漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0166853
漏洞标题:荆楚网某业务系统Getshell漏洞
相关厂商:荆楚网
漏洞作者: 艺术家
提交时间:2016-01-03 11:02
修复时间:2016-02-12 18:49
公开时间:2016-02-12 18:49
漏洞类型:命令执行
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-03: 细节已通知厂商并且等待厂商处理中
2016-01-05: 厂商已经确认,细节仅向厂商公开
2016-01-15: 细节向核心白帽子及相关领域专家公开
2016-01-25: 细节向普通白帽子公开
2016-02-04: 细节向实习白帽子公开
2016-02-12: 细节向公众公开
简要描述:
既然基本所有站都安了安全狗
详细说明:
漏洞证明:
漏洞点:
http://show.cnhubei.com/admin/registerMember.do
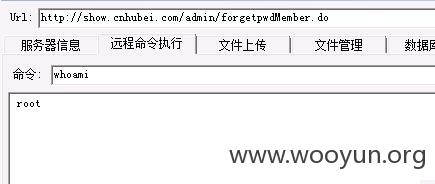
http://show.cnhubei.com/admin/forgetpwdMember.do
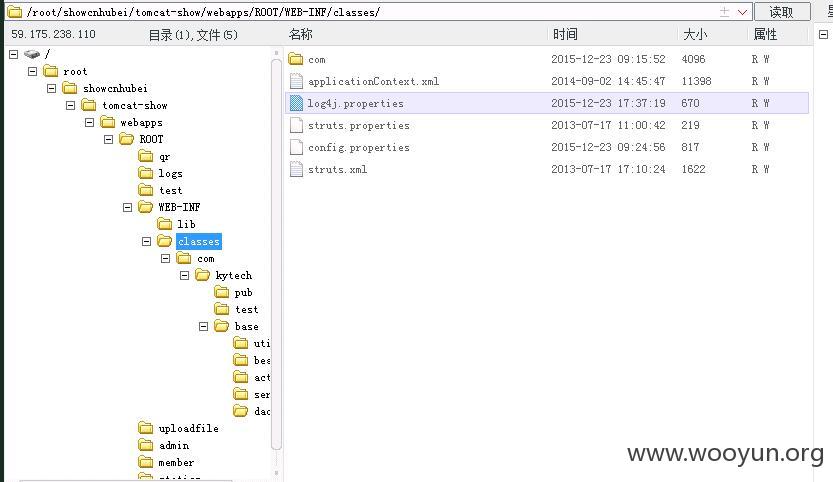
/root/showcnhubei/tomcat-show/webapps/ROOT/WEB-INF/classes/config.properties
直接在内网:
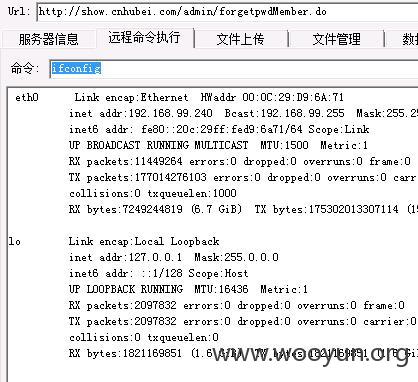
[/root/showcnhubei/tomcat-show/webapps/ROOT/]$ ifconfig
eth0 Link encap:Ethernet HWaddr 00:0C:29:D9:6A:71
inet addr:192.168.99.240 Bcast:192.168.99.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fed9:6a71/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:11464485 errors:0 dropped:0 overruns:0 frame:0
TX packets:177138974453 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:7250694794 (6.7 GiB) TX bytes:175426349404955 (159.5 TiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:2101937 errors:0 dropped:0 overruns:0 frame:0
TX packets:2101937 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:1823577246 (1.6 GiB) TX bytes:1823577246 (1.6 GiB)
简单看一下,不深入了,感觉不会有什么太多东西。
[/root/showcnhubei/tomcat-show/webapps/ROOT/]$ nmap -Pn 192.168.99.1/24 -p 80 -oN /tmp/xx.txt
Starting Nmap 5.51 ( http://nmap.org ) at 2016-01-02 15:53 CST
Nmap scan report for pfSense.localdomain (192.168.99.1)
Host is up (0.00035s latency).
PORT STATE SERVICE
80/tcp open http
MAC Address: 00:0C:29:72:D4:DC (VMware)
Nmap scan report for 192.168.99.85
Host is up (0.00040s latency).
PORT STATE SERVICE
80/tcp closed http
MAC Address: 00:0C:29:9A:60:78 (VMware)
Nmap scan report for productserver (192.168.99.240)
Host is up (0.000063s latency).
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 192.168.99.241
Host is up (0.00059s latency).
PORT STATE SERVICE
80/tcp closed http
MAC Address: 00:0C:29:56:63:58 (VMware)
Nmap scan report for 192.168.99.254
Host is up (0.00053s latency).
PORT STATE SERVICE
80/tcp open http
MAC Address: 00:50:56:60:1B:2E (VMware)
Nmap done: 256 IP addresses (5 hosts up) scanned in 15.46 seconds
修复方案:
把漏洞补了。
版权声明:转载请注明来源 艺术家@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:9
确认时间:2016-01-05 09:45
厂商回复:
感谢您的反馈,已通知研发修补漏洞。
最新状态:
暂无