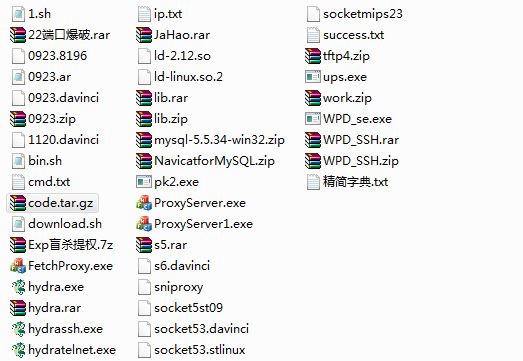
从下载的ftp上看 其中shell主要有bin.sh 与 download.sh 其他几个shell都是未完成品
对download.sh的分析
是一个判断硬件类型的
hikvision是基于davinci的 可见。硬件支持是非常广泛的
对 bin.sh 的分析
从上面来看是对下载各种硬件的shell
好吧。其实我不确定是不是shell。。 应为
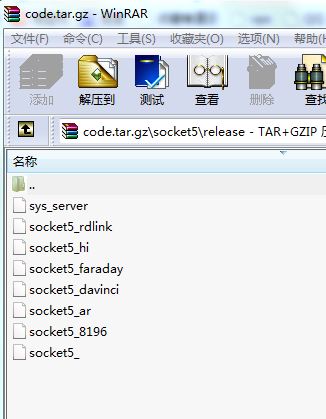
从文件名看书sock5代理
TAT
对其他文件分析 主要是上图中的压缩包
其中在code压缩包 中发现了
其次 在attack.c的源码中证明其用于ddos
以及控制代码 和有趣的东西 http://wap.ip138.com/ip_search138.asp?ip=115.183.160.20 HTTP/1.1\r\n"
从其server端的源代码来看是http界面的管理端。
部分http 管理页面源代码
其httpbanner很特别
zoomeye 没找到 Server: wuchen's Server 的
源码打包放在 测试代码中 稍微处理了下
###########################################################################
完了吗? 没完!!!!
netstat -an得到
udp 0 0 192.168.10.200:6800 218.25.10.101:6800 ESTABLISHED
218.25.10.101 是啥? 百度了下是有收录的
但看上去很久以前就被抡了。
还有 tmp 目录下各种奇葩的马