第一处:
http://**.**.**.**:8083/holidays/hotel_detail.asp?route=mfm&seq=30
第二处:
http://**.**.**.**:8083/about/news_articles.asp?id=21
第三处:
http://**.**.**.**:8083/tips/tips_intro.asp?unqid=1
第4处:
http://**.**.**.**:8083/airshopping/eshopping_intro.asp?item=51002922
第5处:
是post注入
还是可以union的
第1处:
post注入
======================================================
第2处:
还是post注入
=============================================================
第3处:
get型注入
http://**.**.**.**:8084/tips/tips_intro.asp?unqid=23
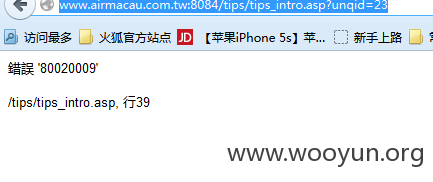
开跑



