1.后台弱口令
http://acm.pptv.com/ (最新一次检测已修复)
用户名:ejacky 密码:123456
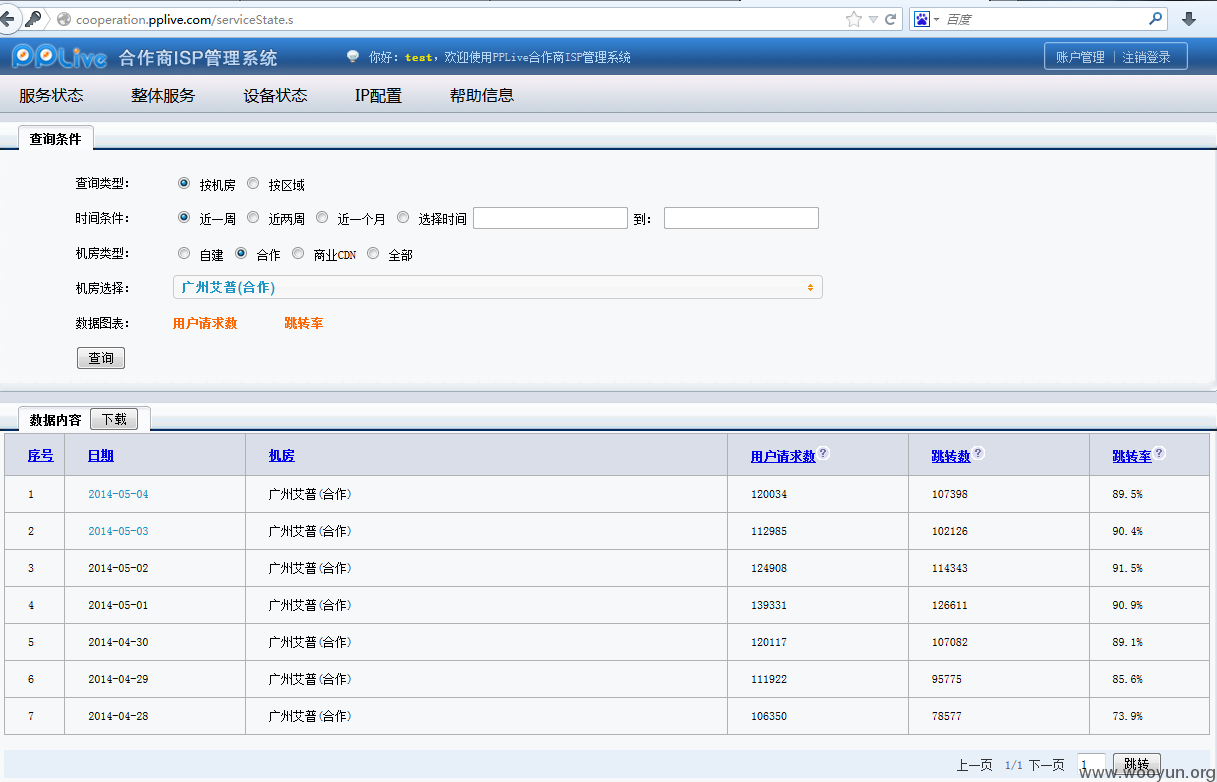
http://cooperation.pplive.com/
用户名:test 密码:123456
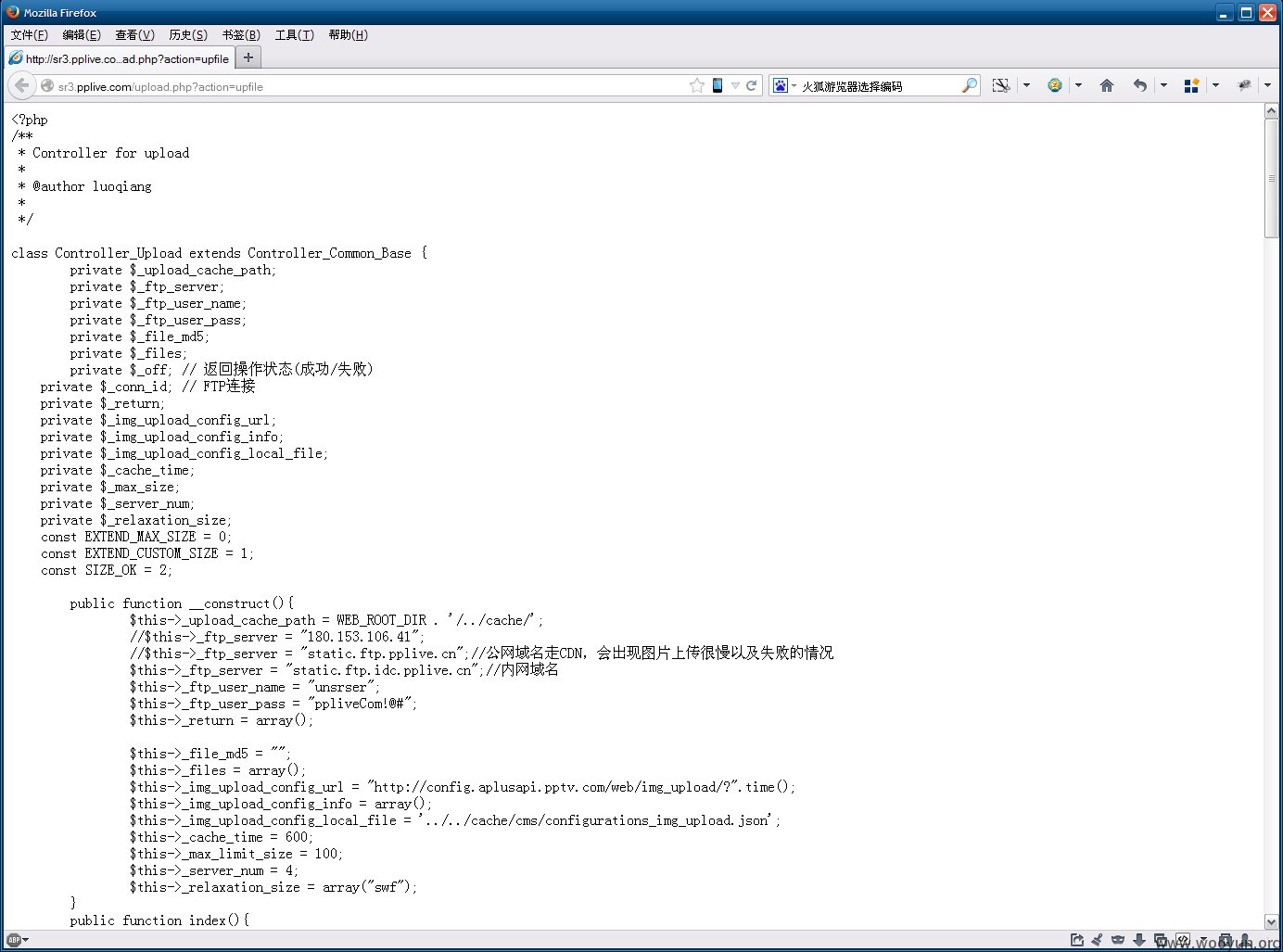
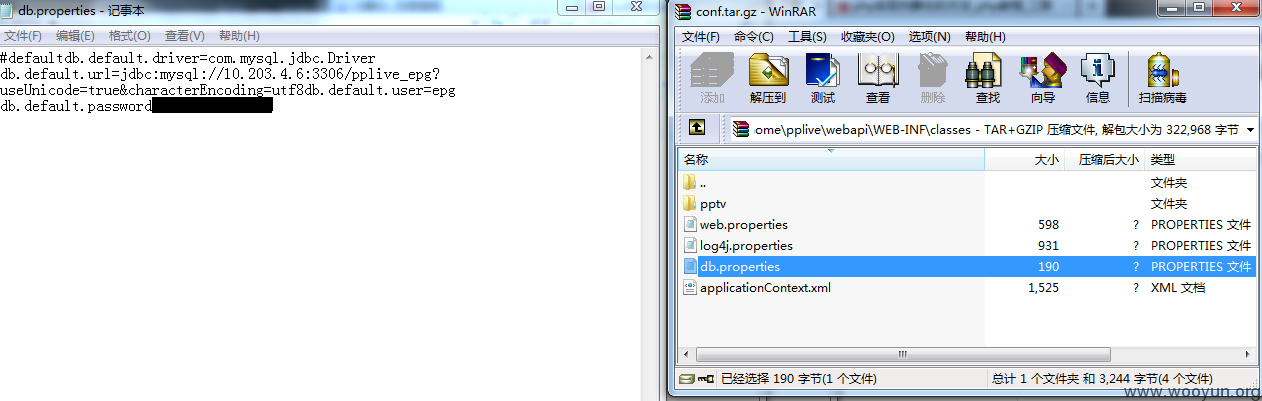
2.配置文件下载
http://sr3.pplive.com/upload.php(已修复)
http://180.153.106.106:8888/conf.tar.gz
http://180.153.106.107:8888/conf.tar.gz
http://180.153.106.26:8888/conf.tar.gz
http://180.105.106.27:8888/conf.tar.gz
(最新一次检测已修复)