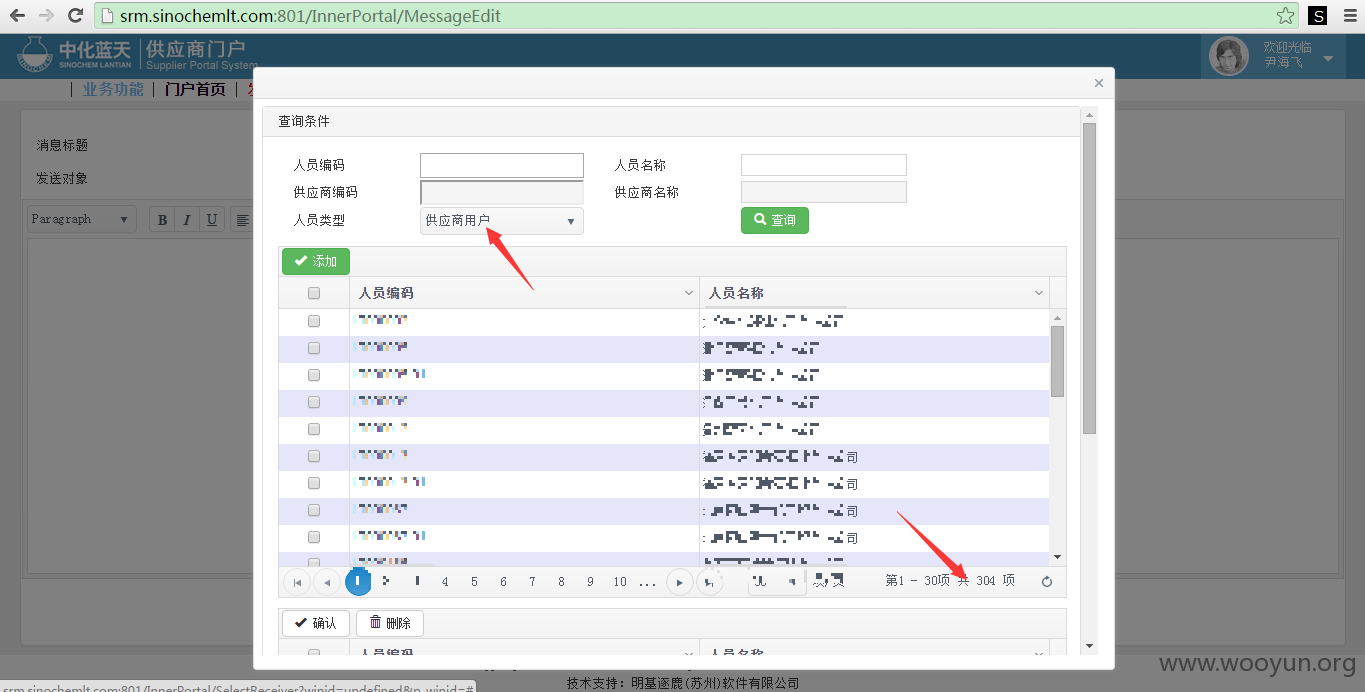
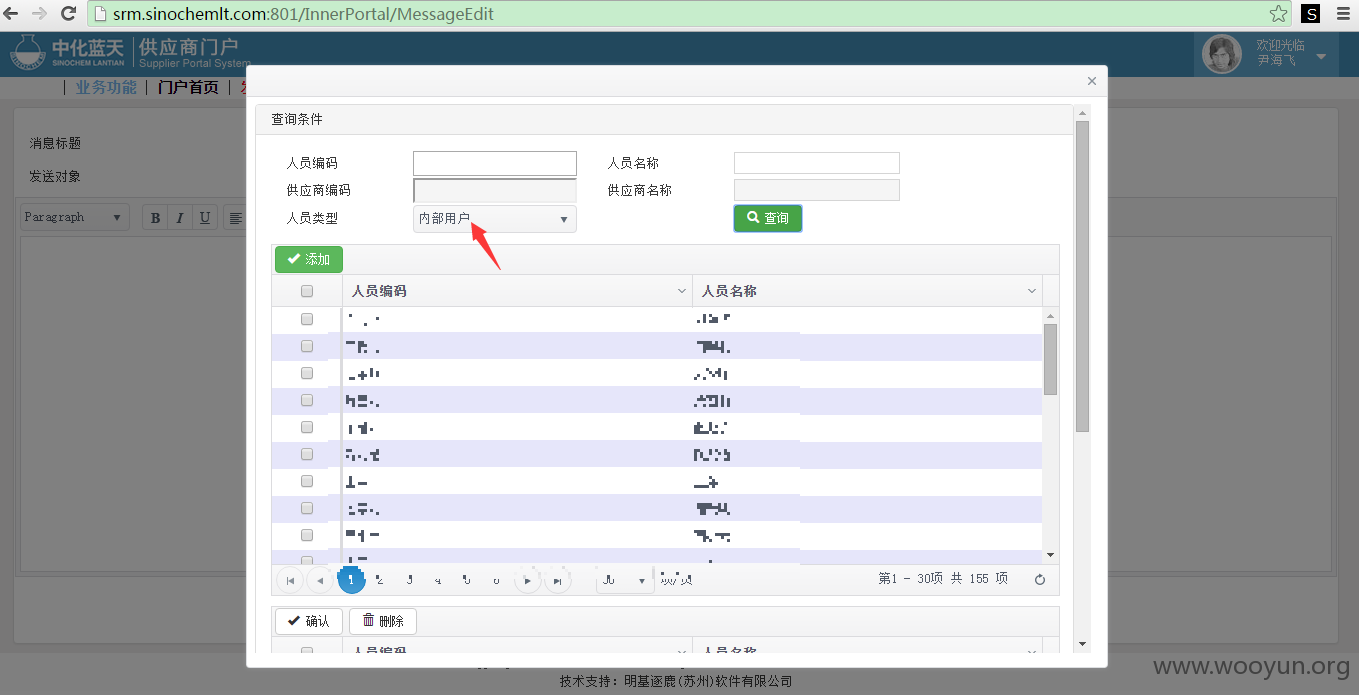
中化蓝天供应商门户SQL注入
注入点:http://**.**.**.