注入点:
https://www.anpingdai.com/index.php?s=/Home/About/infoDetails/category_id/6/id/12*.html 放入sqlmap跑一下吧
基本集合的所有的注入
看表
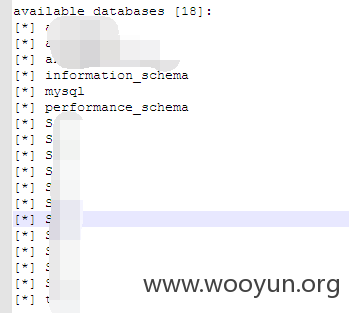
后台管理员:
手动试一下后台地址:
md5解密登录一个
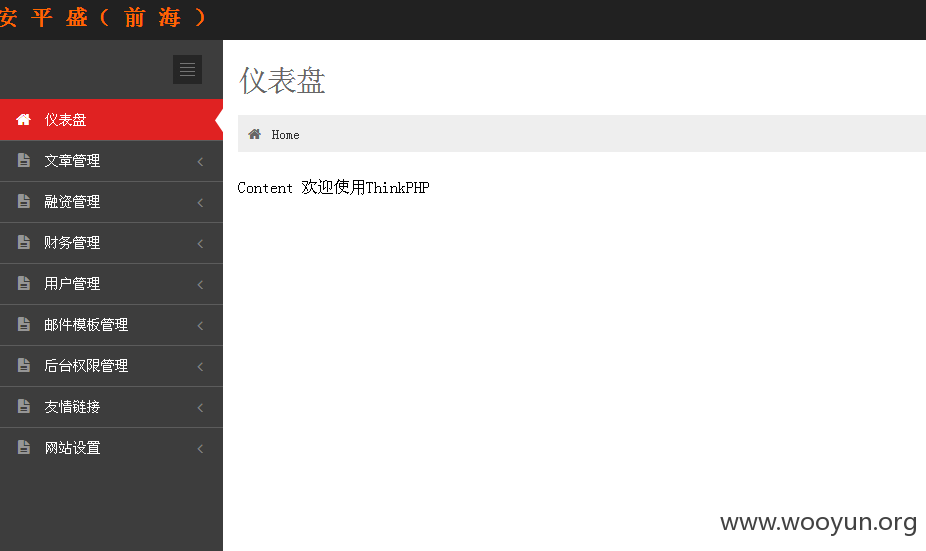
注入点:
https://www.anpingdai.com/index.php?s=/Home/About/infoDetails/category_id/6/id/12*.html 放入sqlmap跑一下吧
基本集合的所有的注入
看表

后台管理员:
手动试一下后台地址:
md5解密登录一个





