先说说 github上面的信息泄露吧
https://github.com/jiangkunwei/dc/blob/9778fb5f182a0dde6f36cf95bdfc8279eb74ec88/config/config.php
支持外联哦~
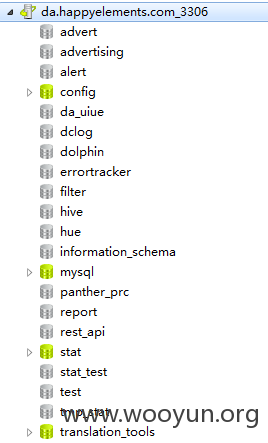
https://github.com/gaitian/project/blob/97d02946eab3e3f18aeef6f97702eb9c0295748e/trunk/protected/config/params.php
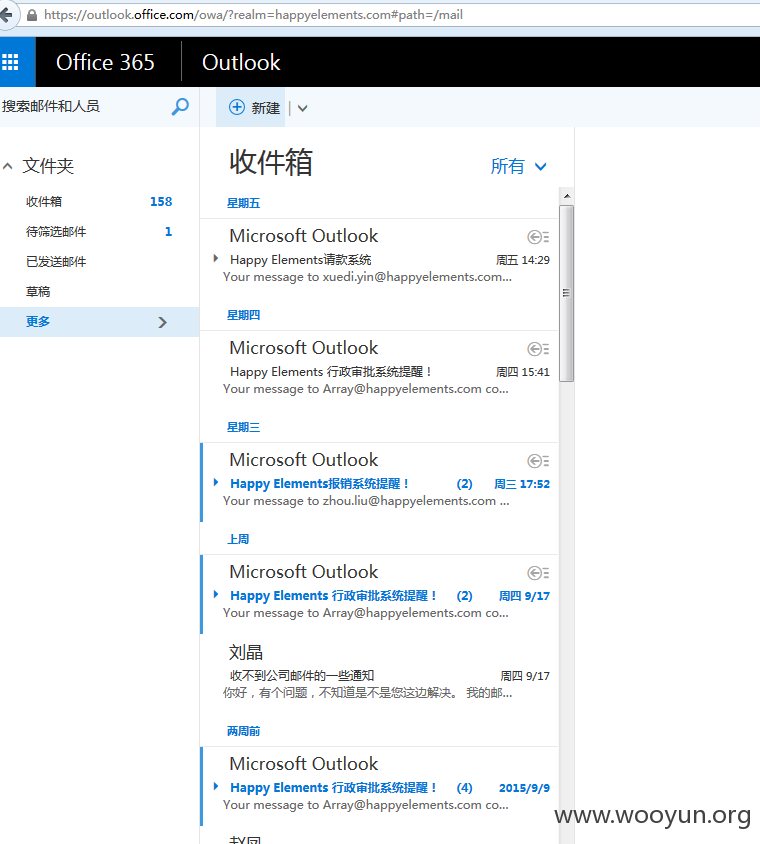
再说个注入问题
http://fansclub.happyelements.com:80/fans/qa.php
这个是开心消消乐APP里面的链接 是客服里面的常见问题
Client-IP 存在注入哦
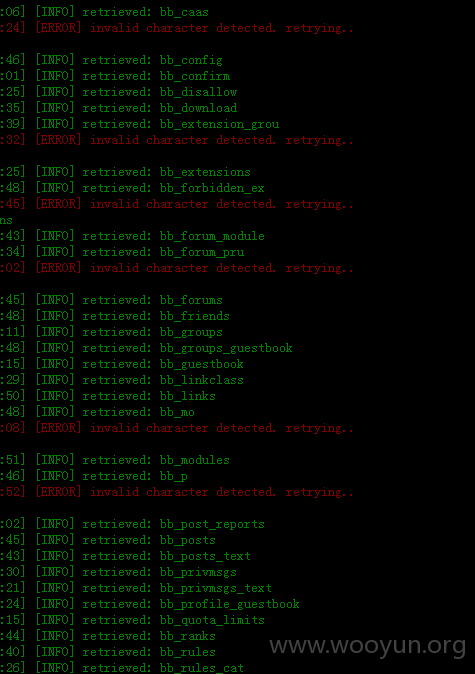
其中 还影响 http://ff.happyelements.com/index.php/admin/nodes admin 1234qwer!