**:801/OutPortal/OutPortalDetailView?messageid=86
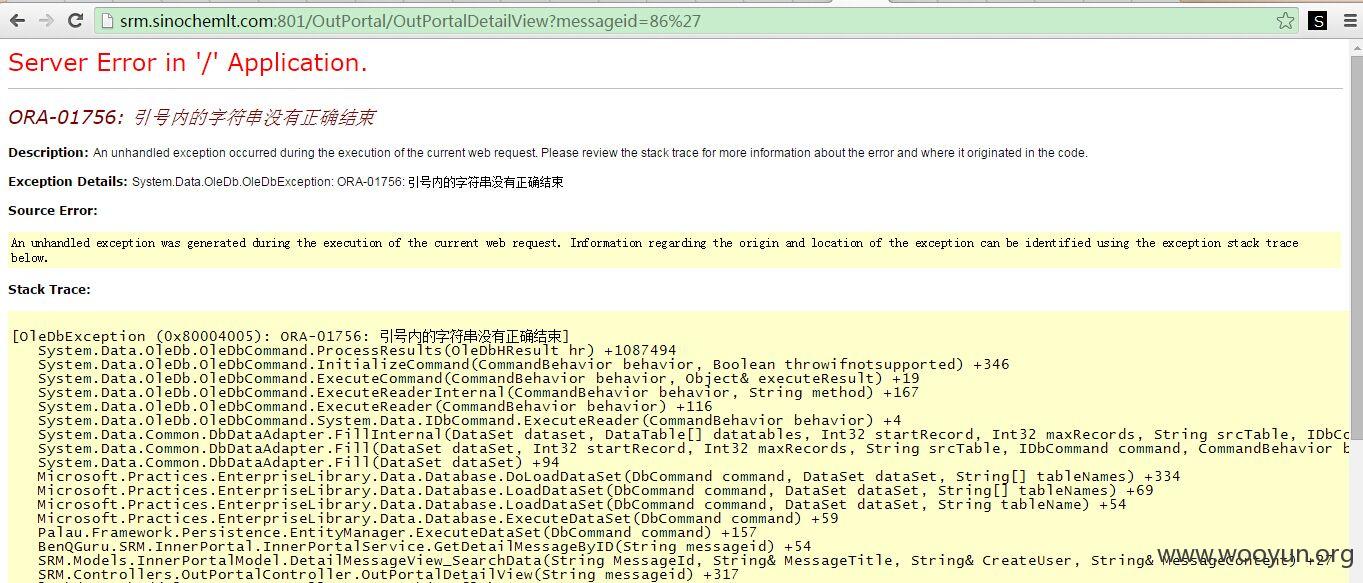
oracle管理员权限
数据库信息
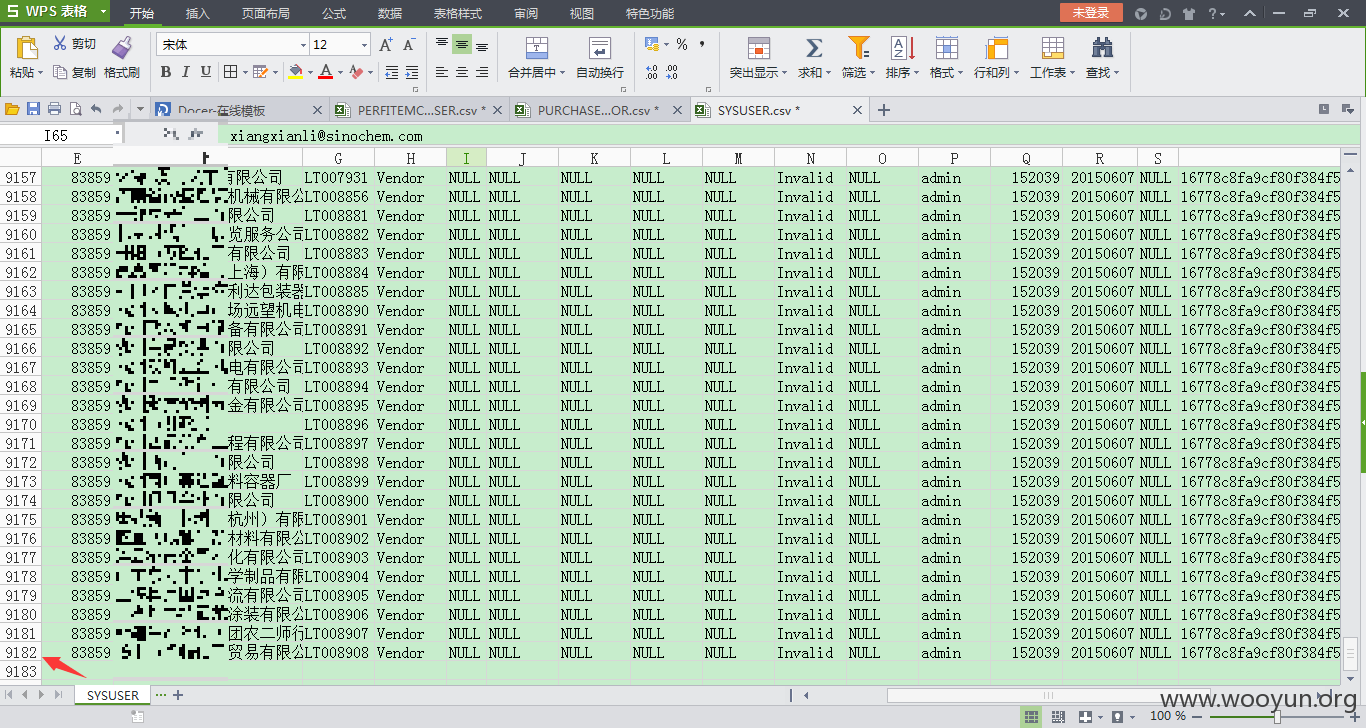
