漏洞概要
关注数(24)
关注此漏洞
漏洞标题:新浪微博某服务器控制不当(可远程SHELL)
提交时间:2016-04-12 16:06
修复时间:2016-05-28 11:10
公开时间:2016-05-28 11:10
漏洞类型:未授权访问/权限绕过
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2016-04-12: 细节已通知厂商并且等待厂商处理中
2016-04-13: 厂商已经确认,细节仅向厂商公开
2016-04-23: 细节向核心白帽子及相关领域专家公开
2016-05-03: 细节向普通白帽子公开
2016-05-13: 细节向实习白帽子公开
2016-05-28: 细节向公众公开
简要描述:
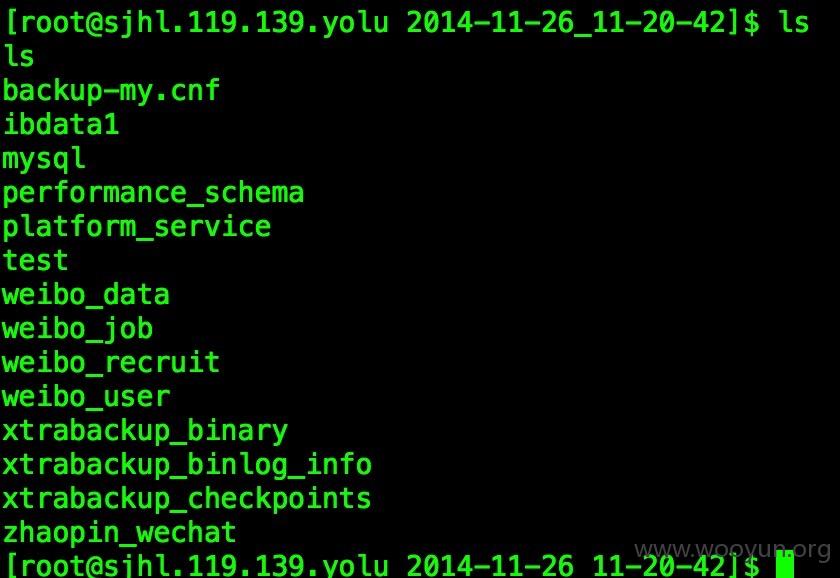
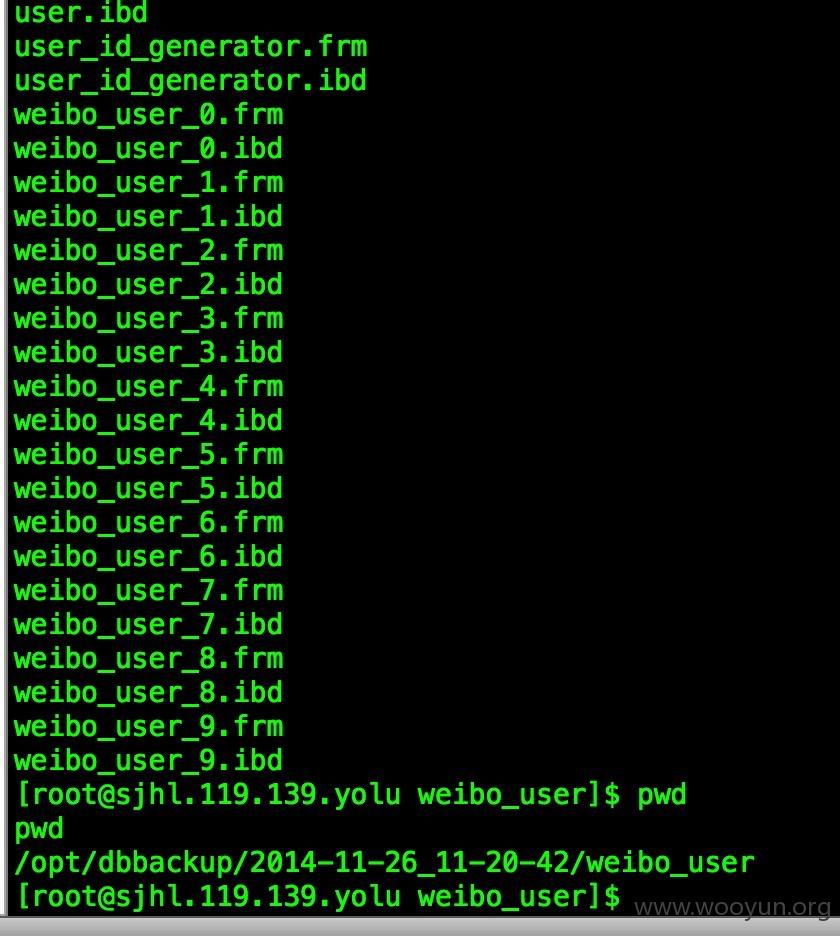
新浪微博某服务器直接弹个SHELL这样,SQL注入就先不发了
看到某个/opt/dbbackup目录里面有个weibo_user, weibo_data的msyql数据库目录,惊呆了
详细说明:
#1 漏洞服务器
zhaopin.weibo.cn
zhaopin.weibo.com
renmai.weibo.com
redis: 59.151.119.139
port: 7377
#2 info
redis-cli -h 59.151.119.139 -p 7377 > info
漏洞证明:
#3 exp get shell
#4 证明
修复方案:
版权声明:转载请注明来源 猪猪侠@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:6
确认时间:2016-04-13 11:03
厂商回复:
感谢关注新浪安全,将通知合作方修复此问题。
最新状态:
暂无




