漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-090335
漏洞标题:韵达快递某系统SQL注入,各种数据库再次侧漏(指哪补哪)~
相关厂商:韵达快递
漏洞作者: 小饼仔
提交时间:2015-01-06 18:37
修复时间:2015-02-20 18:38
公开时间:2015-02-20 18:38
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-01-06: 细节已通知厂商并且等待厂商处理中
2015-01-07: 厂商已经确认,细节仅向厂商公开
2015-01-17: 细节向核心白帽子及相关领域专家公开
2015-01-27: 细节向普通白帽子公开
2015-02-06: 细节向实习白帽子公开
2015-02-20: 细节向公众公开
简要描述:
指哪补哪,韵达你真的修复了吗?
详细说明:
点进去看了下,有个页面
http://car.yundasys.com:81/yd_khd/khd_add.php
未授权访问,可以上传任意文件,厂商的确修复了,跳转到了登陆页面
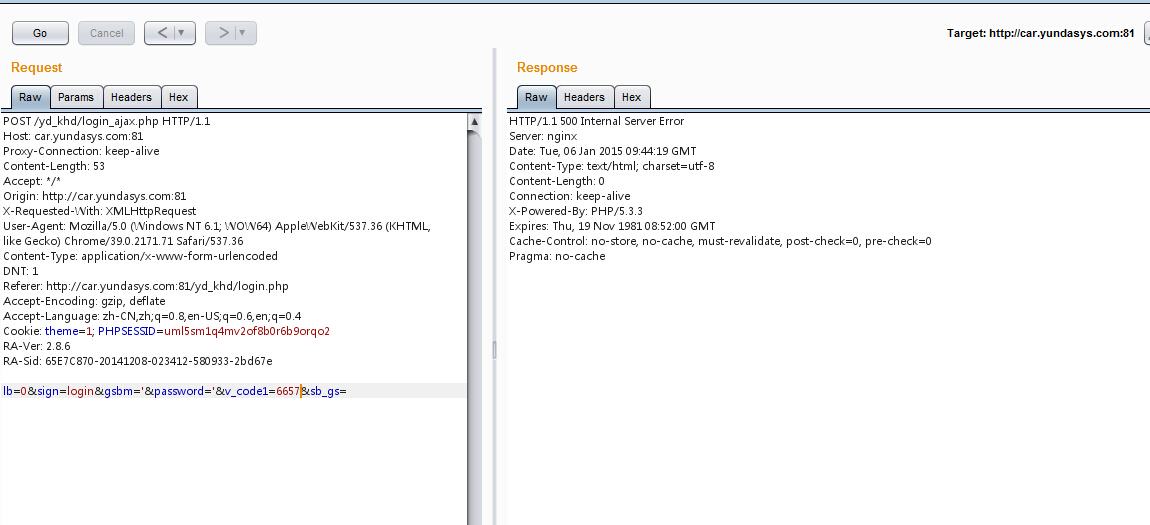
看到登陆处,习惯性的输入了单引号,点登陆,没反应,抓包看了下,500错误,估计有戏
然后随便输入用户名和密码,重复提交了几次,都提示用户名或密码错误,验证码可以重复使用
post请求
漏洞证明:
丢到sqlmap里
好了,危害什么的,看 WooYun: 韵达某处任意文件上传导致各种数据库侧漏(疑似各种韵达系统数据库) 就知道了,就不深入了
修复方案:
别指哪补哪!
版权声明:转载请注明来源 小饼仔@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-01-07 09:42
厂商回复:
已做修复,谢谢
最新状态:
暂无