当前数据库中的数据表
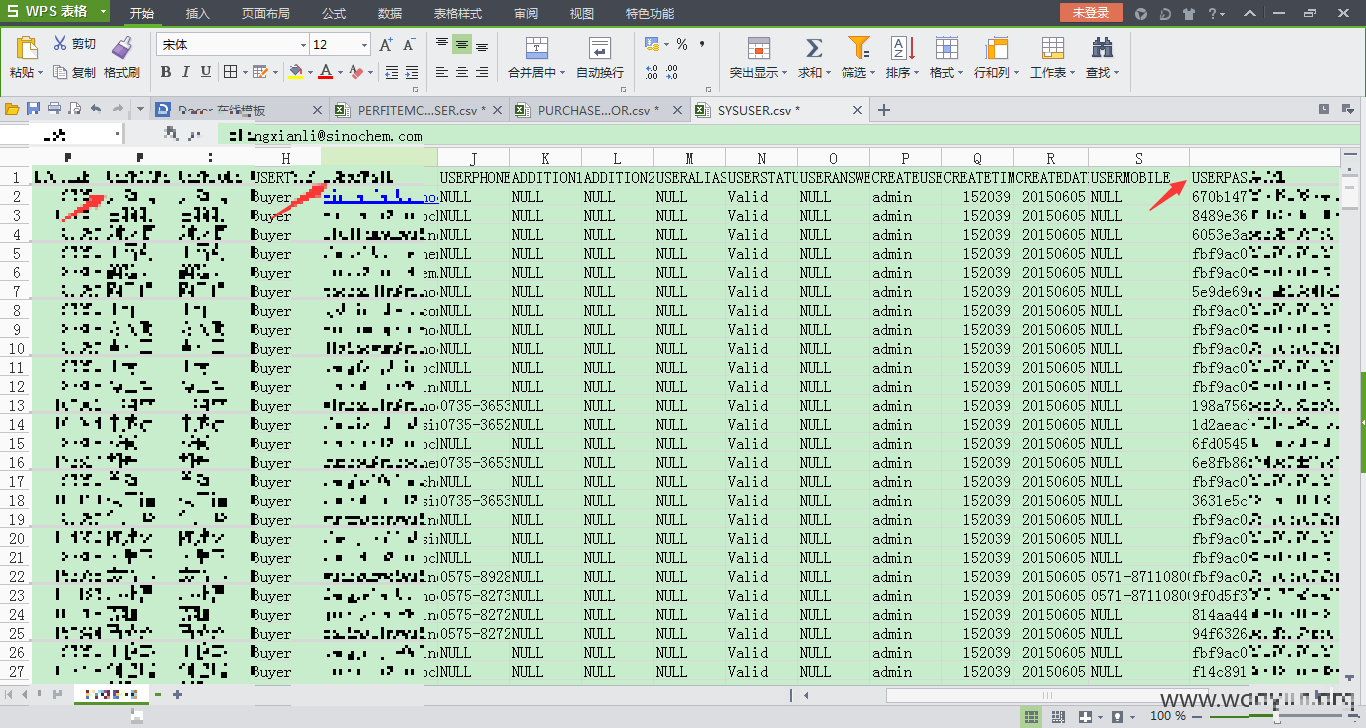
sysuser表中的部分数据
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-11-12 08:37
