http://robot.dangdang.com/WebIm/page/officialPortal.jsp
参考: WooYun: 当当网某分站存储型xss漏洞一枚
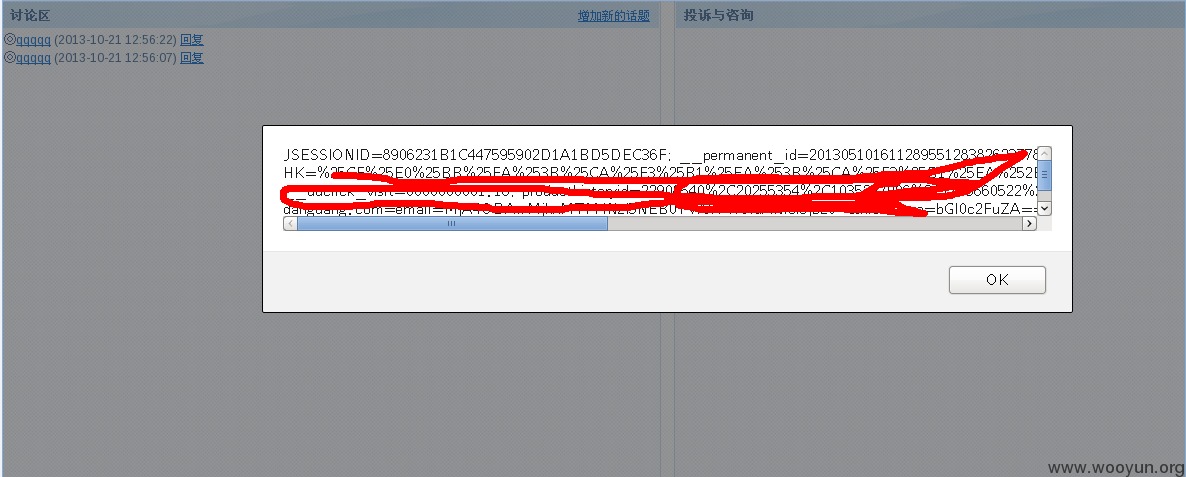
当然,这里已经修复了。不过依然存在问题,可以绕过。感觉这个页面是内部用的,没必要开放访问吧。。
点击增加新的话题,可以添加标题和内容:
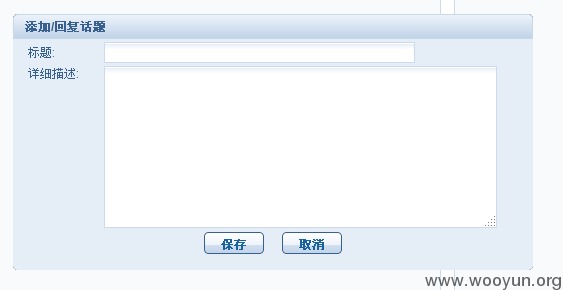
发送如下post请求:
arg参数为传递到服务器的内容。经过分析查询时的返回内容:
发现除了标题和内容,(title,context)外,还会返回多个参数值,比如company_id,sender.而post的参数中恰好也存在这些参数。于是,在post请求中修改sender参数为xss代码。
发送如下请求:
果然没有过滤。