![)1[SYR]G7P)Z%I8MCQ[QFEK.png](http://wimg.zone.ci/upload/201509/272248443a4195f3b480125eecef8b331b79fced.png)
来说说getshell
http://admin.happyelements.net/blog/ 是wp模版 存在弱口令 admin 123456
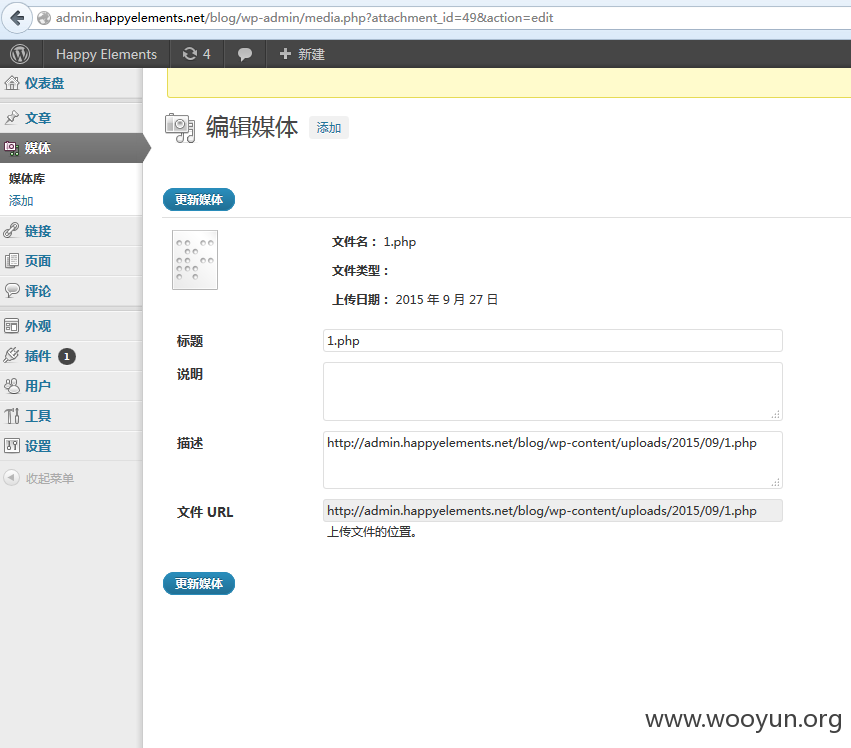
通过上传webshell获得权限
http://admin.happyelements.net/blog/wp-content/uploads/2015/09/0.php 密码a
![C2BFZRB}IBLB@@M3C]_T[MC.png](http://wimg.zone.ci/upload/201509/27225009c70cf211a20595959ad413700ac65f46.png)
在这 翻到一些数据哦
这个基本上是管理员通用的密码咯
还发现了ldap
("odbc:Driver=FreeTDS;Server=10.130.150.171;Port=1433;Database=middata2015;Tds_version=7.0;Uid=sa;Pwd=sa;");
又发现帐号~~登陆一下试试