厂商回复:
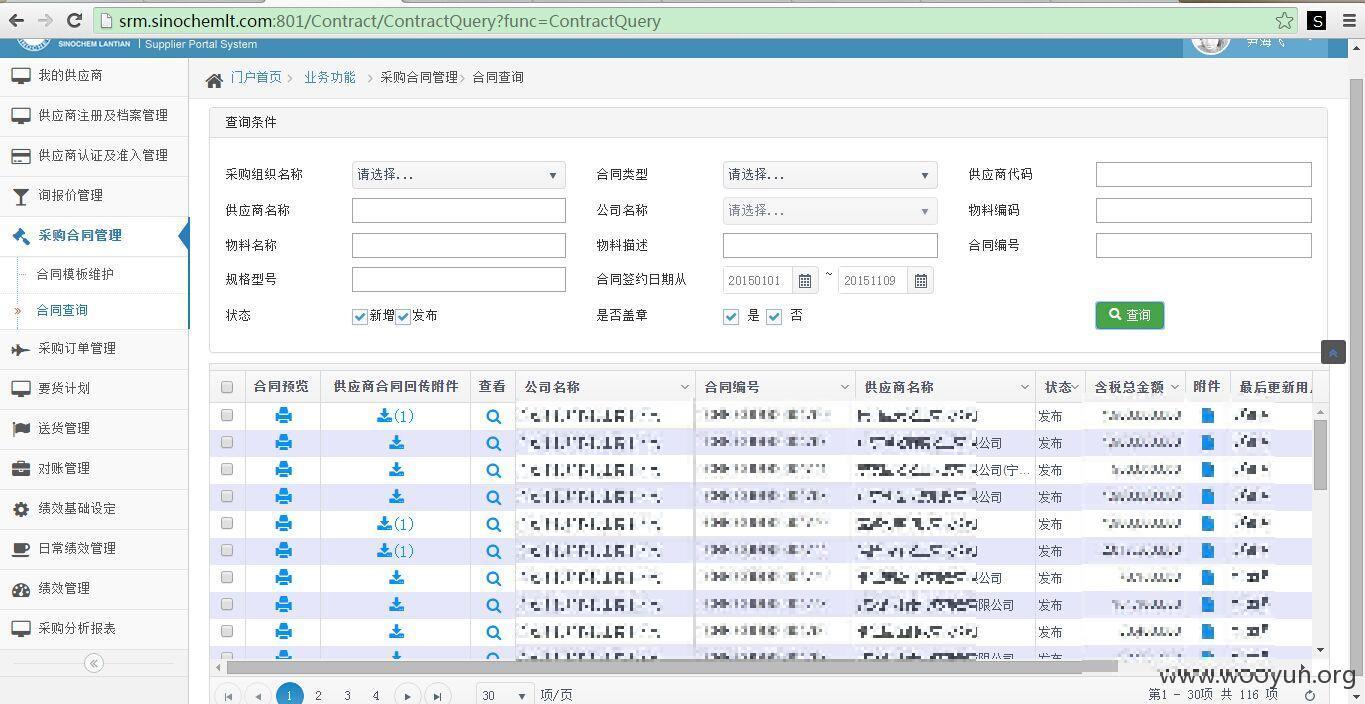
可导致客户信息、重要业务数据泄露,非常严重。我们尽快修复。
最新状态:
2015-11-20:@路人甲 系统供应商已修复注入漏洞,能否帮忙确认?
