#1 漏洞描述
注入漏洞1:
http://**.**.**.**/index.php?rSite/Index&sysPageId=141202171042413'
注入漏洞2:http://**.**.**.**/upload/download.php?id=123'
# 注入漏洞1利用
~ phpmyadmin
http://**.**.**.**/phpmyadmin
~ 进入后台
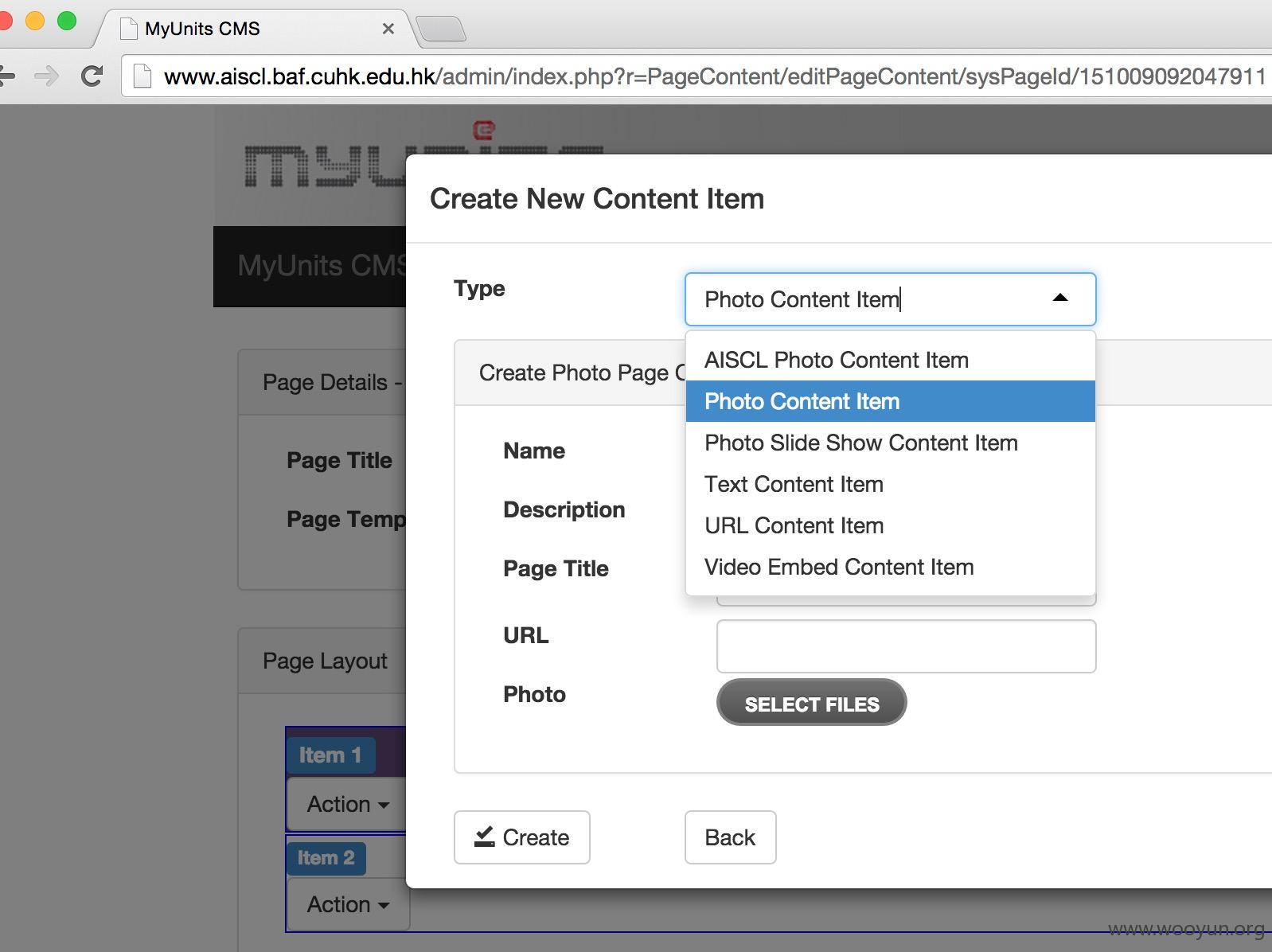
系统权限:
# 注入漏洞2利用
这个注入漏洞root权限起来的,可以直接into outfile 写入shell
shell it:
http://**.**.**.**/upload/123.txt
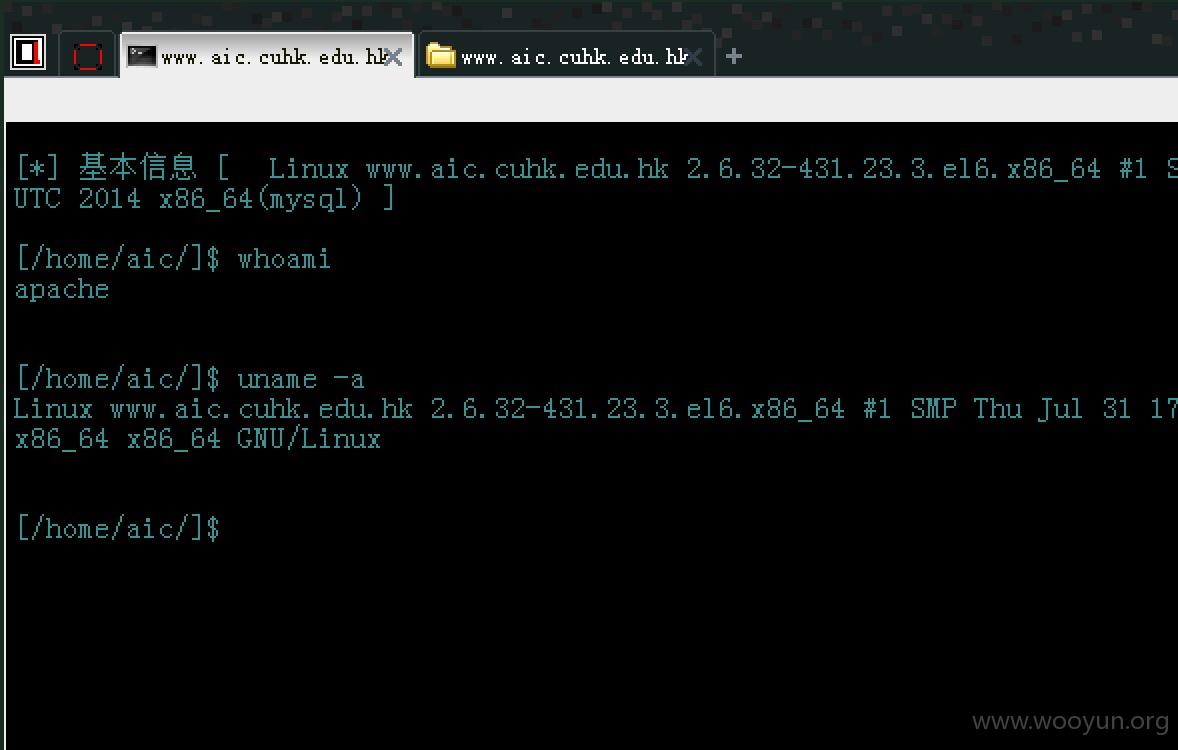
很多数据受影响:




