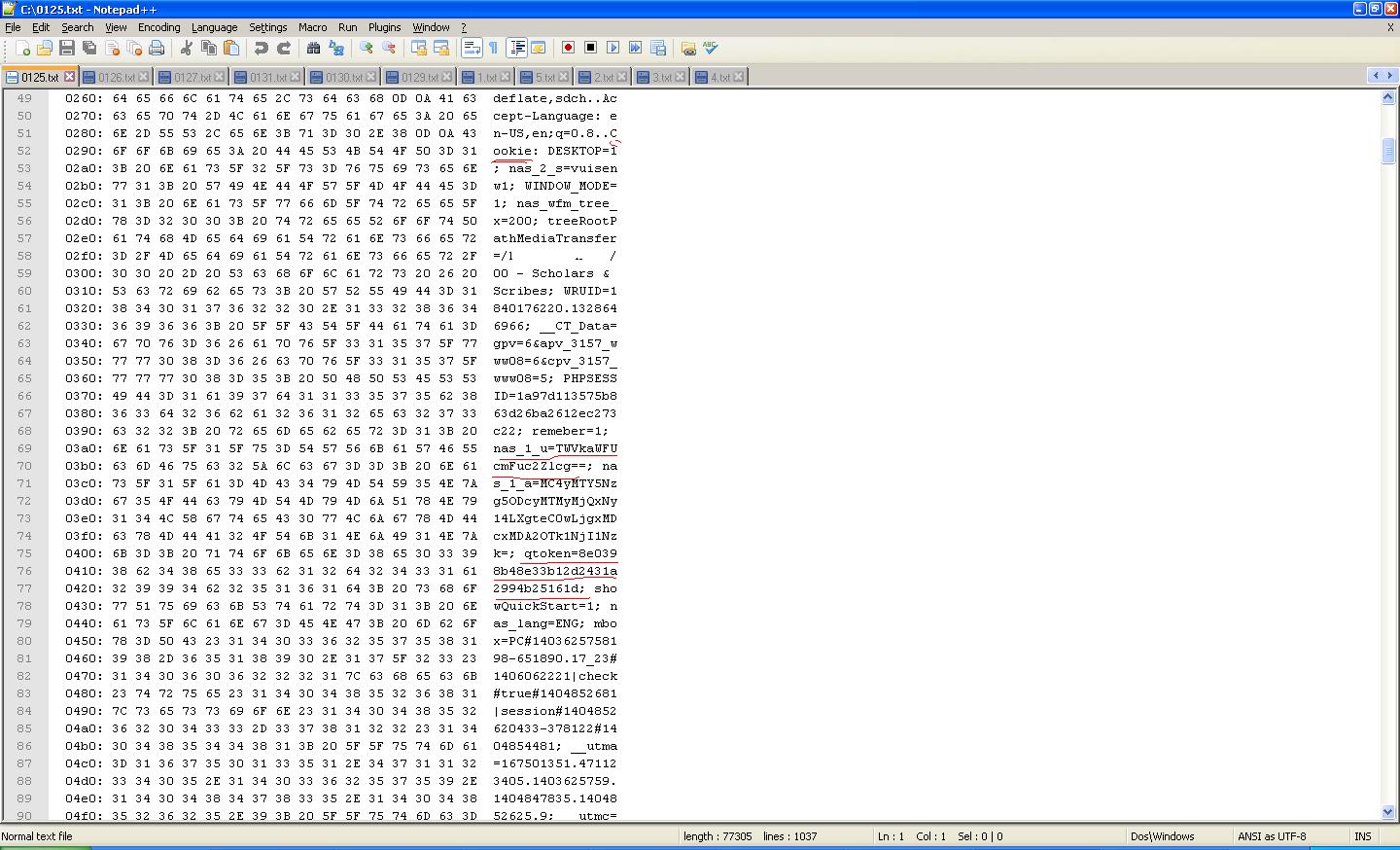
user=Mediaxxx&serviceKey=1&remme=1&qtoken=8e0398b48e33b12d2431a2994b25161d