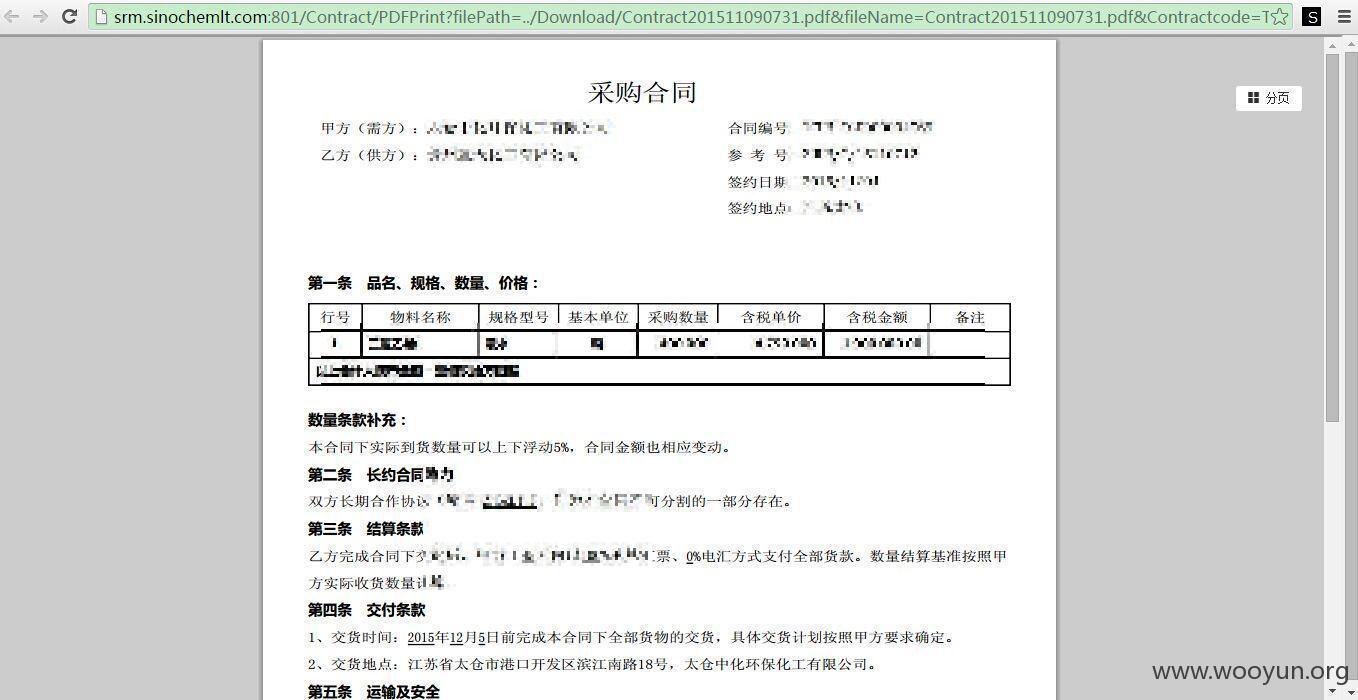
2015-11-26:@乌云 漏洞已修复,可以公开。但能否隐藏人员姓名、手机、邮箱、供应商名称、合同金额?这些都是商业敏感信息。
2015-12-17:已修复。