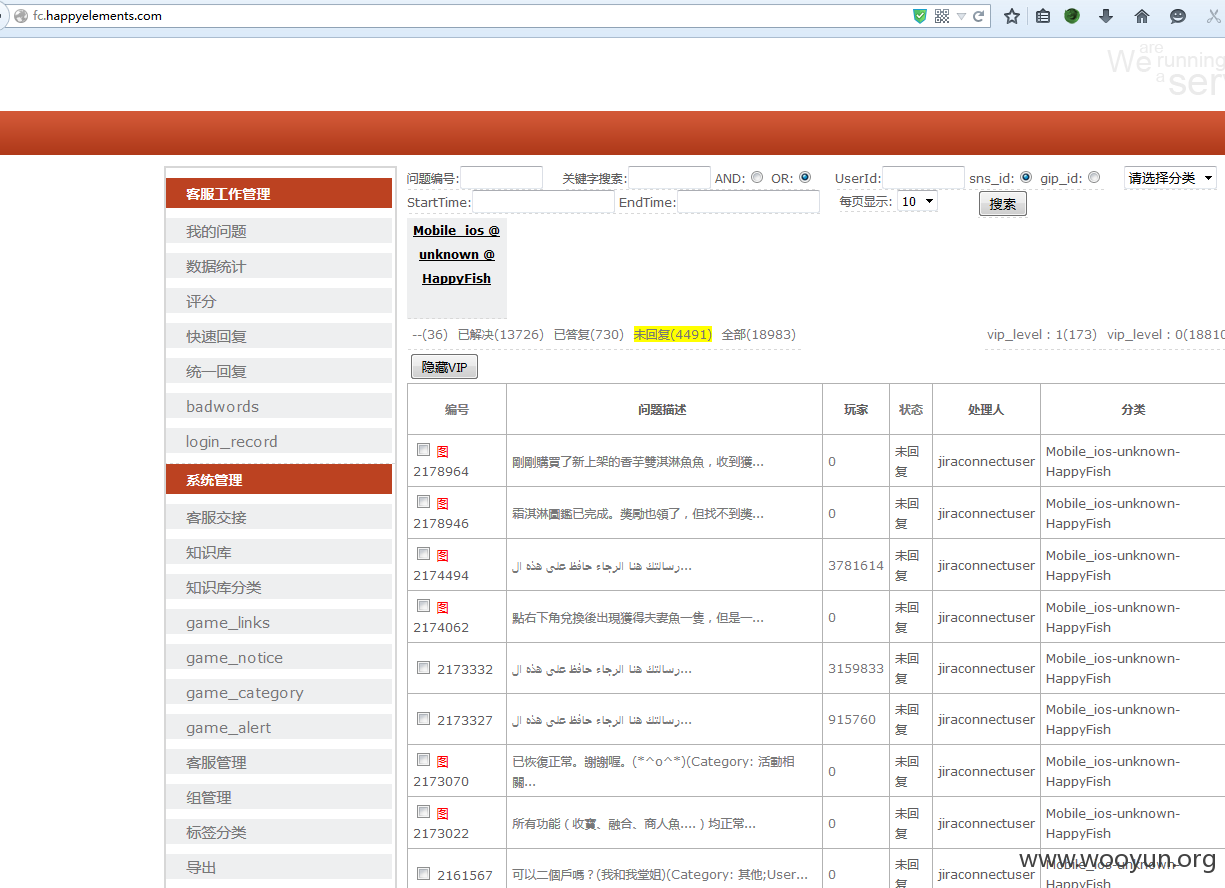
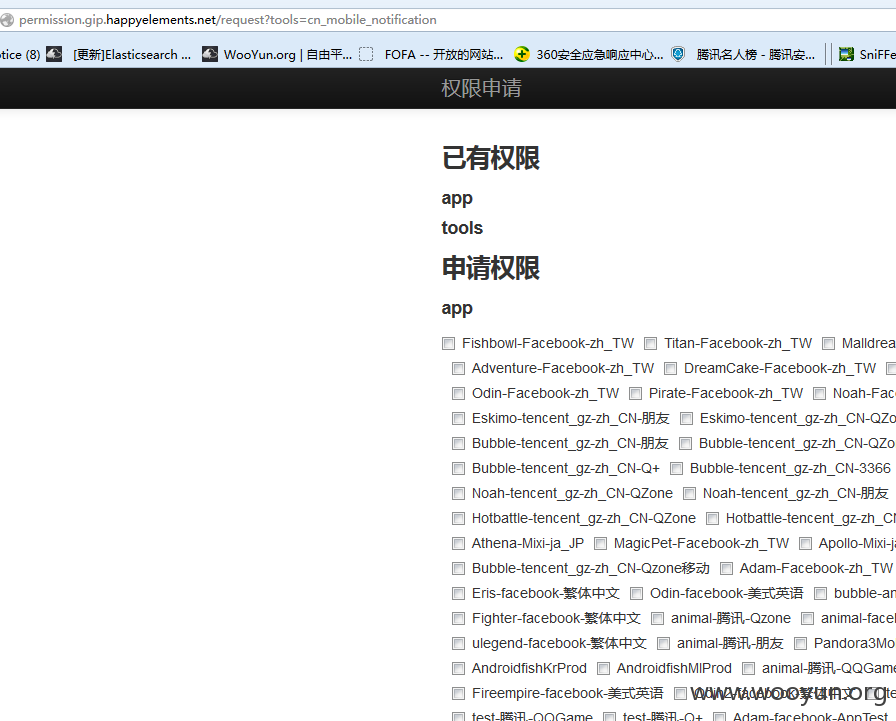
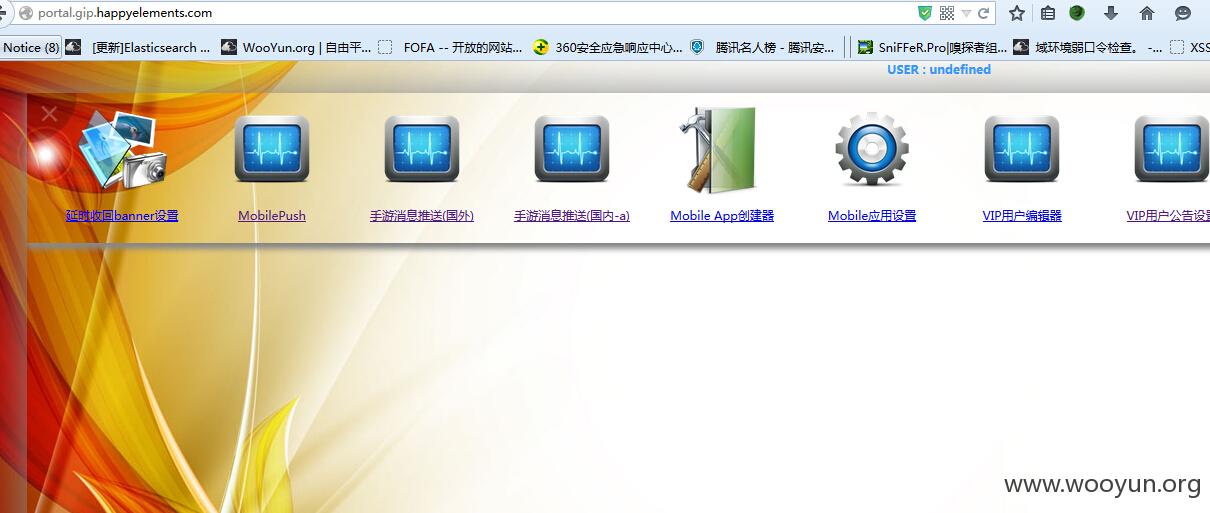
![WOCUB]VRO0Z9MA{H[F@DB{B.jpg](http://wimg.zone.ci/upload/201509/27225220e5e9e29262c78ce835ff78c7a12c497d.jpg)
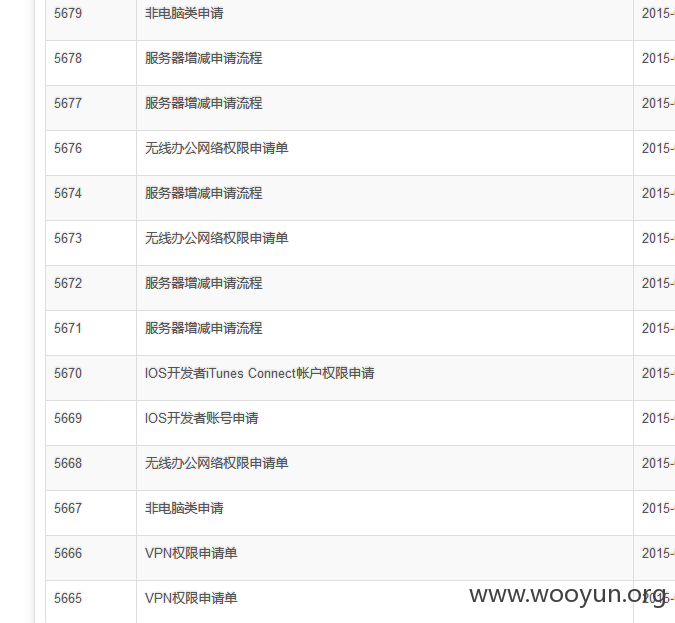
第二个shell
http://fc.happyelements.com/
是客服系统
存在moadmin.php 之前就被爆两个命令执行
![6QVAH18SP$`]8D%{0$EZ3AY.png](http://wimg.zone.ci/upload/201509/27225322b97d7584de96d473400b4db22af5a835.png)
![%%AZ]`(Y[77YL$XIQO9@2@O.png](http://wimg.zone.ci/upload/201509/2722533721c7e5dca91a509734e5276b865719de.png)
成功shell
下面是一些数据哦~
support_user 可以登录的 我就不帖图片了~






![)1[SYR]G7P)Z%I8MCQ[QFEK.png](http://wimg.zone.ci/upload/201509/272248443a4195f3b480125eecef8b331b79fced.png)

![C2BFZRB}IBLB@@M3C]_T[MC.png](http://wimg.zone.ci/upload/201509/27225009c70cf211a20595959ad413700ac65f46.png)



![WOCUB]VRO0Z9MA{H[F@DB{B.jpg](http://wimg.zone.ci/upload/201509/27225220e5e9e29262c78ce835ff78c7a12c497d.jpg)

![6QVAH18SP$`]8D%{0$EZ3AY.png](http://wimg.zone.ci/upload/201509/27225322b97d7584de96d473400b4db22af5a835.png)
![%%AZ]`(Y[77YL$XIQO9@2@O.png](http://wimg.zone.ci/upload/201509/2722533721c7e5dca91a509734e5276b865719de.png)