漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0123363
漏洞标题:窝窝团某服务敏感信息泄漏(可读取程序源码)
相关厂商:窝窝团
漏洞作者: 啊L川
提交时间:2015-06-29 13:39
修复时间:2015-08-13 17:30
公开时间:2015-08-13 17:30
漏洞类型:敏感信息泄露
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-06-29: 细节已通知厂商并且等待厂商处理中
2015-06-29: 厂商已经确认,细节仅向厂商公开
2015-07-09: 细节向核心白帽子及相关领域专家公开
2015-07-19: 细节向普通白帽子公开
2015-07-29: 细节向实习白帽子公开
2015-08-13: 细节向公众公开
简要描述:
RT
详细说明:
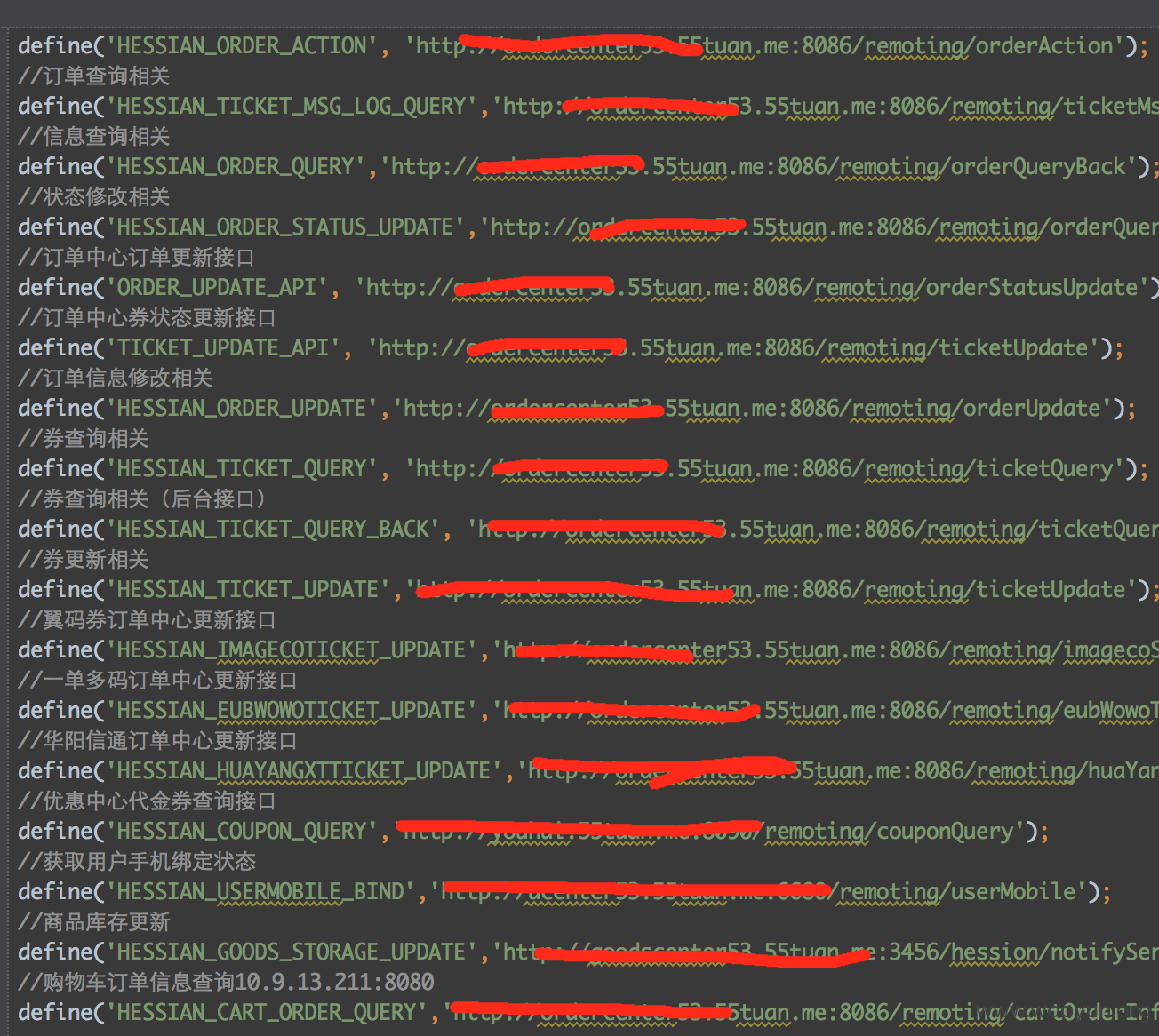
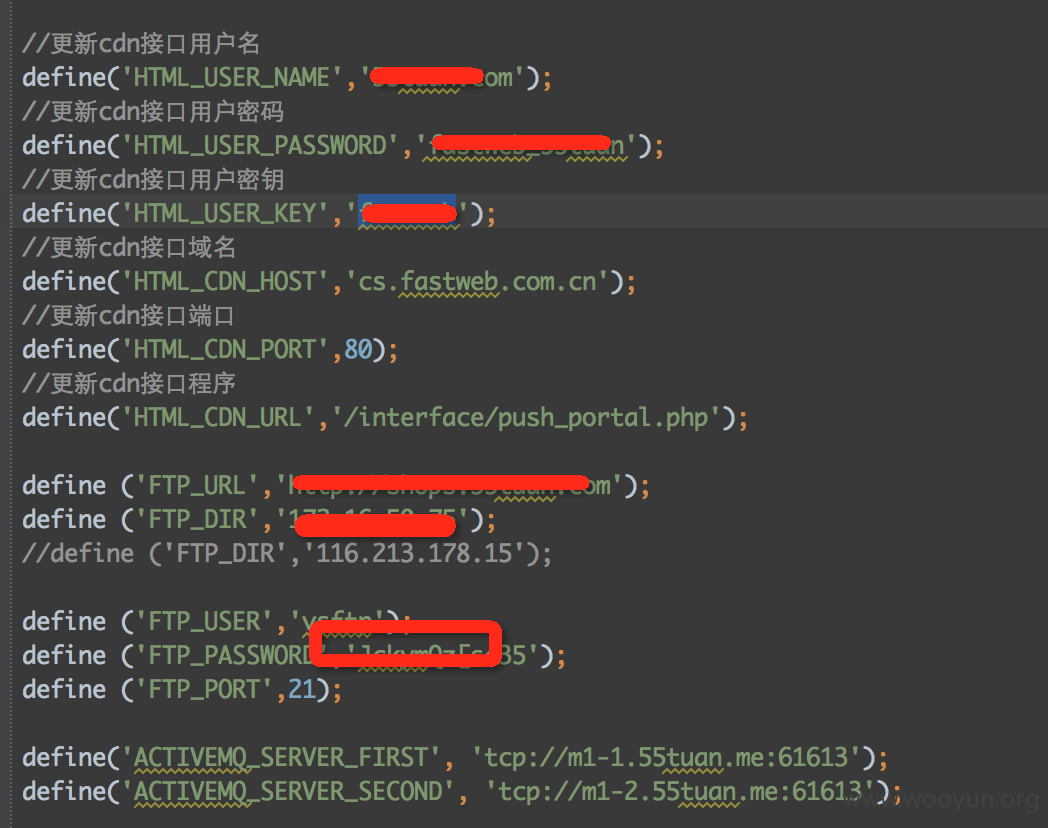
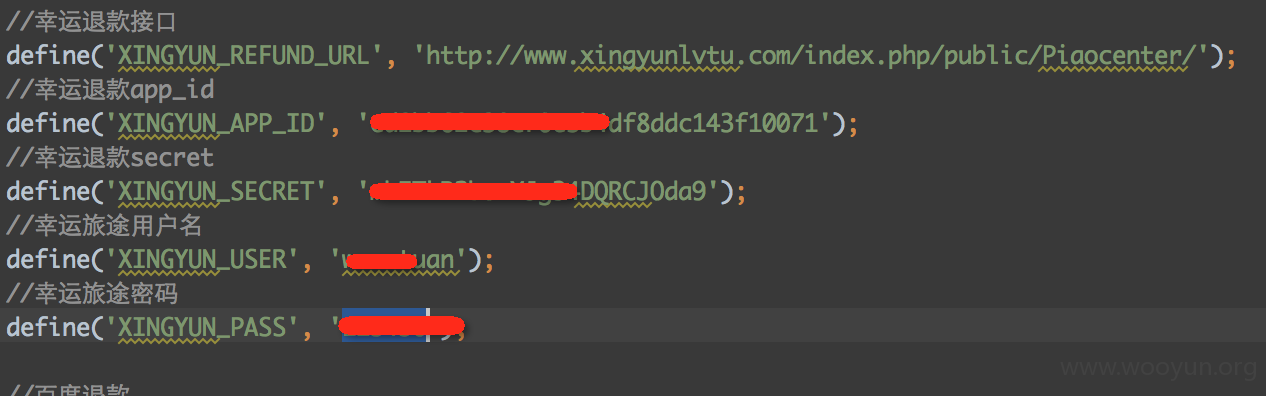
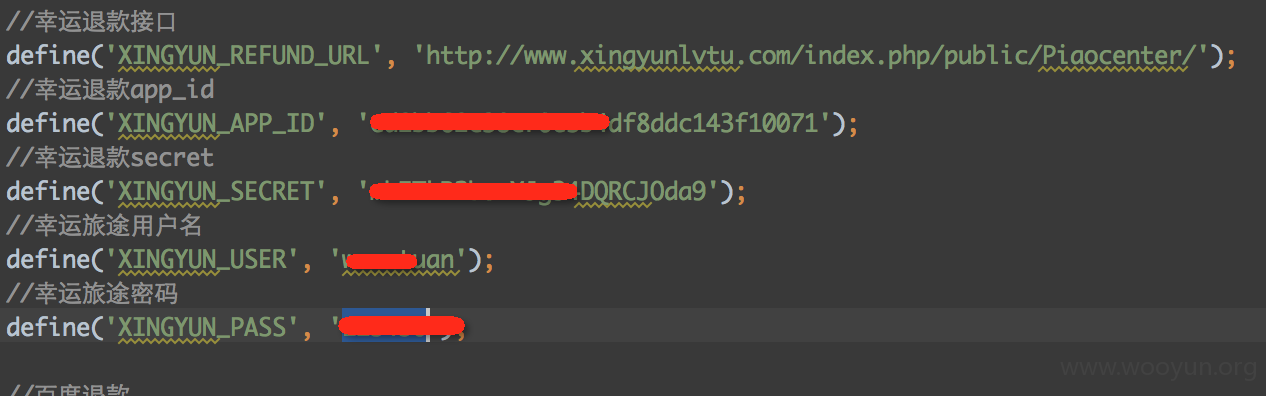
漏洞证明:
修复方案:
版权声明:转载请注明来源 啊L川@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:7
确认时间:2015-06-29 17:28
厂商回复:
.svn/.git隐藏目录的问题容易一犯再犯,而且由不同技术团队事隔多年之后重蹈覆辙,第一得靠自动化上线过滤这种隐藏目录,第二还是得靠Nginx配置统一屏蔽Web访问。多谢这位童鞋帮我们找到非生产环境里的这个漏洞!
最新状态:
暂无